| Subtotal | $0.00 |
| Subtotal | $0.00 |
In this article we have reviewed what is Perfect Forward Secrecy and how it works. Here we will discuss the way to check if your server supports FS.
There are lots of ways to check whether the server uses the key exchange that provides Forward Secrecy.
In this section we will review only a few of them, which, in our view, might come in handy.
Method 1. Check the connection details in your browser.
You can easily detect whether FS is supported by a server with your browser.
For Google Chrome, do the following:
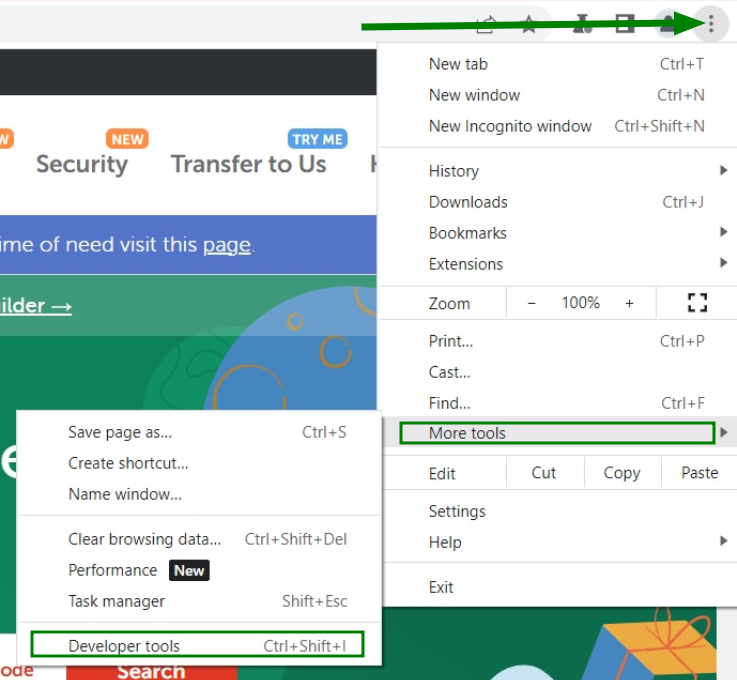
We have learned that only DHE and ECDHE key exchanges provide FS, so let's take a look at a few examples of how that would look: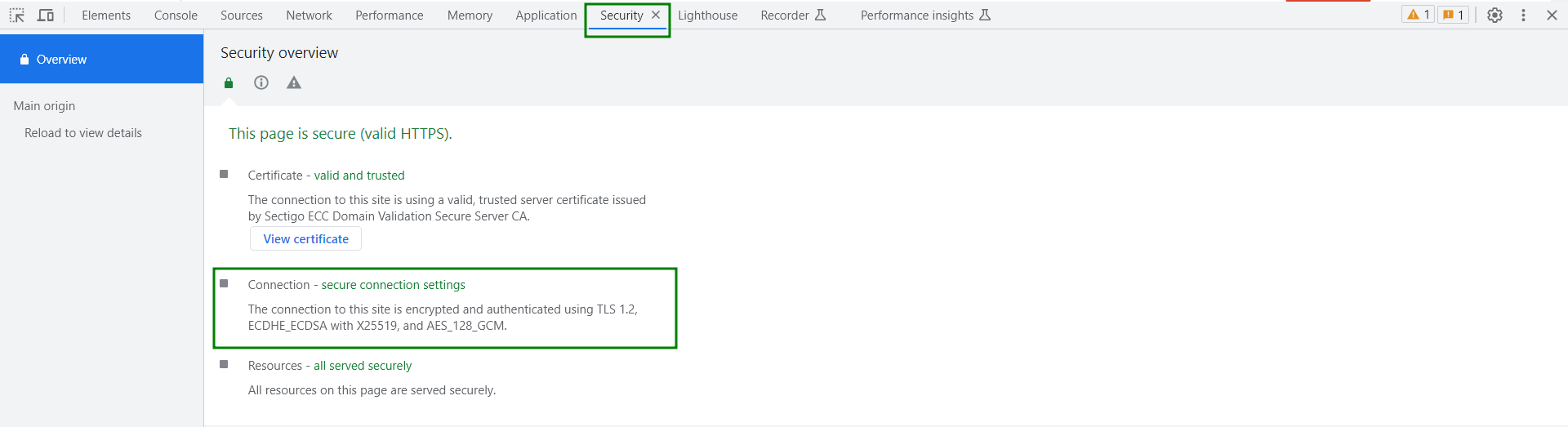
This example shows that our connection to Namecheap is secured using the AES_128_GCM encryption algorithm, while the session key generation relies on the ECDHE key exchange mechanism.
Also, the following message may appear:
Here, the key exchange is performed using X25519, which refers to the elliptic curve ECDH key exchange algorithm, and the actual data encryption is accomplished using the AES_256_GCM symmetric encryption algorithm.
In the example above, the same curve is used for the key exchange, and the AES_128_GCM symmetric encryption algorithm is used for the symmetric encryption algorithm.
In all cases, the combination of X25519 for key exchange and AES_256_GCM or AES_128_GCM for encryption supports FS.
For Mozilla Firefox, you can check in a similar way:
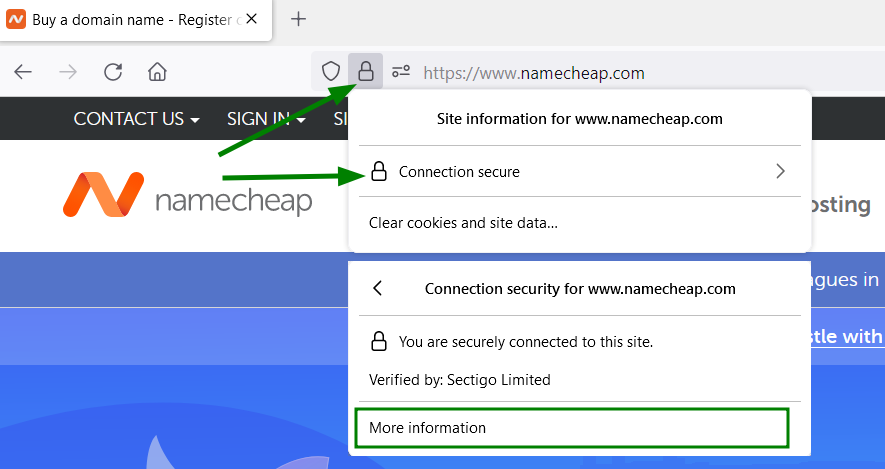
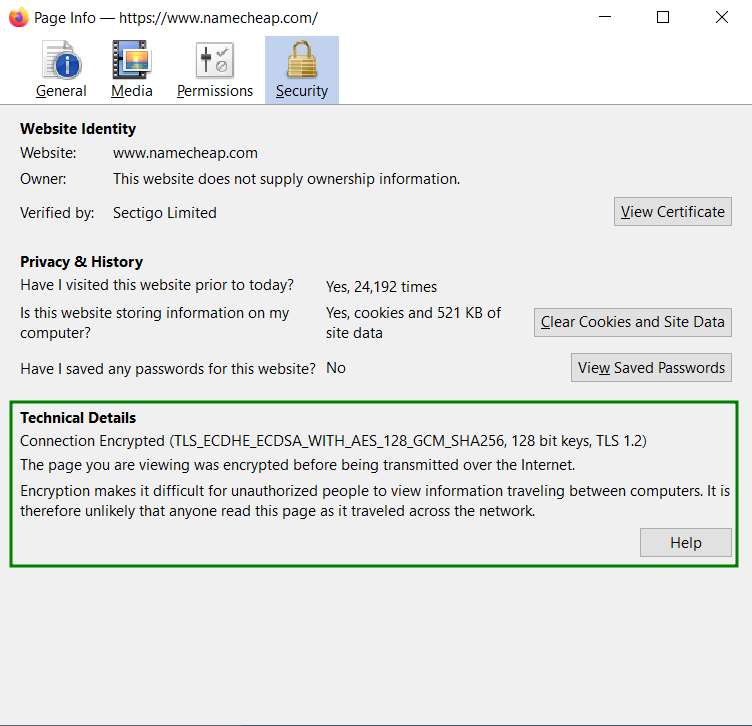
Again, we see that the RSA keys are used here for authentication purposes, the first part of the line (which contains ECDHE) is for the key exchange and the second part (AES ...) is for the encryption itself.
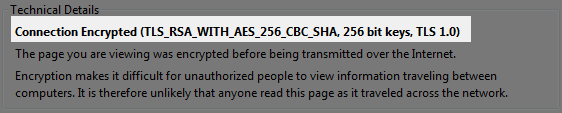
Non-FS connection will look like this:
Method 2. Check it with SSL Labs server test.
Another easy way to check the support of the FS key exchanges is to run the SSL Labs test.
Just enter the domain name you wish to check and hit the Submit button.
This global tool allows you to check a great number of the server-side and SSL-related settings and see the grade of the current configuration.
In order to preeminently check the support of the Forward Secrecy property, after the server analysis is completed, you will need to scroll the results page down to the “Protocol Details” section and check the value of the Forward Secrecy parameter:
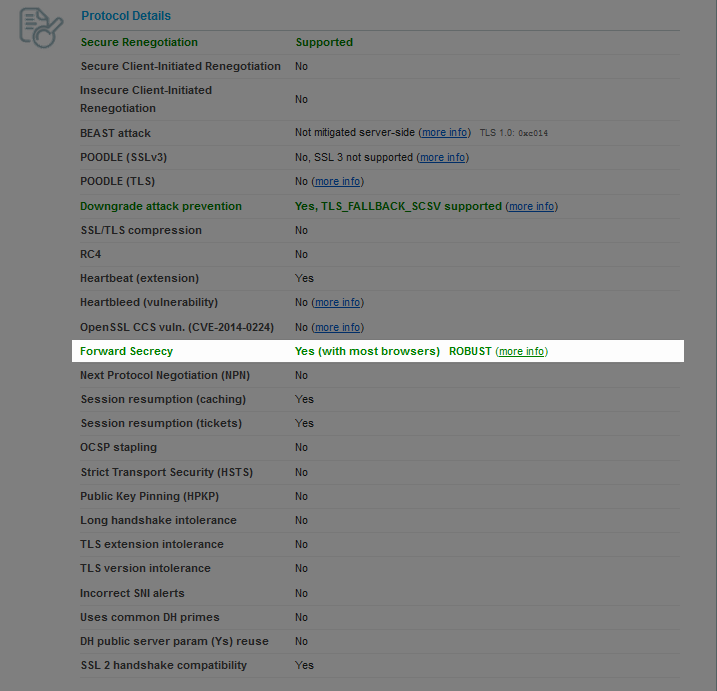
Sometimes, you can see the following result:
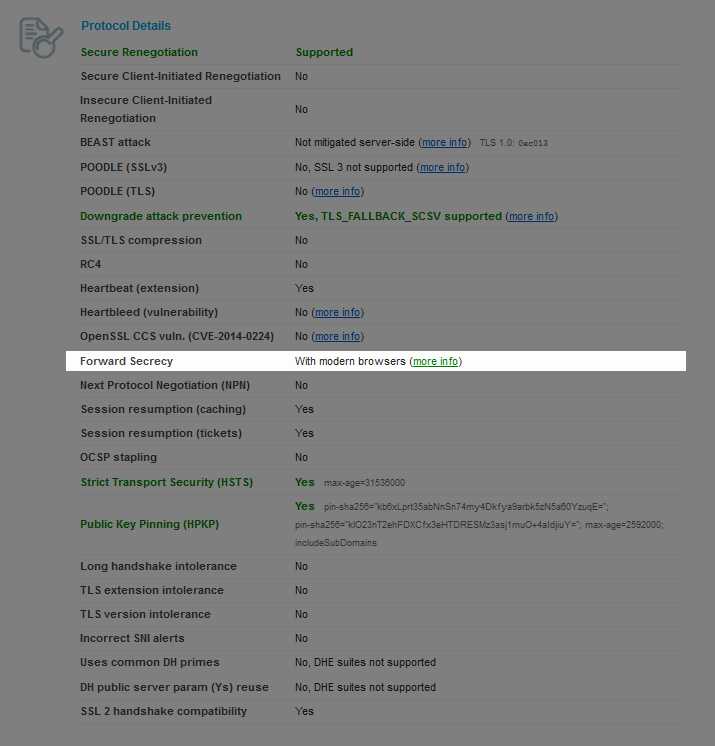
This means that the server is configured to prioritize the key exchanges that provide FS when connecting to modern browsers, however, has a few non-FS cipher suites enabled to include the support of legacy systems.
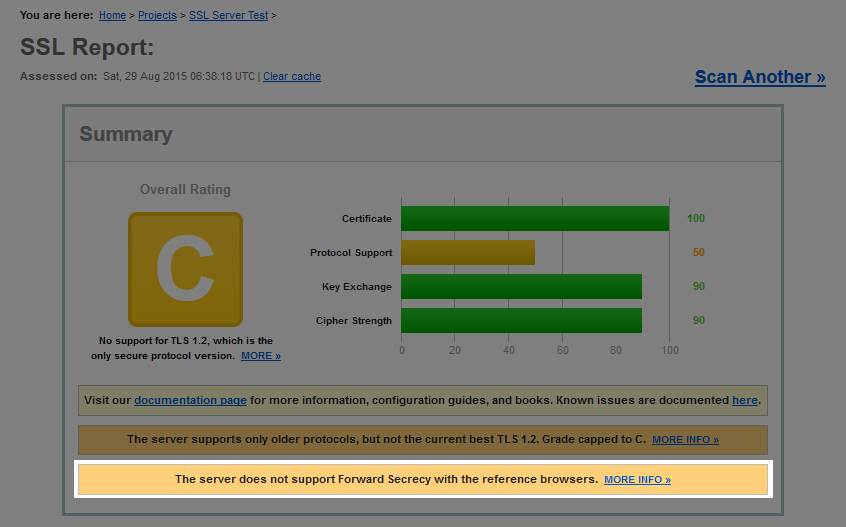
If the server does not support the FS property, you’ll be notified about that on the Summary page:
Method 3. Check it with OpenSSL.
OpenSSL toolkit also allows you to check the support of the FS key exchanges.
The following commands should be used:
openssl s_client -connect example.com:443 -cipher "ECDHE, EECDH"
openssl s_client -connect example.com:443 -cipher "DHE, EDH"
Be sure to change the example.com to the domain you wish to check.
ECDHE, EECDH
and DHE, EDH define the Elliptic-Curve Diffie-Hellman and Diffie-Hellman Ephemeral key exchange mechanisms respectively.
If the command results in a “sslv3 alert handshake failure” error, the Forward Secrecy property is not supported by the server.
Note: If the server’s certificate uses SNI, you’ll need to include the “-servername example.com” option. Example:
openssl s_client -connect example.com:443 -servername example.com -cipher "ECDHE, EECDH"
FS at Namecheap hosting
At Namecheap, we are keeping our finger on the pulse of the modern technologies, therefore, the Forward Secrecy is deployed on all our hosting servers, including the Value, Premium, Business and Reseller plans.
Taking into account the aforementioned vulnerability in DHE and DHE_EXPORT ciphers with the weak DH group called Logjam, the support of the DHE key agreement was completely disabled. ECDHE is used instead.
Elliptic-Curve Diffie-Hellman (ECDHE) key exchange avoids all known feasible cryptanalytic attacks, and modern web browsers now prefer ECDHE over the original DHE key exchange mechanism.
This, however, brings up some compatibility issues with legacy browsers, like IE6 on Windows XP.
Conclusion
Forward Secrecy significantly improves securing encrypted traffic transmitted through public channels. It mitigates the risk of previous sessions'; secrecy being disclosed if the server's secret key is compromised. According to SSL Pulse, Forward Secrecy is not supported on about 0.4% of all websites, while a few years ago, 30% of sites didn't support it. This indicates a positive trend toward increasing the security of encrypted communications.
Need help? We're always here for you.