| Subtotal | $0.00 |
| Subtotal | $0.00 |
Nowadays, when almost everyone embraces HTTPS, a lot of fraud attempts which can lead to certificate mis-issuances may occur.
To prevent this, the CAB Forum with assistance of IETF found a solution - CAA record.
On February 22nd, 2017, CAA checks were made mandatory due to the CAB ballot. More details can be found here .
Thus now, before issuing a certificate for some domain, CAs have to check this domain for any CAA records present, and decline the issuance if a CAA record is set up with another CA preference. However, if there is no CAA record set up, they are still allowed to issue one.
Now we can see that reasons behind using a CAA record can be the following:
- You want to limit your domain to be issued a certificate only by your trusted certificate authorities.
- You want a Certificate Authority to implement additional checks to reduce the risk of unintended certificate mis-issue.
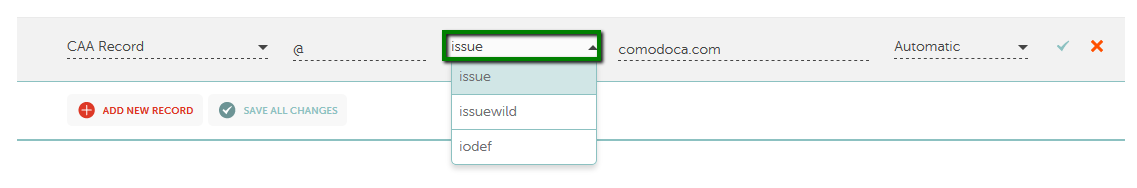
There are some types of CAA records with different parameters which have their own different purposes. They are described below:
example.com. IN CAA 0 issue "comodoca.com"
The CAA record set up above allows the Comodo CA (now Sectigo CA) to be an issuer of certificates for example.com.
Please note that a CAA record with no CA specified under the ‘issue’ parameter will restrict certificate issuance for the domain name in question: paragraph 5.2
Also, keep in mind that setting up one CA in the preferred by you format may lead to a rejected certificate issuance attempt from another one.
example.com. IN CAA 0 issuewild "comodoca.com"
This record above pretty much allows the same, but it should be used when a wildcard certificate is going to be issued for the example.com domain.
example.com. IN CAA 0 iodef "mailto:admin@example.com"
example.com. IN CAA 0 iodef "https://admin.example.com"
The ‘iodef’ record is the record which defines the way domain holder will be notified in case of any issuance policy violation spotted by Certificate Issuer.
In order to set up the desired CAA Record you should check if your DNS provider allows CAA Record implementation. This link (https://sslmate.com/caa/support) can be helpful.
If you use Cloudflare, CAA records can be set up there as well. You can find the guide at https://support.cloudflare.com/hc/en-us/articles/115000310792-Configuring-CAA-Records-
This tool might be used to generate the CAA record.
Additional information about how CAA treats different types of domain pointing can be found here.
Notes:
How to set up the CAA for the domain using Namecheap Basic/FreeDNS/PremiumDNS
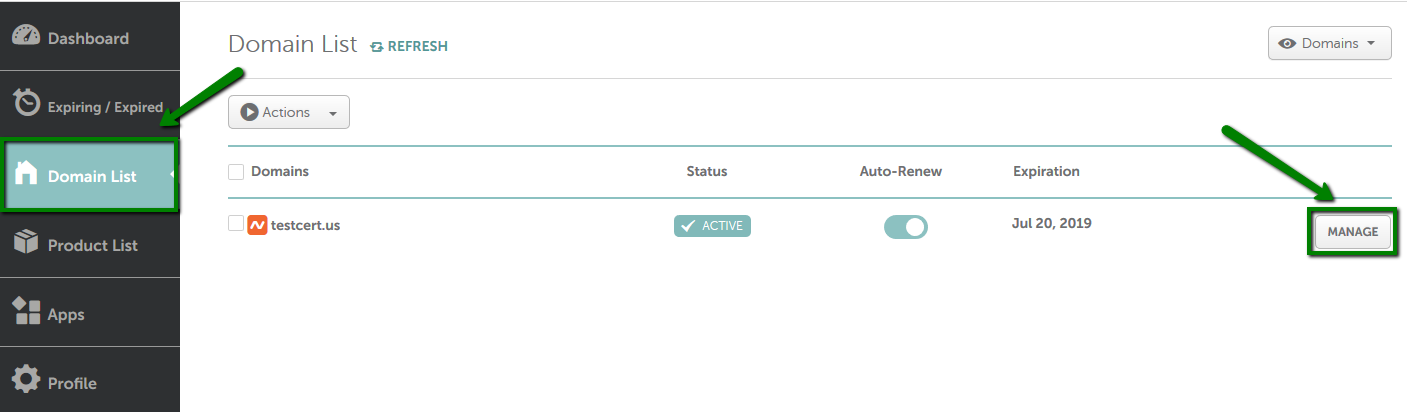
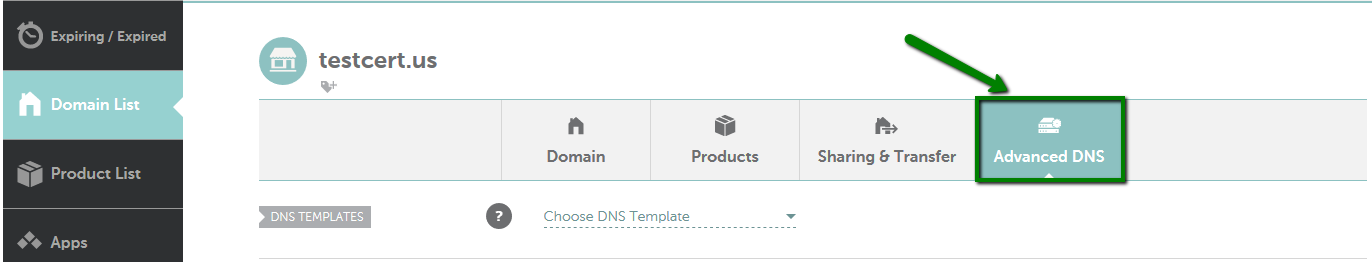
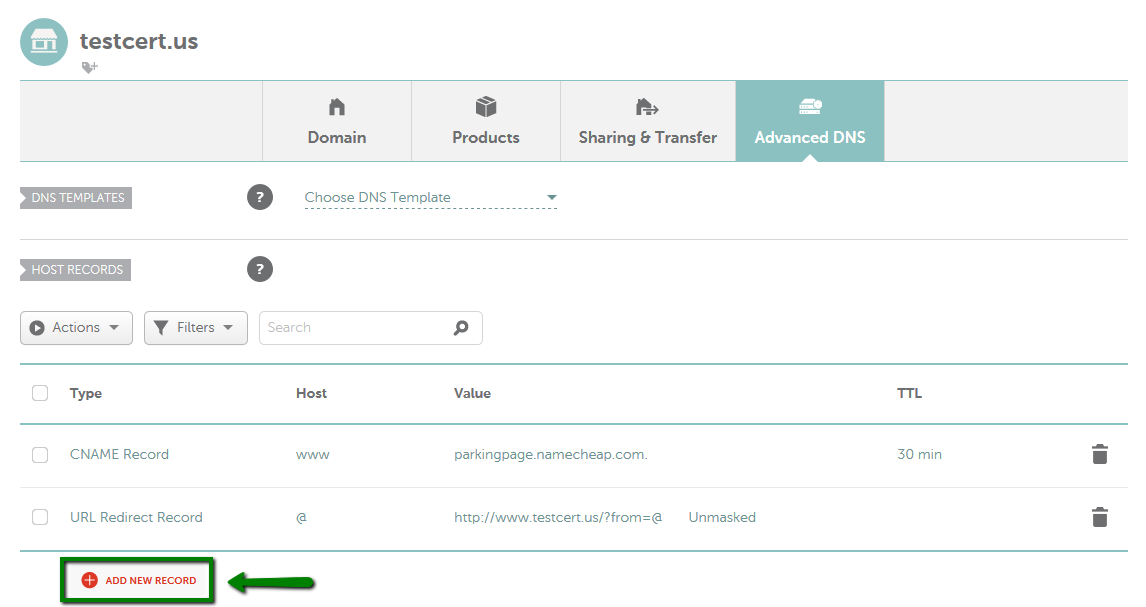
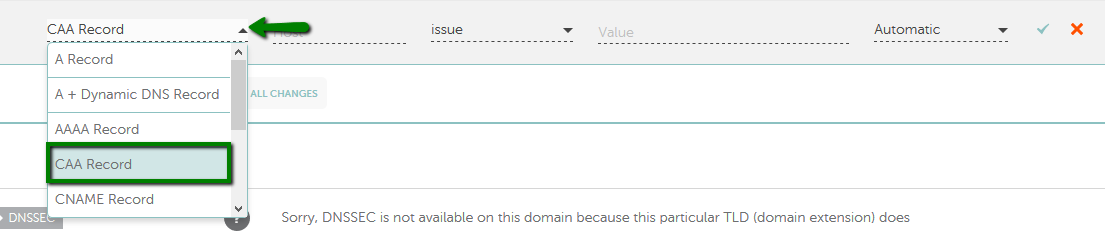
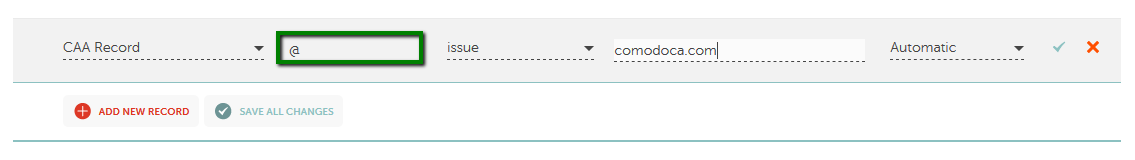
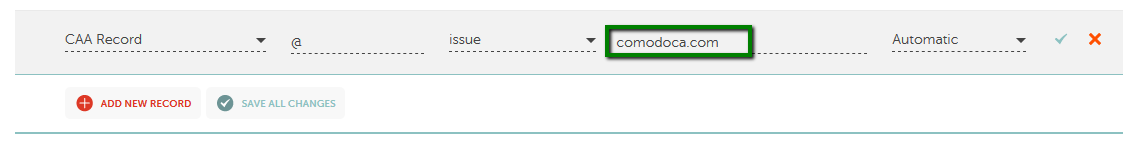
Note: "sectigo.com" and "trust-provider.com" values work as well for Sectigo certificates.
Need help? We're always here for you.