| Subtotal | $0.00 |
| Subtotal | $0.00 |
|
“Dear Hosting Account 'cPanel_username' Owner,
This is an automated alert to inform you that we have detected a malicious attempt to access your account via http or ftp on our server 'hostname_of_the_server'. Our security systems have blocked the upload of malicious file to the server and put it to the quarantine. Your website is safe now, but it is important you undertake the following precautions. 1. Immediately scan your PC for viruses and malware. We recommend the anti-virus programs which free editions are available for most operating systems for this purpose. 2. Make sure that you use strong, hard-to-guess passwords on your account and applications. Do not use the same password for different applications. To remember more difficult passwords, we recommend you use the password managers such as LastPass or RoboForm. 3. Update all third party scripts to the latest versions (e.g. Joomla, WordPress, Magento or any other CMS). Remove every script, gadget, feature, function, and code snippet which has poor security vulnerability report. 4. Use .htaccess or cPanel > Deny IP to block the hacker's HTTP access to your site. If you identified the hacker's IP address, one site where you can look it up to get more information about this IP is http://whois.domaintools.com/ . 5. Change your cPanel/ftp passwords. We have put the following content into quarantine as we believe it contains viruses or other malicious code. If you feel this has been in error and your file is false-positive (innocent), please reach out to our Hosting department via Live Chat or email and we will be happy to assist: '[PHP Obfuscation Exploit [P0395]]': /home/cPanel_username/public_html/Songs/wp-content/themes/.cache.php '[PHP Obfuscation Exploit [P0395]]': /home/cPanel_username/public_html/wp-content/themes/.cache.php '[PHP Obfuscation Exploit [P0395]]': /home/cPanel_username/public_html/wp-content/themes/.cache.php '[PHP Obfuscation Exploit [P0395]]': /home/cPanel_username/public_html/wp-content/themes/.cache.php '[PHP Obfuscation Exploit [P0395]]': /home/cPanel_username/public_html/wp-content/themes/.cache.php” |
Scan your PC for viruses and malware
Scan your hosting account with Virus Scanner
Update your CMS along with all the modules/plugins
Have a fresh backup of your files
Scan your PC for viruses and malware
The first thing to check is whether your personal computer contains any malware that might have triggered the warning email message. Make sure that you scan your local computer and clean up any malicious software.
To check which anti-virus software is popular nowadays, please do not hesitate to review this article from our blog regarding the matter.
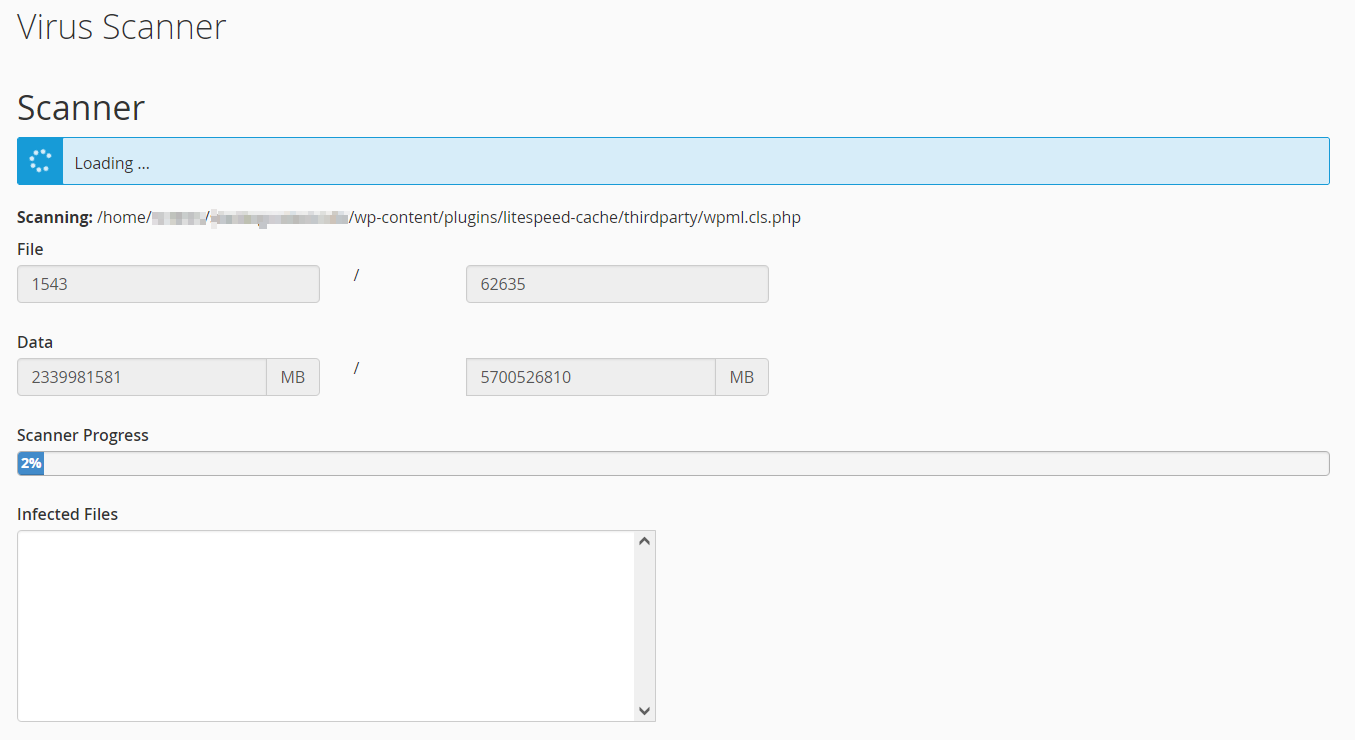
Scan your hosting account with Virus Scanner
|
----------- SCAN REPORT -----------
TimeStamp: Date (/usr/sbin/cxs --nobayes --clamdsock /var/clamd --defapache nobody --doptions Mv --exploitscan --nofallback --filemax 50000 --html --ignore /etc/cxs/cxs.ignore --options mMOLfSGchexdnwZDRu --qoptions Mv --report /home/cPanel_username/scanreport-support-date-h12m.txt --sizemax 500000 --ssl --summary --sversionscan --timemax 30 --user support --virusscan --xtra /etc/cxs/cxs.xtra) Scanning /home/cPanel_username: '/home/cPanel_username/access-logs' # Symlink to [/usr/local/apache/domlogs/support] '/home/cPanel_username/public_html/process.txt' # ClamAV detected virus = [Eicar-Test-Signature] ----------- SCAN SUMMARY ----------- Scanned directories: 171 Scanned files: 13996 Ignored items: 33 Suspicious matches: 2 Viruses found: 1 Fingerprint matches: 0 Data scanned: 218.37 MB Scan time/item: 0.008 sec Scan time: 107.945 sec |
As a precautionary measure, it is highly recommended to update passwords of all the services related to your hosting package as well. Such services include:
Check how to reset the cPanel password here.
As an improved security measure, it is recommended to set up 2FA for the cPanel account.
If you use Reseller Hosting with us, you can initiate a password reset for your main cPanel account, and your WHM password will be updated automatically as well.
To reset the root password for a VPS server, refer to the following tutorial.
Changing the cPanel account password will also update the password for your main FTP account. However, it is necessary to make sure that passwords for all additional FTP accounts are updated as well. In order to change the password for an additional FTP account, you need to do the following:
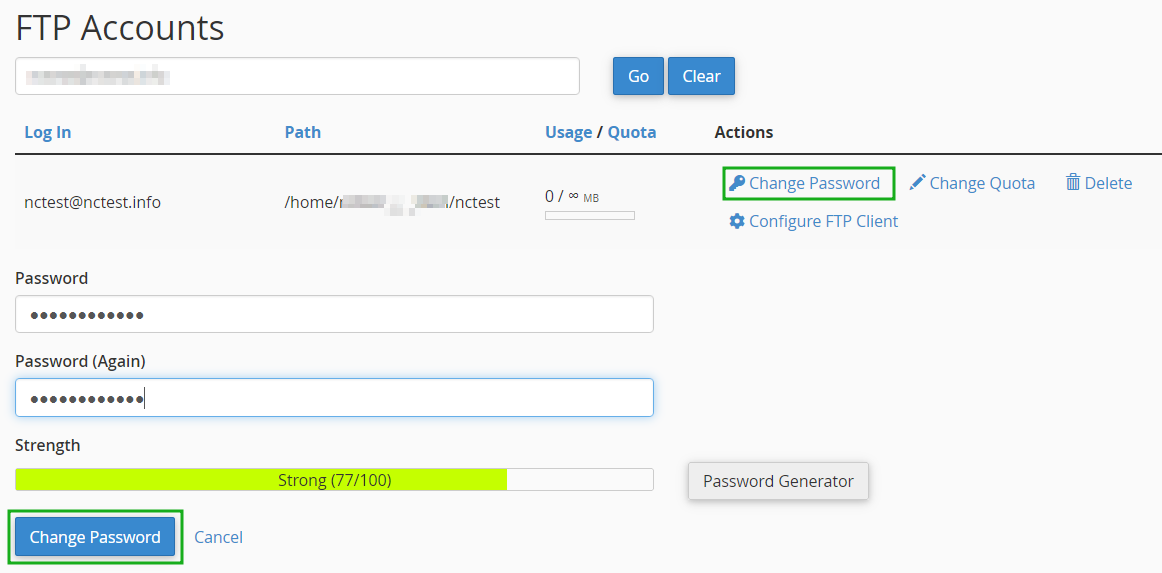
You can find some useful tutorials on how to update Admin passwords for Wordpress, Joomla, Prestashop and WHMCS as examples below:
How to reset WordPress Admin password
How to reset Joomla Admin password
How to reset Prestashop Admin password
How to reset WHMCS Admin password
Make sure that you use strong passwords with special characters in order to avoid unauthorized access to your hosting web space in the future. We recommend to use Password Generators like this one in order to create a complicated, long and reliable password.
For more information on complicated passwords, visit the following link.
The next step is making sure that passwords for all the existing databases are updated and secure as well. This can be done from cPanel > MySQL Databases menu easily.
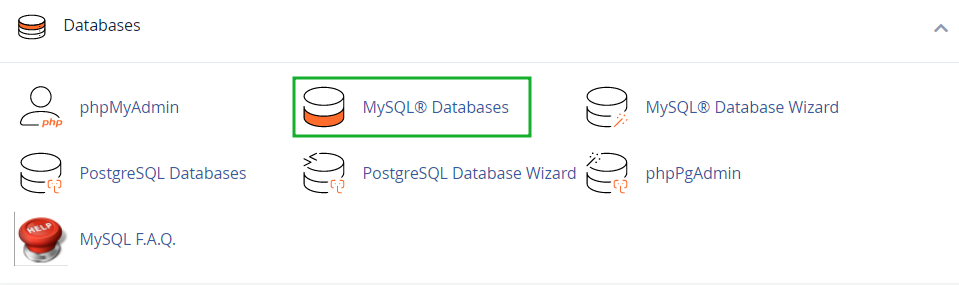
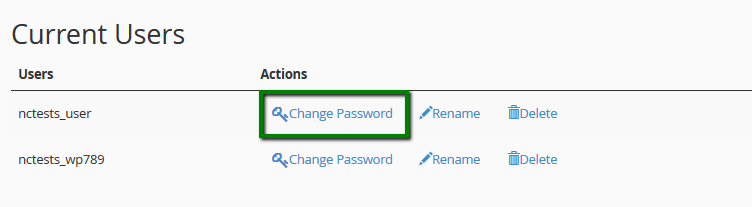
Update your CMS along with all the modules/plugins
The next measure is to make sure you are running the most recent version of a CMS and modules/plugins installed for it. It is important to keep your software up-to-date as the newest version contains various security implementations and fixes that helps to avoid security breaches.
In case your CMS was installed using our Softaculous script installer, it is possible to update it in a few clicks right from the Softaculous interface, check the following tutorial for more details.
If you are using one of CMS scripts available in Softaculous, but initial installation was performed in a different way, you can import the installation to Softaculous in order to update it easily then. For more details on how to import installation into Softaculous, check the following tutorial.
If your website is based on a custom and manually developed script, it is recommended to contact a web developer in order to implement additional security features.
Have a fresh backup of your files
Once all the measures are taken, make sure to create an up-to-date backup of your files. This can be easily done by means of an in-built backup tool in cPanel. For more details, feel free to check the following tutorial. You may also wish to configure automatic backup creation in cPanel.
That's it!
Need any help? Contact our HelpDesk
Need help? We're always here for you.