| Subtotal | $0.00 |
| Subtotal | $0.00 |
In this article, you'll find standard notifications for SSL certificates in modern Chrome browsers. Below is a list of warnings that may pop up while browsing websites via https://.
Note
: From September 2023, the
Chrome
Browser's SSL padlock icon will be replaced by a
tune icon
because,
according to Google
, a secure HTTPS connection has become the norm rather than the exception. The tune icon is not a trust indicator itself, but it will provide more detailed information about a website's connection and draw attention to its settings.
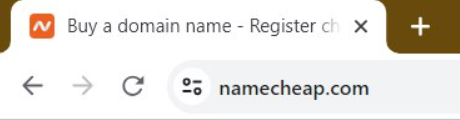
To check SSL-related notifications in Chrome, click the padlock or tune icon in the address bar.
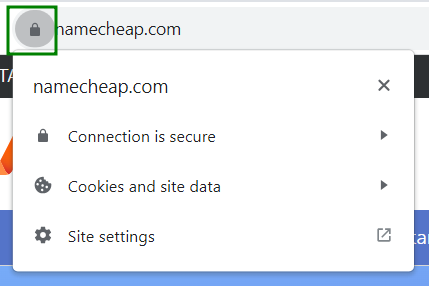
For more information, press Ctrl+ Shift+ J(or Command+Option+J for Mac) and choose the Security tab.
You may see this error message after clicking the padlock or tune icon in the address bar. 
HTTP links in the HTML code of the webpage cause it. You can check the links in the browser by pressing the combination Ctrl+ Shift + J (or Command+Option+J for Mac) and clicking Console. Find more information about this issue and steps to fix it here.
This warning appears for all certificates signed with the SHA-1 signature algorithm. It appears on the webpage, as well as the pop-up window after clicking "Not secure" in the address bar:
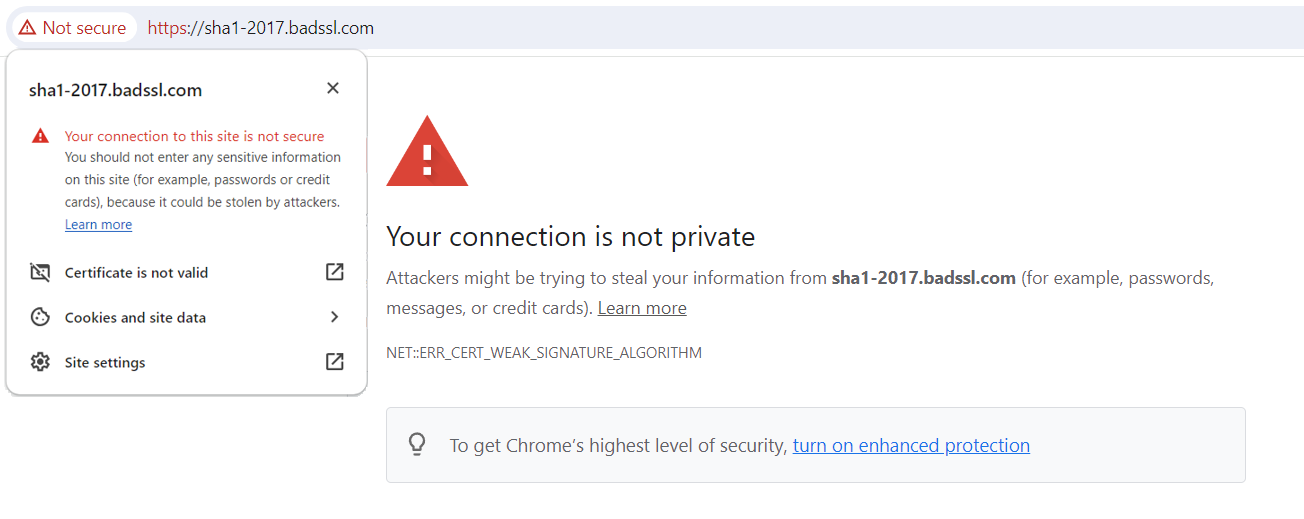
To get more detailed information, press Ctrl+ Shift + J and choose the Security tab:
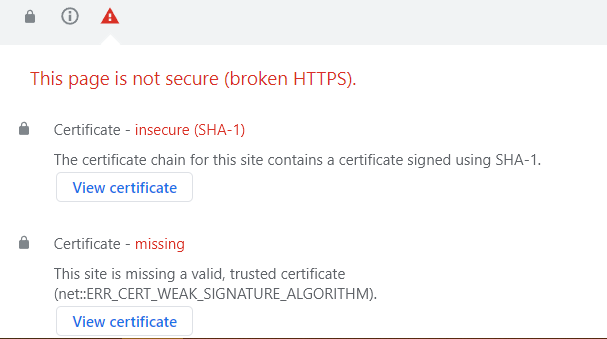
This warning may appear for websites with certificates installed long ago. Earlier Certificate Authorities used the SHA-1 algorithm to sign SSLs, which has since been deprecated. To fix this issue, the certificate should be reissued and reinstalled on the server. Our migration to the SHA-256 algorithm was completed on November 6, 2014, and since then, all our new and reissued certificates are signed with this more robust encryption.
With this issue, the warning is not shown on the pop-up window after clicking the padlock/tune icon:
You can see it by entering Ctrl+ Shift + J, heading to the Security tab, then selecting Connection:

This message means the website encrypts the traffic using a weak cipher suite or SSL/TLS protocol.
It is better to turn off weak ciphers and protocols on the server (e.g., SSLv2, SSLv3, RC4, SHA1, or MD5 hashes used for message authentication) to be safe. You can use this analyzer to scan your website to detect which cipher or protocol causes the warning.
Root access is required to change the server configurations and disable the weak ciphers. If you don't have access, please contact your hosting or server provider for assistance.
This warning is displayed on the webpage itself and after clicking "Not secure" in the address bar:

The same error is shown in the Security tab once you enter Ctrl+ Shift + J: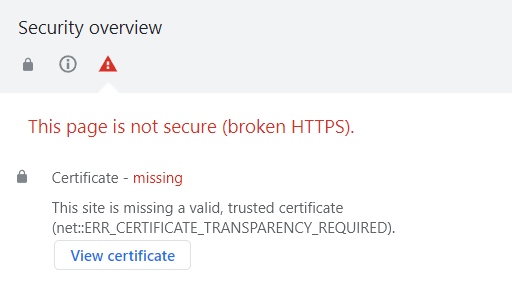
This warning is related to the Certificate Transparency Project, which aims to monitor SSL certificates in real time, making the issuance and use of fake SSLs almost impossible. This project is implemented on the Certificate Authority side.
All Comodo CA (now Sectigo CA ) issued SSL certificates comply with Chromium's CT Policy since March 23, 2018. Therefore customers who use Comodo (now Sectigo) certificates don't need to take any action to comply with the Google Chrome mandate from April 2018.
The following links might also be useful for you:
Need help? We're always here for you.