{"/api/v1/ncpl/simplekb/getarticle:\"{\\\"articleId\\\":9652,\\\"categoryId\\\":38}\"":{"body":{"Id":9652,"FriendlyId":"","ArticleTypeId":0,"Title":"Perfect Forward Secrecy. What it is?","ArticleName":"Perfect Forward Secrecy. What it is?","ArticleSummary":null,"PreponedSummary":false,"Approved":true,"Body":"DQoJCTxwPg0KCQkJCTxiPldoYXQgaXMgRlM/PC9iPg0KCQk8L3A+DQoJCTxwPg0KCQkJCTxiPkZvcndhcmQgU2VjcmVjeTwvYj4gKGFsc28ga25vd24gYXMgUGVyZmVjdCBGb3J3YXJkIFNlY3JlY3kpIGlzIGFuIGF0dHJpYnV0ZSBvZiB0aGUgc3BlY2lmaWMga2V5IGV4Y2hhbmdlIG1lY2hhbmlzbXMgaW4gU1NML1RMUyBzZWN1cml0eSBwcm90b2NvbHMgdGhhdCBpbXBsaWVzIHRoZSBpbmRlcGVuZGVuY2Ugb2YgdGhlIHNlc3Npb24ga2V5IGdlbmVyYXRlZCBkdXJpbmcgdGhlIHNlY3VyZSBzZXNzaW9uIGVzdGFibGlzaG1lbnQgZnJvbSB0aGUgc2V0IG9mIGxvbmctdGVybSBQdWJsaWMgYW5kIFByaXZhdGUga2V5cyBhbmQgdGhlIHNlc3Npb24ga2V5cyB1c2VkIGluIHByZXZpb3VzIHNlc3Npb25zLjwvcD4NCgkJPHA+VGhlIG1pc3Npb24gb2YgdGhlIGtleSBleGNoYW5nZSBpcyB0byBlbnN1cmUgdGhhdCB0d28gcGFydGllcyB3aWxsIGFncmVlIG9uIGEgc2Vzc2lvbiBrZXkgdXBvbiB0aGUgc2VjdXJpdHkgc2V0dGluZ3MgYXZhaWxhYmxlIGZvciBib3RoIHBhcnRpY2lwYW50cyBvZiB0aGUgc2VjdXJlIG5lZ290aWF0aW9uIGFuZCB0aGF0IG5vIG9uZSBlbHNlIHdpbGwga25vdyBpdC48L3A+DQoJCTxwPkZvciBhIGJldHRlciB1bmRlcnN0YW5kaW5nLCBsZXTigJlzIHJldmlldyB0aGUgbm9uLUZTIGtleSBhZ3JlZW1lbnQgYmFzZWQgb24gdGhlIGV4YW1wbGUgb2YgdGhlIFJTQSBrZXkgZXhjaGFuZ2UgbWVjaGFuaXNtIGZpcnN0bHkuIFJTQSBrZXkgZXhjaGFuZ2UgaXMgc3VwcG9ydGVkIGJ5IG5lYXJseSBhbnkgYXBwbGljYXRpb24gdXNpbmcgU1NML1RMUyBwcm90b2NvbC48L3A+DQoJCTxwPg0KCQkJCTxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9wZnNfMS5naWYiIGFsdD0icGZzXzEiIHdpZHRoPSI1MDAiIGhlaWdodD0iNDUwIiBib3JkZXI9IjAiIC8+DQoJCTwvcD4NCgkJPHA+SGVyZSBpcyBob3cgaXQgd29ya3M6IHRoZSBzZXJ2ZXIgc2VuZHMgaXRzIGNlcnRpZmljYXRlLCB0aGUgY2xpZW50IHBpY2tzIGEgcmFuZG9tIHNlc3Npb24ga2V5LCBlbmNyeXB0cyBpdCB3aXRoIHRoZSBzZXJ2ZXLigJlzIFB1YmxpYyBrZXkgb2J0YWluZWQgZnJvbSB0aGUgY2VydGlmaWNhdGUgYW5kIHNlbmRzIGl0IGJhY2sgdG8gdGhlIHNlcnZlci4gVGhlIHNlc3Npb24ga2V5IGNhbiBvbmx5IGJlIGRlY3J5cHRlZCB3aXRoIHRoZSBzZXJ2ZXLigJlzIFByaXZhdGUga2V5IHRoYXQgY29ycmVzcG9uZHMgdG8gdGhlIFB1YmxpYyBrZXksIHRodXMgY3JlYXRpbmcgdGhlIHNlY3VyZSBzZXNzaW9uLjwvcD4NCgkJPHA+SW4gc3VjaCBhIHdheSB0aGUgc2VydmVyIGVzdGFibGlzaGVzIGh1bmRyZWRzIG9mIHRob3VzYW5kcyBzZXNzaW9ucyB1c2luZyB0aGUgc2FtZSBrZXkgcGFpciwgY3JlYXRpbmcgYSBsaW5rIGJldHdlZW4gdGhlIGxvbmctdGVybSBrZXlzIGFuZCB0aGUgc2Vzc2lvbiBrZXkgZm9yIGVhY2ggdW5pcXVlIHNlc3Npb24uPC9wPg0KCQk8cD5BcyB3ZSBzZWUsIHRoZSBzZWNyZWN5IG9mIHRoZSBzZXNzaW9uIGtleSBzb2xlbHkgcmVsaWVzIG9uIHRoZSBzZXJ2ZXLigJlzIFByaXZhdGUga2V5IHNlY3JlY3kgd2hpY2ggbGVhZHMgdG8gdGhlIG9idmlvdXMgY29uY2x1c2lvbjogd2hhdCBpZiBzb21lb25lIGdldHMgaG9sZCBvZiB0aGUgUHJpdmF0ZSBrZXk/PC9wPg0KCQk8cD5JZiB0aGUgUHJpdmF0ZSBrZXkgaXMgbGVha2VkIG9yIGNvbXByb21pc2VkLCBhbiBhZHZlcnNhcnkgaXMgYWJsZSB0byBnbyBiYWNrIGluIHRpbWUgYW5kIGRlY3J5cHQgYWxsIHRoZSBwcmV2aW91c2x5IHNuaWZmZWQgKHJlY29yZGVkKSB0cmFmZmljIGVuY3J5cHRlZCB1c2luZyB0aGUgc2FtZSBsb25nLXRlcm0ga2V5IHBhaXIgYW5kIHN0ZWFsIHRoZSBzZW5zaXRpdmUgaW5mb3JtYXRpb24gdHJhbnNtaXR0ZWQgdGhyb3VnaCB0aGUgbmV0d29yayBjaGFubmVscy4gPC9wPg0KCQk8cD5BIHNpbXBsZSBhbmFsb2d5LCBhcyBpZiBzb21lb25lIGJyZWFrcyBpbnRvIHlvdXIgaG91c2UsIGhl4oCZbGwgYmUgYWJsZSB0byBzZWUgbm90IG9ubHkgd2hhdCdzIGluIHRoZXJlIHJpZ2h0IG5vdywgYnV0IGFsc28ga25vdyBldmVyeXRoaW5nIGZyb20gdGhlIHBhc3Q6IGFsbCB0aGUgcGVvcGxlIHdobyB1c2VkIHRvIGxpdmUgdGhlcmUsIGFsbCB0aGUgY29udmVyc2F0aW9ucyB0aGF0IHVzZWQgdG8gdGFrZSBwbGFjZSBpbiB0aGUgaG91c2Ugb3IgZXZlbiB0aGUgbmFtZSBvZiB5b3VyIGNhdC48L3A+DQoJCTxwPkJ5IGltcGxlbWVudGluZyB0aGUgZXhjaGFuZ2UgbWVjaGFuaXNtcyB0aGF0IHByb3ZpZGUgRm9yd2FyZCBTZWNyZWN5LCBldmVuIHRob3VnaCBzb21lb25lIGJyZWFrcyBpbnRvIGEgaG91c2UsIGhlIHN0aWxsIHdvbid0IGtub3cgd2hhdCB3YXMgaGFwcGVuaW5nIGJlZm9yZSBoZSBnb3QgdGhlcmUuPC9wPg0KCQk8cD4NCgkJCQk8Yj5CZW5lZml0cy9EcmF3YmFja3M8L2I+DQoJCTwvcD4NCgkJPHA+VGhlIG1lY2hhbmlzbXMgdGhhdCBwcm92aWRlIEZTIHVzZSB0aGUgRGlmZmllLUhlbGxtYW4gKERIKSBrZXkgZXhjaGFuZ2UgYXMga2V5IG1hdGVyaWFsLCBwcmVjaXNlbHkgaXRzIEVwaGVtZXJhbCBtb2RlLiA8YSBocmVmPSJodHRwczovL3d3dy5vd2FzcC5vcmcvaW5kZXgucGhwL01haW5fUGFnZSIgdGFyZ2V0PSJfYmxhbmsiPk9XQVNQPC9hPiAoT3BlbiBXZWIgQXBwbGljYXRpb24gU2VjdXJpdHkgUHJvamVjdCkgZ2l2ZXMgdGhlIGZvbGxvd2luZyBkZWZpbml0aW9uIG9mIGVwaGVtZXJhbCBrZXlzOjwvcD4NCgkJPHA+DQoJCQkJPGk+RXBoZW1lcmFsIGtleXMgYXJlIHRlbXBvcmFyeSBrZXlzIHVzZWQgZm9yIG9uZSBpbnN0YW5jZSBvZiBhIHByb3RvY29sIGV4ZWN1dGlvbiBhbmQgdGhlbiB0aHJvd24gYXdheS4gQW4gZXBoZW1lcmFsIGtleSBoYXMgdGhlIGJlbmVmaXQgb2YgcHJvdmlkaW5nIGZvcndhcmQgc2VjcmVjeSwgbWVhbmluZyBhIGNvbXByb21pc2Ugb2YgdGhlIHNpdGUgb3Igc2VydmljZSdzIGxvbmcgdGVybSAoc3RhdGljKSBzaWduaW5nIGtleSBkb2VzIG5vdCBmYWNpbGl0YXRlIGRlY3J5cHRpbmcgcGFzdCBtZXNzYWdlcyBiZWNhdXNlIHRoZSBrZXkgd2FzIHRlbXBvcmFyeSBhbmQgZGlzY2FyZGVkIChvbmNlIHRoZSBzZXNzaW9uIHRlcm1pbmF0ZWQpLjwvaT4NCgkJPC9wPg0KCQk8cD5JbiBvdGhlciB3b3JkcywgdGhlIHNlc3Npb24ga2V5IGdlbmVyYXRlZCB1cG9uIHRoZSBuZWdvdGlhdGVkIERIIHBhcmFtZXRlcnMgaXMgdW5pcXVlIGZvciBlYWNoIGluZGl2aWR1YWwgc2Vzc2lvbiwgZG9lcyBub3QgcmVseSBvbiB0aGUgc2VydmVy4oCZcyBsb25nLXRlcm0ga2V5cyAodGhleSBhcmUgb25seSB1c2VkIGZvciB0aGUgc2VydmVy4oCZcyBhdXRoZW50aWNhdGlvbiBwdXJwb3NlcykgYW5kIHdpbGwgYmUgZXJhc2VkIGFmdGVyIHRoZSBzZXNzaW9uIGlzIGVuZGVkLiBPYnZpb3VzbHksIHRoaXMgaW5jcmVhc2VzIGRyYXN0aWNhbGx5IHRoZSBwcm90ZWN0aW9uIG9mIHRoZSBlbmNyeXB0ZWQgdHJhZmZpYy48L3A+DQoJCTxwPg0KCQkJCTxiPk9ubHkgdGhlIERpZmZpZS1IZWxsbWFuIEVwaGVtZXJhbCAoREhFKSBhbmQgaXRzIGxpZ2h0ZXIgdmVyc2lvbiBiYXNlZCBvbiBFbGxpcHRpYyBDdXJ2ZXMgKEVDREhFKSBrZXkgZXhjaGFuZ2UgbWVjaGFuaXNtcyBwcm92aWRlIHRoZSBGb3J3YXJkIFNlY3JlY3kuPC9iPg0KCQk8L3A+DQoJCTxwPkFmdGVyIGFsbCwgYm90aCBESEUgYW5kIEVDREhFIGRlZ3JhZGUgdGhlIHdlYnNpdGXigJlzIHBlcmZvcm1hbmNlIChpLmUuIHBhZ2XigJlzIGxvYWRpbmcgc3BlZWQpIHdoZW4gdXNlZCB3aXRoIFJTQSBsb25nLXRlcm0ga2V5cywgYXMgYm90aCBpbXBseSB0aGUgaGVhdnkgYXJpdGhtZXRpY3MgdGhhdCBzaWduaWZpY2FudGx5IGluY3JlYXNlIHRoZSBDUFUgbG9hZC4gV2hlbiB1c2VkIHdpdGggRUNEU0EgKEVsbGlwdGljLUN1cnZlIERpZ2l0YWwgU2lnbmF0dXJlIEFsZ29yaXRobSkgbG9uZy10ZXJtIGtleXMgaG93ZXZlciwgdGhlIDxhIGhyZWY9Imh0dHBzOi8vc2VjdXJpdHlwaXRmYWxscy53b3JkcHJlc3MuY29tLzIwMTQvMTAvMDYvcnNhLWFuZC1lY2RzYS1wZXJmb3JtYW5jZS8iIHRhcmdldD0iX2JsYW5rIj5kaWZmZXJlbmNlIGluIHBlcmZvcm1hbmNlIGlzIG5vdCBzbyBjcnVjaWFsPC9hPi4gRm9yIG5vdywgRUMga2V5cyBhcmUgbm90IHlldCBzbyB3aWRlbHkgc3VwcG9ydGVkLiBEZXNwaXRlIHRoYXQsIHlvdSBjYW4gYWxyZWFkeSBnZXQgdGhlIGNlcnRpZmljYXRlIHNpZ25lZCB3aXRoIEVDIGtleSBmcm9tIHVzLiBGZWVsIGZyZWUgdG8gY2hlY2sgbW9yZSBkZXRhaWxzIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC85NTA0LzM4L2hvdy1kby1pLWdldC1hbi1lY2MtY2VydGlmaWNhdGUtdmlhLW5hbWVjaGVhcCIgdGFyZ2V0PSJfYmxhbmsiPmhlcmU8L2E+LjwvcD4NCgkJPHA+VXNpbmcgdGhlIGNpcGhlciBzdWl0ZXMgdGhhdCBwcm92aWRlIGtleSBleGNoYW5nZXMgd2l0aCBGUyBvbmx5IGNhbiBjYXVzZSBzb21lIGluY29tcGF0aWJpbGl0aWVzIHdpdGggPGEgaHJlZj0iaHR0cHM6Ly9zdXBwb3J0Lmdsb2JhbHNpZ24uY29tL2N1c3RvbWVyL3BvcnRhbC9hcnRpY2xlcy8xOTk1MjgzLWVjYy1jb21wYXRpYmlsaXR5IiB0YXJnZXQ9Il9ibGFuayI+bGVnYWN5IHN5c3RlbXM8L2E+LCBidXQgaXNu4oCZdCBpdCBhIHJlYXNvbmFibGUgY29zdCBmb3Igc3VjaCBhIHNlY3VyaXR5IGVuaGFuY2VtZW50PyA8L3A+DQoJCTxwPkl0IGlzIHdvcnRoIG1lbnRpb25pbmcgdGhhdCB5b3Ugc2hvdWxkIHBheSBzcGVjaWFsIGF0dGVudGlvbiB3aGVuIGVuYWJsaW5nIHRoZSBzdXBwb3J0IG9mIHRoZSBjaXBoZXIgc3VpdGVzIHRoYXQgaW1wbHkgREhFIGtleSBleGNoYW5nZSBhcyB0aGV5IGFyZSB0aGUgbWFpbiB2ZWN0b3Igb2YgdGhlIG5ldyB2dWxuZXJhYmlsaXR5IGluIFRMUyBwcm90b2NvbCBkaXNjb3ZlcmVkIGJ5IHRoZSBncm91cCBvZiByZXNlYXJjaGVycyB3aG8gYnJvdWdodCB0byB1cyB0aGUgPGEgaHJlZj0iaHR0cHM6Ly9mcmVha2F0dGFjay5jb20vIiB0YXJnZXQ9Il9ibGFuayI+RlJFQUsgQXR0YWNrPC9hPi4gVGhlIG5ldyBhdHRhY2sgaXMgY2FsbGVkIDxhIGhyZWY9Imh0dHBzOi8vd2Vha2RoLm9yZy8iIHRhcmdldD0iX2JsYW5rIj5Mb2dqYW08L2E+LiBESEUgd2l0aCB3ZWFrIERIIGdyb3VwIGFuZCBESEVfRVhQT1JUIGNpcGhlciBzdWl0ZXMgYXJlIGFmZmVjdGVkLiA8L3A+DQoJCTxwPkluIG9yZGVyIHRvIG1pdGlnYXRlIHRoZSBhdHRhY2ssIHRoZSBzdXBwb3J0IG9mIHRoZSBESEUtRVhQT1JUIGNpcGhlciBzdWl0ZXMgc2hvdWxkIGJlIGRpc2FibGVkLiBBcyBmb3IgdGhlIERIRSBjaXBoZXJzLCBpdCBpcyByZWNvbW1lbmRlZCB0aGF0IHRoZSA8YSBocmVmPSJodHRwczovL3dlYWtkaC5vcmcvc3lzYWRtaW4uaHRtbCIgdGFyZ2V0PSJfYmxhbmsiPmN1c3RvbSBESCBncm91cDwvYT4gaXMgdXNlZCBpbnN0ZWFkLiBUaGUgc2l6ZSBvZiB0aGUgREgga2V5IGluIGEgY3VzdG9tIERIIGNpcGhlciBncm91cCBzaG91bGQgYmUgaW5jcmVhc2VkIHNvIHRoYXQgaXQgbWF0Y2hlcyB0aGUgcmVjb21tZW5kZWQgbGVuZ3RoIG9mIHRoZSBsb25nLXRlcm0ga2V5IChjdXJyZW50IHN0YW5kYXJkIGlzIDIwNDgtYml0KS48L3A+DQoJCTxwPlNvbWUgc2VydmVycyBkb27igJl0IGhhdmUgYW4gb3B0aW9uIHRvIHNldCB0aGUgY3VzdG9tIERIIGdyb3VwcyBvciBjaGFuZ2UgdGhlIHNpemUgb2YgdGhlIERIIGtleSwgdGhlcmVmb3JlLCB0aGUgc3VwcG9ydCBvZiBESEUgY2lwaGVyIHN1aXRlcyBzaG91bGQgYmUgZGlzYWJsZWQuIEFzIGFuIGFsdGVybmF0aXZlLCB0aGUgRUNESEUgc2hvdWxkIGJlIHVzZWQuIFRoZSBFQ0RIRSBrZXkgZXhjaGFuZ2UgaXMgc2xpZ2h0bHkgZmFzdGVyIGluIGNvbXBhcmlzb24gdG8gREhFIGFuZCBpcyB3aWRlbHkgc3VwcG9ydGVkIGJ5IHRoZSBtYWpvcml0eSBvZiB3ZWIgYnJvd3NlcnMuPC9wPg0KCQk8cD5Bbm90aGVyIGRyYXdiYWNrIGlzIHRoYXQgZHVlIHRvIHRoZSBzZXJ2ZXIgYWRtaW5pc3RyYXRvcnPigJkgdW5hd2FyZW5lc3MsIHRoZSBGb3J3YXJkIFNlY3JlY3kgY2FuIGVhc2lseSBiZSBicm9rZW4uIEl0IGlzIG5vdCBlbm91Z2ggdG8gZW5hYmxlIHRoZSBzdXBwb3J0IG9mIHRoZSBjaXBoZXIgc3VpdGVzIHdpdGggY2VydGFpbiBGUyBrZXkgZXhjaGFuZ2UgbWVjaGFuaXNtcyBvbiB0aGUgc2VydmVyLCBidXQgdG8gcHJpb3JpdGl6ZSB0aGVtIHRvIGJlIHVzZWQgYnkgdGhlIHNlcnZlciBpbiB0aGUgZmlyc3QgcGxhY2UgYXQgYWxsIHRpbWVzLjwvcD4NCgkJPHA+QW5vdGhlciB3YXkgdG8gbWVzcyB1cCB0aGUgRm9yd2FyZCBTZWNyZWN5IGlzIHRvIGNvbmZpZ3VyZSB0aGUgc2VydmVyIHRvIHVzZSB0aGUgbG9uZyBkdXJhdGlvbiBzZXNzaW9uIElEcyBvciBzZXNzaW9uIHRpY2tldHMsIHdoaWNoIGFyZSB1c2VkIGZvciB0aGUgc2Vzc2lvbiByZXN1bXB0aW9uLjwvcD4NCgkJPHA+SXZhbiBSaXN0aWMsIHRoZSBEaXJlY3RvciBvZiBFbmdpbmVlcmluZyBhdCB0aGUgY2xvdWQgc2VjdXJpdHkgZmlybSA8YSBocmVmPSJodHRwczovL3d3dy5xdWFseXMuY29tLyIgdGFyZ2V0PSJfYmxhbmsiPlF1YWx5czwvYT4sIGRlZmluZXMgdGhlIGZvbGxvd2luZyBhdHRhY2sgdmVjdG9ycyBpbiBoaXMgPGEgaHJlZj0iaHR0cHM6Ly9jb21tdW5pdHkucXVhbHlzLmNvbS9ibG9ncy9zZWN1cml0eWxhYnMvMjAxMy8wNi8yNS9zc2wtbGFicy1kZXBsb3lpbmctZm9yd2FyZC1zZWNyZWN5IiB0YXJnZXQ9Il9ibGFuayI+YXJ0aWNsZTwvYT4gZGVkaWNhdGVkIHRvIEZvcndhcmQgU2VjcmVjeTo8L3A+DQoJCTxwPg0KCQkJCTxpPuKAnFNlcnZlci1zaWRlIHNlc3Npb24gbWFuYWdlbWVudCBtZWNoYW5pc21zIGNvdWxkIGFsc28gaW1wYWN0IGZvcndhcmQgc2VjcmVjeS4gRm9yIHBlcmZvcm1hbmNlIHJlYXNvbnMsIHNlc3Npb24ga2V5cyBtaWdodCBiZSBrZXB0IGZvciBtYW55IGhvdXJzIChvciBsb25nZXIpIGFmdGVyIHRoZSBjb252ZXJzYXRpb24gaGFkIGJlZW4gdGVybWluYXRlZC48L2k+DQoJCTwvcD4NCgkJPHA+DQoJCQkJPGk+SW4gYWRkaXRpb24sIHRoZXJlIGlzIGFuIGFsdGVybmF0aXZlIHNlc3Npb24gbWFuYWdlbWVudCBtZWNoYW5pc20gY2FsbGVkIHNlc3Npb24gdGlja2V0cywgd2hpY2ggdXNlcyBzZXBhcmF0ZSBlbmNyeXB0aW9uIGtleXMgdGhhdCBhcmUgaW5mcmVxdWVudGx5IHJvdGF0ZWQgKHBvc3NpYmx5IG5ldmVyIGluIGV4dHJlbWUgY2FzZXMpLiBVbmxlc3MgeW91IHVuZGVyc3RhbmQgeW91ciBzZXNzaW9uIHRpY2tldHMgaW1wbGVtZW50YXRpb24gdmVyeSB3ZWxsLCB0aGlzIGZlYXR1cmUgaXMgYmVzdCBkaXNhYmxlZCB0byBlbnN1cmUgaXQgZG9lcyBub3QgY29tcHJvbWlzZSBmb3J3YXJkIHNlY3JlY3ku4oCdPC9pPg0KCQk8L3A+IA0KDQpUaGUgbWV0aG9kcyBob3cgdG8gY2hlY2sgaWYgdGhlIHNlcnZlciB1c2VzIHRoZSBrZXkgZXhjaGFuZ2Ugd2hpY2ggcHJvdmlkZXMgRm9yd2FyZCBTZWNyZWN5IGFyZSBkZXNjcmliZWQgaW4gPGEgaHJlZj0iaHR0cHM6Ly93d3cubmFtZWNoZWFwLmNvbS9zdXBwb3J0L2tub3dsZWRnZWJhc2UvYXJ0aWNsZS5hc3B4Lzk2NTMvMzgvaG93LXRvLWNoZWNrLXdoZXRoZXItdGhlLXNlcnZlci1zdXBwb3J0cy1mb3J3YXJkLXNlY3JlY3kvIiB0YXJnZXQ9Il9ibGFuayI+dGhpcyBhcnRpY2xlPC9hPi4=","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"2022-09-07T09:43:21.0000000","LiveDateTime":"1754-02-02T00:00:00.0000000","CreatedDateTime":"2015-11-22T12:52:24.0000000","ApprovalDatetime":"2015-11-22T13:00:20.0000000","RequestCount":44228,"MarkedAsNew":false,"MarkedAsFeatured":false,"RatingValue":2,"CategoryPaths":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":1,"CategoryId":14,"CategoryName":"SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":2,"CategoryId":38,"CategoryName":"SSL General"}],"AssociatedCategories":[{"CategoryId":38,"CategoryName":"SSL General","CategoryDisplayName":"SSL CertificatesSSL General"}],"AssociatedTags":[],"RelatedArticles":[],"AssociatedMedias":[],"PreferredCategoryId":0,"RootParentCategoryName":"","RootParentCategoryId":0},"status":200,"statusText":"OK"},"/api/v1/ncpl/simplekb/getcategorybycategoryid:\"{\\\"categoryId\\\":38}\"":{"body":{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryDto","Description":"QmFzaWMgaW5mb3JtYXRpb24gb24gU1NMIGNlcnRpZmljYXRlcw==","ParentCategoryId":14,"Parent_Category_Name":"SSL Certificates","FriendlyId":null,"ApprovedYN":true,"TreatAsTopicYN":false,"CreatedDateTime":"07/25/2008 16:58:37","CurrentCategoryPaths":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":1,"CategoryId":14,"CategoryName":"SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":2,"CategoryId":38,"CategoryName":"SSL General"}],"RelatedCategories":[],"AssociatedArticles":[{"ArticleId":9503,"Title":"What is an ECC (Elliptic Curve Cryptography) certificate?","ArticleName":"What is an ECC (Elliptic Curve Cryptography) certificate?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/23/2019"},{"ArticleId":9504,"Title":"How do I get an ECC certificate via Namecheap?","ArticleName":"How do I get an ECC certificate via Namecheap?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/06/2025"},{"ArticleId":9507,"Title":"Why an EV certificate is better for an ecommerce website than a Domain Validation one?","ArticleName":"Why an EV certificate is better for an ecommerce website than a Domain Validation one?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"07/24/2020"},{"ArticleId":9508,"Title":"What is the difference between very high, high, medium and low assurance certificates?","ArticleName":"What is the difference between very high, high, medium and low assurance certificates?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/15/2024"},{"ArticleId":9509,"Title":"Your site shows 256-bit encryption and my site shows 128-bit, why?","ArticleName":"Your site shows 256-bit encryption and my site shows 128-bit, why?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"08/27/2019"},{"ArticleId":9511,"Title":"How 2–5-year SSL certificates work","ArticleName":"How 2–5-year SSL certificates work","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":"03/14/2015 04:00:00","FeaturedTillDate":"03/09/2015 04:00:00","ModifiedDateTime":"04/15/2024"},{"ArticleId":9588,"Title":"What is Certificate Transparency?","ArticleName":"What is Certificate Transparency?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/06/2025"},{"ArticleId":9595,"Title":"HTTP to HTTPS redirection on IIS","ArticleName":"HTTP to HTTPS redirection on IIS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/25/2019"},{"ArticleId":9596,"Title":"HTTP Strict Transport Security (HSTS)","ArticleName":"HTTP Strict Transport Security (HSTS)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9597,"Title":"HTTP Public Key Pinning (HPKP)","ArticleName":"HTTP Public Key Pinning (HPKP)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/06/2024"},{"ArticleId":9598,"Title":"Disabling SSLv3","ArticleName":"Disabling SSLv3","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9599,"Title":"Disabling RC4","ArticleName":"Disabling RC4","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9600,"Title":"Disabling SHA-1","ArticleName":"Disabling SHA-1","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9601,"Title":"Cipher Suites Configuration and forcing Perfect Forward Secrecy on Windows","ArticleName":"Cipher Suites Configuration and forcing Perfect Forward Secrecy on Windows","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":9602,"Title":"OCSP Stapling","ArticleName":"OCSP Stapling","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9650,"Title":"I can see SHA-1 fingerprint/thumbprint on my certificate. Is my certificate actually SHA-2?","ArticleName":"I can see SHA-1 fingerprint/thumbprint on my certificate. Is my certificate actually SHA-2?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/23/2019"},{"ArticleId":9652,"Title":"Perfect Forward Secrecy. What it is?","ArticleName":"Perfect Forward Secrecy. What it is?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2022"},{"ArticleId":9653,"Title":"How to check whether the server supports Forward Secrecy","ArticleName":"How to check whether the server supports Forward Secrecy","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"06/22/2023"},{"ArticleId":9682,"Title":"How to push SSL certificates from one Namecheap account to another one","ArticleName":"How to push SSL certificates from one Namecheap account to another one","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/06/2025"},{"ArticleId":9707,"Title":"HSTS: General information","ArticleName":"HSTS: General information","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9708,"Title":"Prerequisites for Namecheap Shared hosting to enable HSTS","ArticleName":"Prerequisites for Namecheap Shared hosting to enable HSTS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9709,"Title":"How to enable HSTS on Namecheap shared hosts","ArticleName":"How to enable HSTS on Namecheap shared hosts","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/10/2023"},{"ArticleId":9710,"Title":"How to enable HSTS on third-party servers","ArticleName":"How to enable HSTS on third-party servers","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9711,"Title":"How to check if HSTS is enabled","ArticleName":"How to check if HSTS is enabled","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9727,"Title":"What is SSL certificate encryption strength?","ArticleName":"What is SSL certificate encryption strength?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9752,"Title":"How do I get A+ rating in SSLLabs?","ArticleName":"How do I get A+ rating in SSLLabs?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9770,"Title":"How to use .htaccess to redirect to https in cPanel","ArticleName":"How to use .htaccess to redirect to https in cPanel","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/10/2023"},{"ArticleId":9782,"Title":"Security tips for business","ArticleName":"Security tips for business","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/12/2021"},{"ArticleId":9783,"Title":"1024 bit certificates","ArticleName":"1024 bit certificates","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/13/2022"},{"ArticleId":9800,"Title":"Advantages of having an SSL certificate","ArticleName":"Advantages of having an SSL certificate","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2023"},{"ArticleId":9805,"Title":"Setting HTTPS redirect on a Nginx web-server","ArticleName":"Setting HTTPS redirect on a Nginx web-server","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9821,"Title":"Apache Redirect to HTTPS","ArticleName":"Apache Redirect to HTTPS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"06/19/2020"},{"ArticleId":9952,"Title":"Supported key sizes and signature algorithms in CSRs","ArticleName":"Supported key sizes and signature algorithms in CSRs","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"12/05/2017 05:00:00","ModifiedDateTime":"07/27/2023"},{"ArticleId":9953,"Title":"IIS Redirect HTTP to HTTPS","ArticleName":"IIS Redirect HTTP to HTTPS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"11/28/2017 05:00:00","ModifiedDateTime":"12/06/2022"},{"ArticleId":9968,"Title":"How to check the certificate revocation status","ArticleName":"How to check the certificate revocation status","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"01/26/2018 05:00:00","ModifiedDateTime":"09/24/2019"},{"ArticleId":9969,"Title":"HPKP pinning","ArticleName":"HPKP pinning","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/06/2024"},{"ArticleId":9991,"Title":"CAA Record and why it is needed (SSL related)","ArticleName":"CAA Record and why it is needed (SSL related)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"04/30/2018 04:00:00","ModifiedDateTime":"09/07/2022"},{"ArticleId":10081,"Title":"Comodo CA rebrands as Sectigo","ArticleName":"Comodo CA rebrands as Sectigo","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"01/25/2019"},{"ArticleId":10100,"Title":"Cipher Suites Configuration for Apache, Nginx","ArticleName":"Cipher Suites Configuration for Apache, Nginx","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2022"},{"ArticleId":10503,"Title":"How to remove an SSL from a Namecheap account","ArticleName":"How to remove an SSL from a Namecheap account","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/11/2025"},{"ArticleId":10504,"Title":"What is AutoSSL and how to use it?","ArticleName":"What is AutoSSL and how to use it?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/18/2025"},{"ArticleId":10557,"Title":"Decoder.link user guide","ArticleName":"Decoder.link user guide","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/15/2025"},{"ArticleId":10595,"Title":"Understanding How SSL Encryption Works","ArticleName":"Understanding How SSL Encryption Works","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"04/05/2023"},{"ArticleId":10597,"Title":"What is SSL and TLS","ArticleName":"What is SSL and TLS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2023"},{"ArticleId":10747,"Title":"What is MPIC (Multi-Perspective Issuance Corroboration)","ArticleName":"What is MPIC (Multi-Perspective Issuance Corroboration)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/15/2025"},{"ArticleId":9293,"Title":"I need to secure some of the subdomains of my domain name","ArticleName":"I need to secure some of the subdomains of my domain name","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9294,"Title":"I need to secure two, three or more domain names with the same certificate","ArticleName":"I need to secure two, three or more domain names with the same certificate","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":9464,"Title":"Can I download an issued certificate on your site?","ArticleName":"Can I download an issued certificate on your site?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/12/2024"},{"ArticleId":786,"Title":"What is an SSL certificate and what is it used for?","ArticleName":"What is an SSL certificate and what is it used for?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"07/24/2023"},{"ArticleId":334,"Title":"What is Certificate Authority (CA)?","ArticleName":"What is Certificate Authority (CA)?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9415,"Title":"SSL certificate migration from the SHA-1 to SHA-2 algorithm","ArticleName":"SSL certificate migration from the SHA-1 to SHA-2 algorithm","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9467,"Title":"How do I check my hashing algorithm?","ArticleName":"How do I check my hashing algorithm?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9484,"Title":"I want to test your service do you have trial certificates?","ArticleName":"I want to test your service do you have trial certificates?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"04/28/2025"},{"ArticleId":789,"Title":"Can I use a single SSL certificate for multiple subdomains?","ArticleName":"Can I use a single SSL certificate for multiple subdomains?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":787,"Title":"How to inform your clients that you use SSL","ArticleName":"How to inform your clients that you use SSL","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2023"},{"ArticleId":464,"Title":"What is a wildcard certificate?","ArticleName":"What is a wildcard certificate?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/07/2024"},{"ArticleId":790,"Title":"Types of certificates offered at Namecheap","ArticleName":"Types of certificates offered at Namecheap","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/01/2019"},{"ArticleId":9469,"Title":"Are your certificates private or shared? What is the difference?","ArticleName":"Are your certificates private or shared? What is the difference?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/26/2015"},{"ArticleId":9466,"Title":"Can I get a certificate if I use an online web-hosting (Wix, Weebly, Tumblr, etc.)?","ArticleName":"Can I get a certificate if I use an online web-hosting (Wix, Weebly, Tumblr, etc.)?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"01/20/2021"},{"ArticleId":9473,"Title":"Can I use your SSL certificates for FTP and SQL?","ArticleName":"Can I use your SSL certificates for FTP and SQL?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/22/2018"},{"ArticleId":9481,"Title":"I have a certificate at another vendor; will there be an issue, if I activate one with you for the same common name?","ArticleName":"I have a certificate at another vendor; will there be an issue, if I activate one with you for the same common name?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/26/2015"},{"ArticleId":982,"Title":"Domain Validated certificates","ArticleName":"Domain Validated certificates","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":886,"Title":"Chained and single Root certificates","ArticleName":"Chained and single Root certificates","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":885,"Title":"SSL certificate warranty","ArticleName":"SSL certificate warranty","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"}],"AssociatedTags":[],"CategoryId":38,"CategoryName":"SSL General"},"status":200,"statusText":"OK"},"/api/v1/ncpl/simplekb/getcategories:\"{\\\"parentCategoryId\\\":0,\\\"getTree\\\":true}\"":{"body":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2216,"CategoryName":"Spam Protection"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2217,"CategoryName":"Renewal"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2218,"CategoryName":"cPanel SSL Plugin"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2219,"CategoryName":"PHP Configuration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2221,"CategoryName":"Multi-Domain SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2222,"CategoryName":"Cancellation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2223,"CategoryName":"Browser errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2224,"CategoryName":"Site Seal, Logo"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2225,"CategoryName":"SEO"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2226,"CategoryName":"Email Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2227,"CategoryName":"SSL Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/cloud-red.png","ShortDesc":"","CategoryId":2228,"CategoryName":"Apps","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2251,"CategoryName":"Supersonic CDN"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2298,"CategoryName":"Site Maker"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":177,"CategoryName":"Google Workspace (formerly G Suite)"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2229,"CategoryName":"Hosting Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2232,"CategoryName":"DNSSEC"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2234,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2237,"CategoryName":"Host records setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2238,"CategoryName":"SSL installation errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/easywp-red.png","ShortDesc":"","CategoryId":2239,"CategoryName":"EasyWP","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2280,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2279,"CategoryName":"General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2281,"CategoryName":"WordPress Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2282,"CategoryName":"Plugins and Themes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2284,"CategoryName":"WordPress Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2285,"CategoryName":"SFTP and Database access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2286,"CategoryName":"Domains questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2288,"CategoryName":"Billing questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2287,"CategoryName":"SSL questions"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2251,"CategoryName":"Supersonic CDN"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2252,"CategoryName":"InterWorx questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2254,"CategoryName":"Domains How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2255,"CategoryName":"Hosting How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2257,"CategoryName":"Sales & Payments How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2258,"CategoryName":"cPanel Email How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2260,"CategoryName":"Private Email Contacts and Calendars Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2262,"CategoryName":"EasyWP How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"https://download.namecheap.com/assets/img/domainvault-red@2x.png","ShortDesc":"","CategoryId":2289,"CategoryName":"Domain Vault","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2290,"CategoryName":"CSR code"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2291,"CategoryName":"Webuzo questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2292,"CategoryName":"Browser Extensions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2293,"CategoryName":"Automated SSL management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2298,"CategoryName":"Site Maker"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":27,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/support-red.png","ShortDesc":"","CategoryId":5,"CategoryName":"General & Support","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":7,"CategoryName":"Billing FAQ"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":8,"CategoryName":"Transfer Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":22,"CategoryName":"Hosting Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":38,"CategoryName":"SSL General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":45,"CategoryName":"Account Security"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":46,"CategoryName":"Domain Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":63,"CategoryName":"Namecheap API"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":177,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2179,"CategoryName":"Private Email: General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2274,"CategoryName":"General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2280,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2279,"CategoryName":"General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2215,"CategoryName":"Private Email: Mailbox Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2196,"CategoryName":"WHMCS module for SSL"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/savings-red.png","ShortDesc":"","CategoryId":2200,"CategoryName":"Checkout & Billing","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":7,"CategoryName":"Billing FAQ"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2201,"CategoryName":"Domains Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":21,"CategoryName":"Hosting Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":71,"CategoryName":"SSL Certificates Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2177,"CategoryName":"Private Email"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2201,"CategoryName":"Domains Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":67,"CategoryName":"Activation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":83,"CategoryName":"Transfer to Namecheap"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":43,"CategoryName":"Profile Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":10,"CategoryName":"DNS Questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":29,"CategoryName":"cPanel questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":21,"CategoryName":"Hosting Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":11,"CategoryName":"Dynamic DNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":44,"CategoryName":"Account Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":84,"CategoryName":"Transfer to another provider"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":68,"CategoryName":"Validation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2182,"CategoryName":"cPanel: Software Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2214,"CategoryName":"Email Forwarding"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2270,"CategoryName":"Routers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2281,"CategoryName":"WordPress Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2282,"CategoryName":"Plugins and Themes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2272,"CategoryName":"TV"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2187,"CategoryName":"cPanel: WordPress"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":219,"CategoryName":"Canceled Transfers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":71,"CategoryName":"SSL Certificates Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2176,"CategoryName":"Private Email: DNS Settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":69,"CategoryName":"Installation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/reseller-red.png","ShortDesc":"","CategoryId":34,"CategoryName":"Domains","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2232,"CategoryName":"DNSSEC"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2234,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2237,"CategoryName":"Host records setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":46,"CategoryName":"Domain Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":10,"CategoryName":"DNS Questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":11,"CategoryName":"Dynamic DNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":35,"CategoryName":"Registrations"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2207,"CategoryName":"Renewal questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":36,"CategoryName":"Domains with extended attributes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":51,"CategoryName":"FreeDNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":15,"CategoryName":"Namecheap Market"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2208,"CategoryName":"3rd Party Services Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2278,"CategoryName":"Handshake TLDs"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":35,"CategoryName":"Registrations"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":70,"CategoryName":"Reissuance"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/protection-red.png","ShortDesc":"","CategoryId":37,"CategoryName":"Domain Privacy Protection","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2177,"CategoryName":"Private Email"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2178,"CategoryName":"Private Email: Webmail Features"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2207,"CategoryName":"Renewal questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2210,"CategoryName":"cPanel Add-ons"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2273,"CategoryName":"Gaming Consoles"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2284,"CategoryName":"WordPress Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2285,"CategoryName":"SFTP and Database access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2268,"CategoryName":"macOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2175,"CategoryName":"Private Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/status-red.png","ShortDesc":"","CategoryId":2209,"CategoryName":"Domain Transfers","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":8,"CategoryName":"Transfer Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":83,"CategoryName":"Transfer to Namecheap"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":84,"CategoryName":"Transfer to another provider"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":219,"CategoryName":"Canceled Transfers"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":48,"CategoryName":"VPS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":36,"CategoryName":"Domains with extended attributes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/server-red.png","ShortDesc":"","CategoryId":12,"CategoryName":"Hosting","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2219,"CategoryName":"PHP Configuration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2225,"CategoryName":"SEO"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2252,"CategoryName":"InterWorx questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2291,"CategoryName":"Webuzo questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":27,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":22,"CategoryName":"Hosting Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":29,"CategoryName":"cPanel questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2182,"CategoryName":"cPanel: Software Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2187,"CategoryName":"cPanel: WordPress"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2210,"CategoryName":"cPanel Add-ons"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":48,"CategoryName":"VPS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2188,"CategoryName":"Dedicated Server"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":30,"CategoryName":"WHM questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":32,"CategoryName":"DNS settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":103,"CategoryName":"LVE (CloudLinux)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":89,"CategoryName":"SSH Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":205,"CategoryName":"FTP questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2180,"CategoryName":"MySQL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2199,"CategoryName":"Hosting Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2194,"CategoryName":"Tips & Tricks"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":239,"CategoryName":"WHMCS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":33,"CategoryName":"SSL Installation"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2171,"CategoryName":"Private Email: Active Sync (Exchange) Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2188,"CategoryName":"Dedicated Server"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2269,"CategoryName":"iOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2286,"CategoryName":"Domains questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2288,"CategoryName":"Billing questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2271,"CategoryName":"Linux"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":30,"CategoryName":"WHM questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":31,"CategoryName":"cPanel Email FAQs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":51,"CategoryName":"FreeDNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/email-red.png","ShortDesc":"","CategoryId":93,"CategoryName":"Email service","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2216,"CategoryName":"Spam Protection"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2226,"CategoryName":"Email Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2260,"CategoryName":"Private Email Contacts and Calendars Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2179,"CategoryName":"Private Email: General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2215,"CategoryName":"Private Email: Mailbox Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2214,"CategoryName":"Email Forwarding"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2176,"CategoryName":"Private Email: DNS Settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2178,"CategoryName":"Private Email: Webmail Features"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2175,"CategoryName":"Private Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2171,"CategoryName":"Private Email: Active Sync (Exchange) Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":31,"CategoryName":"cPanel Email FAQs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2186,"CategoryName":"cPanel Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2204,"CategoryName":"Private Email: Video Overview"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":32,"CategoryName":"DNS settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":15,"CategoryName":"Namecheap Market"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2186,"CategoryName":"cPanel Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2266,"CategoryName":"Windows"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2287,"CategoryName":"SSL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2267,"CategoryName":"Android"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2208,"CategoryName":"3rd Party Services Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2204,"CategoryName":"Private Email: Video Overview"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/security-red.png","ShortDesc":"","CategoryId":14,"CategoryName":"SSL Certificates","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2217,"CategoryName":"Renewal"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2218,"CategoryName":"cPanel SSL Plugin"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2221,"CategoryName":"Multi-Domain SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2222,"CategoryName":"Cancellation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2223,"CategoryName":"Browser errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2224,"CategoryName":"Site Seal, Logo"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2238,"CategoryName":"SSL installation errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2290,"CategoryName":"CSR code"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2293,"CategoryName":"Automated SSL management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":38,"CategoryName":"SSL General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":67,"CategoryName":"Activation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":68,"CategoryName":"Validation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":69,"CategoryName":"Installation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":70,"CategoryName":"Reissuance"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/performance-red.png","ShortDesc":"","CategoryId":9,"CategoryName":"My Account","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":45,"CategoryName":"Account Security"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":43,"CategoryName":"Profile Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":44,"CategoryName":"Account Access"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2278,"CategoryName":"Handshake TLDs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":103,"CategoryName":"LVE (CloudLinux)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/affiliates-red.png","ShortDesc":"","CategoryId":55,"CategoryName":"Affiliates","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":89,"CategoryName":"SSH Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/tools-red.png","ShortDesc":"","CategoryId":2211,"CategoryName":"API & Resellers","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2227,"CategoryName":"SSL Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2229,"CategoryName":"Hosting Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":63,"CategoryName":"Namecheap API"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2196,"CategoryName":"WHMCS module for SSL"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/timer-red.png","ShortDesc":"","CategoryId":2212,"CategoryName":"Legacy Products","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":205,"CategoryName":"FTP questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2180,"CategoryName":"MySQL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2199,"CategoryName":"Hosting Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/premiumdns-red.png","ShortDesc":"","CategoryId":2231,"CategoryName":"PremiumDNS","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2194,"CategoryName":"Tips & Tricks"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"https://static.nc-img.com/live-resource/icons/knowledgebase/fastVPN_icon-150px.png","ShortDesc":"","CategoryId":2265,"CategoryName":"FastVPN","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2292,"CategoryName":"Browser Extensions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2274,"CategoryName":"General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2270,"CategoryName":"Routers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2272,"CategoryName":"TV"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2273,"CategoryName":"Gaming Consoles"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2268,"CategoryName":"macOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2269,"CategoryName":"iOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2271,"CategoryName":"Linux"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2266,"CategoryName":"Windows"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2267,"CategoryName":"Android"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":239,"CategoryName":"WHMCS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":33,"CategoryName":"SSL Installation"}],"status":200,"statusText":"OK"}}What is FS?
Forward Secrecy (also known as Perfect Forward Secrecy) is an attribute of the specific key exchange mechanisms in SSL/TLS security protocols that implies the independence of the session key generated during the secure session establishment from the set of long-term Public and Private keys and the session keys used in previous sessions.
The mission of the key exchange is to ensure that two parties will agree on a session key upon the security settings available for both participants of the secure negotiation and that no one else will know it.
For a better understanding, let’s review the non-FS key agreement based on the example of the RSA key exchange mechanism firstly. RSA key exchange is supported by nearly any application using SSL/TLS protocol.
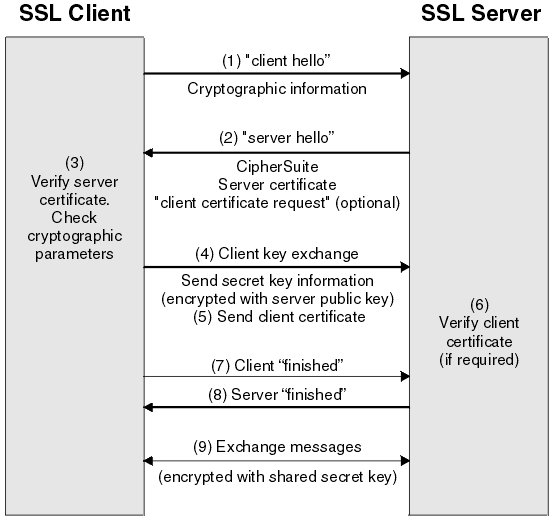
Here is how it works: the server sends its certificate, the client picks a random session key, encrypts it with the server’s Public key obtained from the certificate and sends it back to the server. The session key can only be decrypted with the server’s Private key that corresponds to the Public key, thus creating the secure session.
In such a way the server establishes hundreds of thousands sessions using the same key pair, creating a link between the long-term keys and the session key for each unique session.
As we see, the secrecy of the session key solely relies on the server’s Private key secrecy which leads to the obvious conclusion: what if someone gets hold of the Private key?
If the Private key is leaked or compromised, an adversary is able to go back in time and decrypt all the previously sniffed (recorded) traffic encrypted using the same long-term key pair and steal the sensitive information transmitted through the network channels.
A simple analogy, as if someone breaks into your house, he’ll be able to see not only what's in there right now, but also know everything from the past: all the people who used to live there, all the conversations that used to take place in the house or even the name of your cat.
By implementing the exchange mechanisms that provide Forward Secrecy, even though someone breaks into a house, he still won't know what was happening before he got there.
Benefits/Drawbacks
The mechanisms that provide FS use the Diffie-Hellman (DH) key exchange as key material, precisely its Ephemeral mode. OWASP (Open Web Application Security Project) gives the following definition of ephemeral keys:
Ephemeral keys are temporary keys used for one instance of a protocol execution and then thrown away. An ephemeral key has the benefit of providing forward secrecy, meaning a compromise of the site or service's long term (static) signing key does not facilitate decrypting past messages because the key was temporary and discarded (once the session terminated).
In other words, the session key generated upon the negotiated DH parameters is unique for each individual session, does not rely on the server’s long-term keys (they are only used for the server’s authentication purposes) and will be erased after the session is ended. Obviously, this increases drastically the protection of the encrypted traffic.
Only the Diffie-Hellman Ephemeral (DHE) and its lighter version based on Elliptic Curves (ECDHE) key exchange mechanisms provide the Forward Secrecy.
After all, both DHE and ECDHE degrade the website’s performance (i.e. page’s loading speed) when used with RSA long-term keys, as both imply the heavy arithmetics that significantly increase the CPU load. When used with ECDSA (Elliptic-Curve Digital Signature Algorithm) long-term keys however, the difference in performance is not so crucial. For now, EC keys are not yet so widely supported. Despite that, you can already get the certificate signed with EC key from us. Feel free to check more details here.
Using the cipher suites that provide key exchanges with FS only can cause some incompatibilities with legacy systems, but isn’t it a reasonable cost for such a security enhancement?
It is worth mentioning that you should pay special attention when enabling the support of the cipher suites that imply DHE key exchange as they are the main vector of the new vulnerability in TLS protocol discovered by the group of researchers who brought to us the FREAK Attack. The new attack is called Logjam. DHE with weak DH group and DHE_EXPORT cipher suites are affected.
In order to mitigate the attack, the support of the DHE-EXPORT cipher suites should be disabled. As for the DHE ciphers, it is recommended that the custom DH group is used instead. The size of the DH key in a custom DH cipher group should be increased so that it matches the recommended length of the long-term key (current standard is 2048-bit).
Some servers don’t have an option to set the custom DH groups or change the size of the DH key, therefore, the support of DHE cipher suites should be disabled. As an alternative, the ECDHE should be used. The ECDHE key exchange is slightly faster in comparison to DHE and is widely supported by the majority of web browsers.
Another drawback is that due to the server administrators’ unawareness, the Forward Secrecy can easily be broken. It is not enough to enable the support of the cipher suites with certain FS key exchange mechanisms on the server, but to prioritize them to be used by the server in the first place at all times.
Another way to mess up the Forward Secrecy is to configure the server to use the long duration session IDs or session tickets, which are used for the session resumption.
Ivan Ristic, the Director of Engineering at the cloud security firm Qualys, defines the following attack vectors in his article dedicated to Forward Secrecy:
“Server-side session management mechanisms could also impact forward secrecy. For performance reasons, session keys might be kept for many hours (or longer) after the conversation had been terminated.
In addition, there is an alternative session management mechanism called session tickets, which uses separate encryption keys that are infrequently rotated (possibly never in extreme cases). Unless you understand your session tickets implementation very well, this feature is best disabled to ensure it does not compromise forward secrecy.”
The methods how to check if the server uses the key exchange which provides Forward Secrecy are described in this article.Need help? We're always here for you.