{"/api/v1/ncpl/simplekb/getarticle:\"{\\\"articleId\\\":9588,\\\"categoryId\\\":38}\"":{"body":{"Id":9588,"FriendlyId":"","ArticleTypeId":0,"Title":"What is Certificate Transparency?","ArticleName":"What is Certificate Transparency?","ArticleSummary":null,"PreponedSummary":false,"Approved":true,"Body":"DQoJCTxwPlNvbWUgb2YgdXMgbWF5IGhhdmUgYWxyZWFkeSBoZWFyZCB0aGUgbmV3IHdvcmQgY29tYmluYXRpb24gd2hpY2ggaGFkIHNwcmVhZCBvdmVyIHRoZSBJbnRlcm5ldCBzb2NpZXR5IC0gPGI+Q2VydGlmaWNhdGUgVHJhbnNwYXJlbmN5PC9iPi4gVGhpcyBwcm9jZXNzIGFuZCwgd2hpY2ggaXMgbW9yZSBpbXBvcnRhbnQsIHRoZSBub3ZlbHR5IG9mIHRoaXMgY29uY2VwdCBpdHNlbGYgaGF2ZSBiZWVuIHJlY2VudGx5IGFubm91bmNlZCBieSA8YSBocmVmPSJodHRwczovL2RyaXZlLmdvb2dsZS5jb20vdmlld2Vybmcvdmlld2VyP2E9diZhbXA7cGlkPXNpdGVzJmFtcDtzcmNpZD1aR1ZtWVhWc2RHUnZiV0ZwYm54alpYSjBhV1pwWTJGMFpYUnlZVzV6Y0dGeVpXNWplWHhuZURvME9EaGpOR1JsT1RJeU16WXdOVGN6IiBsaW5rdGV4dD0iR29vZ2xlIEluYy4iIGxpbmt0eXBlPSJDdXN0b20iIHRhcmdldD0iX2JsYW5rIj5Hb29nbGUgSW5jLjwvYT4gIFNvLCB3aGF0IGNlcnRpZmljYXRlIHRyYW5zcGFyZW5jeSBhY3R1YWxseSBpcz8gTGV0IHVzIGhhdmUgYSBsb29rLjwvcD4NCgkJPHA+QXMgb3JpZ2luYWxseSBkZWZpbmVkIGFuZCBwbGFubmVkIGJ5IDxhIGhyZWY9Imh0dHBzOi8vZW4ud2lraXBlZGlhLm9yZy93aWtpL05ldHNjYXBlIiBsaW5rdGV4dD0iTmV0c2NhcGUiIGxpbmt0eXBlPSJDdXN0b20iIHRhcmdldD0iX2JsYW5rIj5OZXRzY2FwZTwvYT4gYW5kIG90aGVycyBpbiB0aGUgbWlkLTE5OTBzLCBjZXJ0aWZpY2F0ZSBpc3N1YW5jZSBwcm9jZXNzIGltcGxpZXMgdGhhdCBhIDxhIGhyZWY9Imh0dHBzOi8vZW4ud2lraXBlZGlhLm9yZy93aWtpL0NlcnRpZmljYXRlX2F1dGhvcml0eSIgbGlua3RleHQ9IkNlcnRpZmljYXRlIEF1dGhvcml0eSIgbGlua3R5cGU9IkN1c3RvbSIgdGFyZ2V0PSJfYmxhbmsiPkNlcnRpZmljYXRlIEF1dGhvcml0eTwvYT4gKENBKSBzaG91bGQgZ2VuZXJhdGUgYW5kIHByZXNlbnQgdGhlIGNlcnRpZmljYXRlIGZvciB0aGUgY2VydGlmaWNhdGUgcmVxdWVzdGVyIChkb21haW4gb3duZXIsIHNlcnZlciBhZG1pbmlzdHJhdG9yKSBmb3IgcmV2aWV3IGFuZCBhcHByb3ZhbCwgcHJpb3IgdG8gdGhlIGFjdHVhbCBTU0zigJlzIGlzc3VhbmNlLiBPbmNlIGlzc3VlZCwgdGhlIENlcnRpZmljYXRlIEF1dGhvcml0eSBwdWJsaXNoZXMgdGhlIGNlcnRpZmljYXRlIGluIGFuIGluZGVwZW5kZW50IHJlcG9zaXRvcnkgd2hpY2ggd2lsbCBwcm92ZSB0aGF0IHRoZSByZXF1ZXN0ZXIgaGFzIGJlZW4gYXdhcmUgb2YgdGhlIGNlcnRpZmljYXRl4oCZcyBpc3N1YW5jZS4gVGhhdCBpbmRlcGVuZGVudCByZXBvc2l0b3J5IGFsbG93cyBwdWJsaWMga2V5ICh3aGljaCBpcyBhbiBlc3NlbnRpYWwgcGFydCBvZiBTU0wgY2VydGlmaWNhdGUpIHZlcmlmaWNhdGlvbiBhbmQgdmFsaWRpdHkgY2hlY2sgPGI+cHJpb3I8L2I+IHRvIGVzdGFibGlzaGluZyBhbmQgbmVnb3RpYXRpbmcgYSBzZWN1cmUgc2Vzc2lvbiB3aXRoIHRoZSBzZXJ2ZXIuIEluIGEgd2F5LCBhIHB1YmxpYyBrZXkgY2FuIGJlIDxiPmFsdGVybmF0aXZlbHk8L2I+IHZhbGlkYXRlZCBiZXNpZGVzIGZvciBnZXR0aW5nIGl0IGZyb20gdGhlIHNlcnZlciBzb2xlbHkgZHVyaW5nIHNlc3Npb24gbmVnb3RpYXRpb24uIDxiPkNlcnRpZmljYXRlIFRyYW5zcGFyZW5jeTwvYj4gcHJvamVjdCBicmluZ3MgdXAgYSBuZXcgd2F5IG9mIG1ha2luZyBjZXJ0aWZpY2F0ZeKAmXMgaXNzdWFuY2UgcHJvY2VzcyBwdWJsaWNseSBhdmFpbGFibGUsIG9wZW4gYW5kLCBubyBtYXR0ZXIgaG93IHRhdXRvbG9naWNhbCBpdCBzb3VuZHMsIHRyYW5zcGFyZW50LjwvcD4NCgkJPHA+DQoJCQkJPGk+DQoJCQkJCQk8Yj5Ib3cgaXMgdGhlIGNlcnRpZmljYXRlIHRyYW5zcGFyZW5jeSBhY2hpZXZlZD88L2I+DQoJCQkJPC9pPg0KCQk8L3A+DQoJCTxwPkNlcnRpZmljYXRlIHRyYW5zcGFyZW5jeSAoZnVydGhlciA8Yj5DVDwvYj4pIGlzIGFjaGlldmVkIGJ5IGhhdmluZyBDZXJ0aWZpY2F0ZSBBdXRob3JpdGllcyBwb3N0IGNlcnRpZmljYXRlcyB0byBwdWJsaWNseSBhY2Nlc3NpYmxlIFF1YWxpZmllZCBDVCBsb2dzLiBUaGVyZSBhcmUgZm91ciBtYWluIHBhcnRpY2lwYW50cyBpbiB0aGUgQ1Q6IDwvcD4NCgkJPHVsPg0KCQkJCTxsaT5DQXM8L2xpPg0KCQkJCTxsaT5Mb2cgc2VydmVycyBhcyBwdWJsaWMgcmVwb3NpdG9yaWVzIGZvciBjZXJ0aWZpY2F0ZXM8L2xpPg0KCQkJCTxsaT5BdWRpdG9ycyAtIGJyb3dzZXIgb2YgYW55IGNsaWVudCB0aGF0IGFjY2VwdHMgY2VydGlmaWNhdGU8L2xpPg0KCQkJCTxsaT5Nb25pdG9ycyAtIHB1YmxpY2x5IHJ1biBzZXJ2ZXJzIHdob3NlIGFpbSBpcyBtb25pdG9yaW5nIG5ld2x5IGFkZGVkIGNlcnRpZmljYXRlcyB0byBsb2cgc2VydmVycyBmb3IgZGV0ZWN0aW5nIG1pcy1pc3N1ZWQgY2VydGlmaWNhdGVzIGZvciBjZXJ0YWluIHdlYnNpdGVzLjwvbGk+DQoJCTwvdWw+DQoJCTxwPg0KCQkJCTxiPkZpcnN0bHksPC9iPiBhIENlcnRpZmljYXRlIEF1dGhvcml0eSBjcmVhdGVzIHNvIGNhbGxlZCBwcmUtY2VydGlmaWNhdGUgd2hpY2ggY29udGFpbnMgbWFpbiBpbmZvcm1hdGlvbiB0aGF0IHdpbGwgYmUgcmVmbGVjdGVkIGluIHRoZSBmdXR1cmUgY2VydGlmaWNhdGUgYW5kIHNlbmRzIGl0IHRvIHRoZSB0cnVzdGVkIExvZyBzZXJ2ZXIuIDwvcD4NCgkJPHA+DQoJCQkJPGI+SW4gaXRzIHR1cm48L2I+LCBMb2cgc2VydmVyIGFjY2VwdHMgdGhpcyBpbmZvcm1hdGlvbiBhbmQgcmVwbGllcyB3aXRoIGEg4oCYc2lnbmVkIGNlcnRpZmljYXRlIHRpbWVzdGFtcCAoU0NUKeKAmSB3aGljaCBpcywgYnkgbmF0dXJlLCBhIOKAmHByb21pc2XigJkgdG8gYWRkIHRoZSBjZXJ0aWZpY2F0ZSB0byB0aGUgbG9nIHdpdGhpbiBhIGNlcnRhaW4gcGVyaW9kIG9mIHRpbWUuIFRoaXMgdGltZSBmcmFtZSwga25vd24gYXMgPGI+TWF4aW11bSBNZXJnZSBEZWxheSAoTU1EKTwvYj4sIHNldHMgdGhlIHJlYXNvbmFibGUgcGVyaW9kIHdoZW4gdGhlIGNlcnRpZmljYXRlIGlzIGFkZGVkIHRvIHRoZSBMb2cgc2VydmVyLiBPbmUgbWlnaHQgcXVlc3Rpb24gb25lc2VsZiBpZiB0aGUgPGI+TU1EPC9iPiB2YWx1ZSBjYW4gYWN0dWFsbHkgZGVsYXkgb3IgcG9zdHBvbmUgdGhlIGNlcnRpZmljYXRl4oCZcyBpc3N1YW5jZS4gPGI+TU1EIGhhcyBpbmZsdWVuY2UgbmVpdGhlciBvbiBTU0zigJlzIGlzc3VhbmNlIG5vciBvbiBjZXJ0aWZpY2F0ZeKAmXMgdXNhZ2UuPC9iPiBUaGUgbGFyZ2VzdCBNTUQgdGltZWZyYW1lIGlzIDI0IGhycywgbWVhbmluZyB0aGF0IGFsbCBuZXdseSBpc3N1ZWQgY2VydGlmaWNhdGVzIHdpbGwgYmUgYXZhaWxhYmxlIGluIGxvZyBtYXhpbXVtIHdpdGhpbiAyNCBocnMgb25jZSBTQ1QgaXMgZ2VuZXJhdGVkLjwvcD4NCgkJPHA+U0NUIGdvZXMg4oCYaGFuZCBpbiBoYW5k4oCZIHdpdGggdGhlIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc2VjdXJpdHkvc3NsLWNlcnRpZmljYXRlcy8iIGxpbmt0ZXh0PSJTU0wgY2VydGlmaWNhdGUiIGxpbmt0eXBlPSJDdXN0b20iIHRhcmdldD0iX2JsYW5rIj5TU0wgY2VydGlmaWNhdGU8L2E+IHRocm91Z2hvdXQgaXRzIGxpZmUgY3ljbGUsIHVudGlsIHRoZSBleHBpcmF0aW9uIG9yIHJldm9jYXRpb24uIDwvcD4NCgkJPHA+U0NUIGlzIGFjY2VwdGVkIGJ5IHRoZSBDZXJ0aWZpY2F0ZSBBdXRob3JpdHkgYW5kIGludGVncmF0ZWQgZWl0aGVyIGluIHRoZSBib2R5IG9mIHRoZSBjZXJ0aWZpY2F0ZSBvciBwcmVzZW50ZWQgYnkgPGEgaHJlZj0iaHR0cHM6Ly90b29scy5pZXRmLm9yZy9odG1sL3JmYzY5NjIjc2VjdGlvbi0zIiBsaW5rdGV4dD0ib3RoZXIgbWVhbnMiIGxpbmt0eXBlPSJDdXN0b20iIHRhcmdldD0iX2JsYW5rIj5vdGhlciBtZWFuczwvYT4uIFNDVCBwcmVzZW5jZSBhbmQgYXZhaWxhYmlsaXR5IGluIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC83ODYvMzgvd2hhdC1pcy1hbi1zc2wtY2VydGlmaWNhdGUtYW5kLXdoYXQtaXMtaXQtdXNlZC1mb3IiIGxpbmt0ZXh0PSJTU0wgQ2VydGlmaWNhdGUiIGxpbmt0eXBlPSJDdXN0b20iIHRhcmdldD0iX2JsYW5rIj5TU0wgQ2VydGlmaWNhdGU8L2E+IGl0c2VsZiBzZXJ2ZXMgYXMgYSBzaWduYWwgdGhhdCB0aGUgY2VydGlmaWNhdGUgaGFzIGJlZW4gcHVibGlzaGVkIGZvciByZXZpZXcuIFRoZXJlIGFyZSB0aHJlZSBnZW5lcmFsIG1ldGhvZHMgZm9yIENUIHRvIGRlbGl2ZXIgU0NUIHdpdGggdGhlIGNlcnRpZmljYXRlczogPGI+eDUwOXYzIGV4dGVuc2lvbjwvYj4gKHdoaWNoIGFjdHVhbGx5IHJlcXVpcmVzIG5vIGFkZGl0aW9uYWwgYWN0aW9ucyBmcm9tIHNlcnZlciBvcGVyYXRvciksIDxiPlRMUyBleHRlbnNpb248L2I+ICh3aGljaCBpcyB0byBiZSB1c2VkIGJ5IHNpdGUgb3BlcmF0b3Igd2l0aCB0eXBlIHNpZ25lZF9jZXJ0aWZpY2F0ZV90aW1lc3RhbXAgZm9yIFNDVCBkZWxpdmVyaW5nIHRvIHRoZSBjbGllbnQgZHVyaW5nIDxhIGhyZWY9Imh0dHBzOi8vZG9jcy5taWNyb3NvZnQuY29tL2VuLXVzL3dpbmRvd3MvZGVza3RvcC9TZWNBdXRoTi90bHMtaGFuZHNoYWtlLXByb3RvY29sIiBsaW5rdGV4dD0iVExTIEhhbmRzaGFrZSIgbGlua3R5cGU9IkN1c3RvbSIgdGFyZ2V0PSJfYmxhbmsiPlRMUyBIYW5kc2hha2U8L2E+KSBhbmQgPGI+T0NTUCBTdGFwbGluZzwvYj4uPC9wPg0KCQk8cD4NCgkJCQk8aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvVHJhbnNwYXJlbmN5XzEuanBnIiBhbHQ9IlRyYW5zcGFyZW5jeV8xLmpwZyIgd2lkdGg9IjM1MCIgaGVpZ2h0PSI1MDAiIGJvcmRlcj0iMCIgLz4NCgkJPC9wPg0KCQk8cD4NCgkJCQk8aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvVHJhbnNwYXJlbmN5XzIucG5nIiBhbHQ9IlRyYW5zcGFyZW5jeV8yLmpwZyIgd2lkdGg9IjM1MCIgaGVpZ2h0PSI0NzAiIGJvcmRlcj0iMCIgLz4NCgkJPC9wPg0KCQk8cD5Nb3JlIGRldGFpbHMgb24gdGhlc2UgbWV0aG9kcyBjYW4gYmUgc2VlbiA8YSBocmVmPSJodHRwczovL3d3dy5jZXJ0aWZpY2F0ZS10cmFuc3BhcmVuY3kub3JnL2hvdy1jdC13b3JrcyIgbGlua3RleHQ9ImhlcmUiIGxpbmt0eXBlPSJDdXN0b20iIHRhcmdldD0iX2JsYW5rIj5oZXJlPC9hPiwgYnV0IHRoZSBtYWluIGlkZWEgaXMgdGhhdCBTaWduZWQgQ2VydGlmaWNhdGUgVGltZXN0YW1wIGlzIHByZXNlbnRlZCBhbG9uZyB3aXRoIHRoZSBjZXJ0aWZpY2F0ZSBpdHNlbGYgZHVyaW5nIHNlc3Npb24gbmVnb3RpYXRpb24uIDwvcD4NCgkJPHA+DQoJCQkJPGk+DQoJCQkJCQk8Yj5Qcm9zIGFuZCDigKYuUHJvcyE8L2I+DQoJCQkJPC9pPg0KCQk8L3A+DQoJCTxwPlRoZSBtYWluIGFuZCB0aGUgdmVyeSBmaXJzdCBhZHZhbnRhZ2Ugd2hpY2ggY29tZXMgdG8gb3VyIG1pbmQgaXMgPGI+dHJ1c3Q8L2I+LiBIYXZpbmcgY29tcGFueSBkZXRhaWxzIHB1Ymxpc2hlZCBhbmQgb3BlbiBmb3Igdmlld2luZyBidWlsZHMgYSB3YXkgPGI+YmV0dGVyIGltYWdlIHdoaWxlIGRvaW5nIG9ubGluZSBidXNpbmVzczwvYj4uIFRoaXMgcG9pbnQgaXMgYmVuZWZpY2lhbCBub3Qgb25seSBmb3IgQ0FzLCBkb21haW4gb3duZXJzIGFuZCBzZXJ2ZXIgb3BlcmF0b3JzLCBidXQgYWxzbyBmb3IgYSBncmVhdCBudW1iZXIgb2YgZW5kIHVzZXJzLiBHb29nbGUgaXMgY3VycmVudGx5IHJ1bm5pbmcgYSBDZXJ0aWZpY2F0ZSBUcmFuc3BhcmVuY3kgbG9nIHdoaWNoIGlzIGZpbGxlZCBpbiB3aXRoIHRoZSBjZXJ0aWZpY2F0ZXMgcmV0cmlldmVkIGZyb20gdGhlIHdlYiwgYW5kIGFjdGl2ZSB3b3JrIGlzIHBlcmZvcm1lZCBvbiBtb25pdG9yaW5nIGFuZCBhdWRpdGluZyBzb2Z0d2FyZSB3aGljaCBjYW4gYmUgcmV2aWV3ZWQgPGEgaHJlZj0iaHR0cHM6Ly9jb2RlLmdvb2dsZS5jb20vYXJjaGl2ZS9wL2NlcnRpZmljYXRlLXRyYW5zcGFyZW5jeS8iIGxpbmt0ZXh0PSJoZXJlIiBsaW5rdHlwZT0iQ3VzdG9tIiB0YXJnZXQ9Il9ibGFuayI+aGVyZTwvYT4uIFRoZSBkZXZlbG9wbWVudCBvZiBhIG5ldyBHb29nbGUgQ2hyb21lIHZlcnNpb24gaXMgY3VycmVudGx5IGdvaW5nIG9uLiBBdCBzb21lIHBvaW50LCBpdCB3aWxsIGJlIHVwZGF0ZWQgdG8gc2hvdyBhIHdhcm5pbmcgbWVzc2FnZSBwcmlvciB0byBlc3RhYmxpc2hpbmcgYSBjb25uZWN0aW9uIHRvIGEgd2Vic2l0ZSB3aXRob3V0IGEgdmVyaWZpZWQgU0NULiBBZnRlciBhZG9wdGlvbiBvZiBjZXJ0aWZpY2F0ZSB0cmFuc3BhcmVuY3kgYnkgQ2VydGlmaWNhdGUgQXV0aG9yaXRpZXMgYW5kIGJyb3dzZXJzIGluY3JlYXNlcywgQ2hyb21lIGlzIHBsYW5uZWQgdG8gYmUgbW9kaWZpZWQgYWdhaW4sIHNvIHRoYXQgbm8gY29ubmVjdGlvbiB0byBhIHdlYiBzaXRlIHdpdGhvdXQgYSB2YWxpZCBTQ1QgYWxvbmcgd2l0aCB0aGUgY2VydGlmaWNhdGUgaXMgcGVyZm9ybWVkIChidXQgdGhpcyBzZXR0aW5nIGNhbiBiZSBjaGFuZ2VkIGJ5IGEgQ2hyb21lIHVzZXIpLiA8L3A+DQoJCTxwPg0KCQkJCTxiPkFub3RoZXIgYWR2YW50YWdlPC9iPiBjb25jZXJucyBDZXJ0aWZpY2F0ZSBBdXRob3JpdGllc+KAmSBidXNpbmVzcyBtb2RlbDogU1NMIGNlcnRpZmljYXRlcyBhcmUgaXNzdWVkIGp1c3QgdGhlIHdheSB0aGV5IHdlcmUsIGV4Y2VwdCBmb3Igb25lIGV4dHJhIHN0ZXA6IGZpcnN0LCB0aGUgY2VydGlmaWNhdGUgaXMgc2VudCB0byBzZXZlcmFsIExvZyBzZXJ2ZXJzIHRvIHJlY2VpdmUgYW5kIGluY2x1ZGUgYSB0aW1lc3RhbXAgdG8gdGhlIFNTTC4gRG9tYWluIG93bmVycyBvciBzZXJ2ZXIgYWRtaW5pc3RyYXRvcnMgd2lsbCBub3QgbmVlZCB0byBhZGp1c3QgdG8gbmV3IFNTTC1wZXJmb3JtYW5jZSBwcm9jZWR1cmUuIFRMUyBIYW5kc2hha2UgcmVtYWlucyB1bmNoYW5nZWQsIGJ1dCB0aGUgZG9tYWluL3NlcnZlciBvd25lciBpcyBhYmxlIHRvIG1vbml0b3IgdGhlIGNlcnRpZmljYXRlcyBhbmQgYmUgc3VyZSB0aGF0IDxiPm5vIHVucmVxdWVzdGVkIG9yIHVuYXBwcm92ZWQgY2VydGlmaWNhdGVzIGFyZSBpc3N1ZWQgZm9yIGhpcy9oZXIgZG9tYWluIG9yIHNlcnZlcjwvYj4uPC9wPg0KCQk8cD4NCgkJCQk8aT4NCgkJCQkJCTxiPkkgYW0gZm9yIHRyYW5zcGFyZW5jeSEgQnV0IGhvdyBkb2VzIHRoaXMgYWZmZWN0IG15IEVWIGNlcnRpZmljYXRlIHdpdGggTmFtZWNoZWFwIEluYy4/PC9iPg0KCQkJCTwvaT4NCgkJPC9wPg0KCQk8cD5BbGwgRXh0ZW5kZWQgVmFsaWRhdGlvbiAoRVYpIGNlcnRpZmljYXRlcyB3aXRoIGFuIGV4cGlyYXRpb24gZGF0ZSBiZXlvbmQgRGVjZW1iZXIgMjAxNSBzaG91bGQgc3VwcG9ydCBjZXJ0aWZpY2F0ZSB0cmFuc3BhcmVuY3kuIFRoaXMgY29uY2VybnMgYWxyZWFkeSBpc3N1ZWQgRVYgY2VydGlmaWNhdGVzIGFzIHdlbGwuIEl0IGlzIHBsYW5uZWQgb24gb3IgYWZ0ZXIgRmVicnVhcnkgMXN0LCAyMDE1IHRvIDxpPnN0b3AgZGlzcGxheWluZyB0aGUgR3JlZW4gQmFyPC9pPiBpbiBHb29nbGUgQ2hyb21lLCBpZiBhIHZhbGlkIGFuZCB2ZXJpZmllZCBTQ1QgaXMgbm90IHByb3ZpZGVkIGFsb25nIHdpdGggYW4gRVYgY2VydGlmaWNhdGUgZHVyaW5nIHNlY3VyZSBzZXNzaW9uIG5lZ290aWF0aW9uLiBUaGUgPGI+ZXhhY3QgdGltZSBmcmFtZSBoYXMgbm90IGJlZW4gYW5ub3VuY2VkPC9iPiBzbyBmYXIsIGFuZCBpdCBkZXBlbmRzIG9uIEdvb2dsZSBDaHJvbWUgcmVsZWFzZSBzY2hlZHVsZS4gPC9wPg0KCQk8cD4NCgkJCQlDb21vZG8gKG5vdyA8YSBocmVmPSJodHRwczovL3NlY3RpZ28uY29tIiBsaW5rdGV4dD0iU2VjdGlnbyIgbGlua3R5cGU9IkN1c3RvbSIgdGFyZ2V0PSJfYmxhbmsiPlNlY3RpZ288L2E+KSBDZXJ0aWZpY2F0ZSBBdXRob3JpdHkgLSBvdXIgU1NMIHZlbmRvciAtIHN1cHBvcnRzIENlcnRpZmljYXRlIFRyYW5zcGFyZW5jeSBmb3IgPGEgaHJlZj0iaHR0cHM6Ly93d3cubmFtZWNoZWFwLmNvbS9zZWN1cml0eS9zc2wtY2VydGlmaWNhdGVzL2V4dGVuZGVkLXZhbGlkYXRpb24uYXNweCIgdGFyZ2V0PSJfYmxhbmsiPkVWIGNlcnRpZmljYXRlczwvYT4gc3RhcnRpbmcgdGhlIG1pZGRsZSBvZiBEZWNlbWJlciwgMjAxNC4gQWxsIGN1cnJlbnQgYW5kIGZ1dHVyZSBFViBjZXJ0aWZpY2F0ZXMsIHB1cmNoYXNlZCBhbmQgYWN0aXZhdGVkIHZpYSBOYW1lY2hlYXAsIHdpbGwgc3VwcG9ydCBDZXJ0aWZpY2F0ZSBUcmFuc3BhcmVuY3ksIGFuZCBwdWJsaWMgbG9ncyB3aWxsIGJlIHdoaXRlbGlzdGVkLiBBcyBwZXIgcmVjZW50IEdvb2dsZSBhbm5vdW5jZW1lbnQsIGFsbCBTU0wgY2VydGlmaWNhdGVzLCBEViBhbmQgT1YgaW5jbHVkZWQsIHdpbGwgYmUgcmVxdWlyZWQgdG8gY29tcGx5IHdpdGggQ1Qgc3RhcnRpbmcgT2N0b2JlciwgMjAxNy48L3A+DQoJCTxzcGFuIHN0eWxlPSJmb250LXNpemU6IDFlbTsgZm9udC1mYW1pbHk6IFZlcmRhbmEsQXJpYWwsSGVsdmV0aWNhLHNhbnMtc2VyaWY7IiBsYW5nPSJFTi1VUyI+DQoJCTwvc3Bhbj4NCgkJPHA+Q2VydGlmaWNhdGUgVHJhbnNwYXJlbmN5IGlzIGEgYmFja2dyb3VuZCBtb2RpZmljYXRpb24gdG8gdGhlIHdheSBFViBjZXJ0aWZpY2F0ZXMgYXJlIGlzc3VlZC4gVGhpcyBwcm9jZXNzIGhhcyA8Yj5ubyBpbXBhY3Q8L2I+IG9uIFNTTCBvcmRlcmluZyBhbmQgYWN0aXZhdGlvbiB2aWEgTmFtZWNoZWFwIGludGVyZmFjZSBhbmQgPGI+bm8gYWN0aW9ucyBhcmUgcmVxdWlyZWQ8L2I+IGZyb20geW91LCBldmVuIGlmIHlvdXIgRVYgY2VydGlmaWNhdGUgaGFzIGJlZW4gaXNzdWVkIGxvbmcgYmVmb3JlIHRoaXMgbm92ZWx0eS4gWW91ciBFViBjZXJ0aWZpY2F0ZXMgaGF2ZSBiZWVuIGFkZGVkIHRvIEdvb2dsZeKAmXMgQ2VydGlmaWNhdGUgVHJhbnNwYXJlbmN5IHdoaXRlbGlzdCBieSBDZXJ0aWZpY2F0ZSBBdXRob3JpdGllcy4gPGJyIC8+PC9wPg0KCQk8cD4NCgkJCQk8Yj5Ob3RlOiA8L2I+U2luY2UgPGI+MjMgTWFyY2ggMjAxODwvYj4sPGI+IGFsbCBTU0wgY2VydGlmaWNhdGVzPC9iPiBpc3N1ZWQgYnkgQ29tb2RvIENBIChub3cgU2VjdGlnbyBDQSkgPGI+Y29tcGx5PC9iPiB3aXRoIENocm9taXVtJ3MgQ1QgUG9saWN5LiBUaHVzLCBubyBhZGRpdGlvbmFsIGFjdGlvbnMgYXJlIHJlcXVpcmVkIGZyb20gdGhlIGVuZCB1c2VyIG9mIENvbW9kbyAobm93IFNlY3RpZ28pIFNTTCBjZXJ0aWZpY2F0ZSB0byBpbmNsdWRlIGNlcnRpZmljYXRlcyBpc3N1ZWQgb24gb3IgYWZ0ZXIgc3VjaCBhIGRhdGUgaW4gYW55IGtub3duIENUIExvZyB0byBiZSBjb21wbGlhbnQgd2l0aCA8YSBocmVmPSJodHRwczovL2dpdGh1Yi5jb20vY2hyb21pdW0vY3QtcG9saWN5IiBsaW5rdGV4dD0iR29vZ2xlIENocm9tZSBtYW5kYXRlIGZyb20gQXByaWwgMjAxIiBsaW5rdHlwZT0iQ3VzdG9tIiB0YXJnZXQ9Il9ibGFuayI+R29vZ2xlIENocm9tZSBtYW5kYXRlIGZyb20gQXByaWwgMjAxODwvYT4uPC9wPg0KCQk8cD4NCgkJCQk8YnIgLz4NCgkJPC9wPg0KCQk8cD4NCgkJCQk8c3Ryb25nPg0KCQkJCQkJPGk+SG93IGNhbiBJIGNoZWNrIGlmIENlcnRpZmljYXRlIFRyYW5zcGFyZW5jeSBpcyBzdXBwb3J0ZWQ/PC9pPg0KCQkJCTwvc3Ryb25nPg0KCQk8L3A+DQoJCTxvbD4NCgkJCQk8bGk+T3BlbiB5b3VyIENocm9tZSBicm93c2VyIGFuZCBjbGljayB0aGUgZWxsaXBzaXMvdGhyZWUgZG90cyBpbiB0aGUgdG9wLXJpZ2h0IGNvcm5lci48L2xpPg0KCQkJCTxsaT5TZWxlY3QgPHN0cm9uZz5Nb3JlIHRvb2xzPC9zdHJvbmc+ICZndDsgPHN0cm9uZz5EZXZlbG9wZXIgdG9vbHM8L3N0cm9uZz4gJmd0OyA8c3Ryb25nPlNlY3VyaXR5PC9zdHJvbmc+Og0KPGJyIC8+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL0NUMS5wbmciIC8+PGJyIC8+PGJyIC8+PC9saT4NCgkJCQk8bGk+Q29ubmVjdCB0byB0aGUgd2Vic2l0ZSB5b3Ugd2FudCB0byBjaGVjayBvciByZWxvYWQgdGhlIHBhZ2UgaWYgaXQncyBhbHJlYWR5IG9wZW4uPC9saT4NCgkJCQk8bGk+Q2xpY2sgdGhlIGxpbmsgdW5kZXIgIjxzdHJvbmc+TWFpbiBvcmlnaW48L3N0cm9uZz4iIGFuZCBzY3JvbGwgZG93biB0byB0aGUgIjxzdHJvbmc+Q2VydGlmaWNhdGUgVHJhbnNwYXJlbmN5PC9zdHJvbmc+IiBzZWN0aW9uOg0KPGJyIC8+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL0NUMi5wbmciIC8+PGJyIC8+PGJyIC8+PC9saT4NCgkJCQk8bGk+SGl0ICI8c3Ryb25nPlNob3cgZnVsbCBkZXRhaWxzPC9zdHJvbmc+IjoNCjxiciAvPjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9DVDMucG5nIiAvPjwvbGk+DQoJCTwvb2w+DQoJCTxwPk5vdyB5b3Ugd2lsbCBzZWUgYWxsIGF2YWlsYWJsZSBTQ1RzIGxvZ3MgZm9yIHRoZSBvcGVuZWQgd2Vic2l0ZS48L3A+DQoJCTxwPg0KCQkJCTxzdHJvbmc+Tm90ZTwvc3Ryb25nPjogVGhlIDxzdHJvbmc+U0NUIGxpc3Q8L3N0cm9uZz4gc2VjdGlvbiBpcyBkaXNwbGF5ZWQgb24gV2luZG93cyAxMCBhbmQgaGlnaGVyLiBPbiBvbGRlciBPcGVyYXRpbmcgU3lzdGVtcywgdGhlIHNlY3Rpb24gaXMgbmFtZWQgPHN0cm9uZz4xLjMuNi4xLjQuMS4xMTEyOS4yLjQuMjwvc3Ryb25nPi48L3A+DQoJCTxwPg0KCQkJCTxiciAvPg0KCQk8L3A+DQoJCTxpPg0KCQk8L2k+DQoJCTxkaXY+QWxzbywgaGVyZSBhcmUgc29tZSB1c2VmdWwgb25saW5lIHRvb2xzIHRvIGNoZWNrIHRoZSBTQ1Q6PGJyIC8+PC9kaXY+DQoJCTxkaXY+DQoJCQkJPHVsPg0KCQkJCQkJPGxpPg0KCQkJCQkJCQk8YSBocmVmPSJodHRwczovL2RlY29kZXIubGluay9jZXJ0aWZpY2F0ZV90cmFuc3BhcmVuY3kiIGxpbmt0ZXh0PSJvbmxpbmUgY2hlY2tlciIgbGlua3R5cGU9IkN1c3RvbSIgdGFyZ2V0PSJfYmxhbmsiPk5hbWVjaGVhcCBvbmxpbmUgY2hlY2tlcjwvYT4gd2hlcmUgdGhlIGNlcnRpZmljYXRlIGNvZGUgc2hvdWxkIGJlIHBhc3RlZDs8L2xpPg0KCQkJCQkJPGxpPg0KCQkJCQkJCQk8YSBocmVmPSJodHRwczovL2NydC5zaC8iIGxpbmt0ZXh0PSJTZWN0aWdvIGNoZWNrZXIiIGxpbmt0eXBlPSJDdXN0b20iIHRhcmdldD0iX2JsYW5rIj5TZWN0aWdvIGNoZWNrZXI8L2E+IHdoZXJlIHlvdSBqdXN0IG5lZWQgdG8gdHlwZSBjb21tb24gbmFtZSBvZiB0aGUgU2VjdGlnbyBjZXJ0aWZpY2F0ZSBpbiBxdWVzdGlvbjs8L2xpPg0KCQkJCQkJPGxpPg0KCQkJCQkJCQk8YSBocmVmPSJodHRwczovL3RyYW5zcGFyZW5jeXJlcG9ydC5nb29nbGUuY29tL2h0dHBzL2NlcnRpZmljYXRlcyIgbGlua3RleHQ9Ikdvb2dsZSBTQ1QgY2hlY2tlciIgbGlua3R5cGU9IkN1c3RvbSIgdGFyZ2V0PSJfYmxhbmsiPkdvb2dsZSBTQ1QgY2hlY2tlcjwvYT4uPGJyIC8+PC9saT4NCgkJCQk8L3VsPg0KCQk8L2Rpdj4NCgkJPHA+DQoJCQkJPGk+DQoJCQkJCQk8Yj4NCgkJCQkJCQkJPGJyIC8+QXMgYSBjb25jbHVzaW9u4oCmPC9iPg0KCQkJCTwvaT4NCgkJPC9wPg0KCQk8cD4NCkF0IHRoZSBuZWFyIGZ1dHVyZSwgYWxsIENlcnRpZmljYXRlIEF1dGhvcml0aWVzIHdpbGwgbmVlZCB0byBjb21wbHkgd2l0aCBDVCANCmJ5IGF1dG9tYXRpY2FsbHkgcHVibGlzaGluZyB0aGUgaXNzdWVkIGNlcnRpZmljYXRlcy4gVGhpcyBpcywgaW4gcGFydCwgDQpkdWUgdG8gR29vZ2xl4oCZcyBzdHJvbmcgcG9zaXRpb25pbmcgd2l0aCB0aGVpciBDaHJvbWUgYnJvd3NlcjogZnV0dXJlIHZlcnNpb25zIG9mIHRoZSBDaHJvbWUgYnJvd3NlciBtYXkgZXZlbiBzaG93IHdhcm5pbmcgaW5kaWNhdG9ycyBmb3Igc2l0ZXMgd2l0aCBjZXJ0aWZpY2F0ZXMgdGhhdCBhcmUgbm90IHByZXNlbnQgaW4gQ1QgTG9nIFNlcnZlcnMuIFNvIGZhciwgDQphbnkgRVYgY2VydGlmaWNhdGUgaXMgY2hlY2tlZCBjYXJlZnVsbHkgZm9yIENUIHByZXNlbmNlIGluIHB1YmxpYyBDVCANCkxvZ3MuPC9wPg0KCQk8cD4NCk9mIGNvdXJzZSwgdGhpcyBhcnRpY2xlIGdpdmVzIHlvdSBhIHZlcnkgZ2VuZXJhbCBpZGVhIG9mIHdoYXQgaXMgZ29pbmcgb24gYW5kIHdoYXQgQ2VydGlmaWNhdGUgVHJhbnNwYXJlbmN5IGlzLiBUaGVyZSBhcmUgbXVjaCBtb3JlIHF1ZXN0aW9ucyB0byBiZSBhc2tlZCwgYW5kIHNvbWUgb2YgdGhlbSB3ZXJlIGFscmVhZHkgYW5zd2VyZWQgPGEgaHJlZj0iaHR0cHM6Ly93d3cuY2VydGlmaWNhdGUtdHJhbnNwYXJlbmN5Lm9yZy9mYXEiIGxpbmt0ZXh0PSJoZXJlIiBsaW5rdHlwZT0iQ3VzdG9tIiB0YXJnZXQ9Il9ibGFuayI+aGVyZTwvYT4uIEFzIHVzdWFsLCB3ZSBhcmUgMjQvNyB3aXRoIHlvdSB2aWEgPGEgaHJlZj0iaHR0cHM6Ly93d3cubmFtZWNoZWFwLmNvbS9zdXBwb3J0L2xpdmUtY2hhdC9zc2wuYXNweCIgdGFyZ2V0PSJfYmxhbmsiPkNoYXQ8L2E+IGFuZCA8YSBocmVmPSJodHRwczovL3N1cHBvcnQubmFtZWNoZWFwLmNvbS9pbmRleC5waHA/L1RpY2tldHMvU3VibWl0IiB0YXJnZXQ9Il9ibGFuayI+ZW1haWw8L2E+IChQcm9kdWN0IC0gPGk+U1NMPC9pPikgZm9yIGRpc2N1c3Npb24sIGNsYXJpZmljYXRpb24gYW5kIG5lZ290aWF0aW9uIG9mIHdoYXQgaXMgYmVzdCBmb3IgeW91ITwvcD4NCg==","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"2025-02-06T13:49:12.0000000","LiveDateTime":"1754-02-02T00:00:00.0000000","CreatedDateTime":"2015-07-30T18:36:02.0000000","ApprovalDatetime":"2015-07-30T18:37:00.0000000","RequestCount":35456,"MarkedAsNew":false,"MarkedAsFeatured":false,"RatingValue":2,"CategoryPaths":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":1,"CategoryId":14,"CategoryName":"SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":2,"CategoryId":38,"CategoryName":"SSL General"}],"AssociatedCategories":[{"CategoryId":38,"CategoryName":"SSL General","CategoryDisplayName":"SSL CertificatesSSL General"}],"AssociatedTags":[],"RelatedArticles":[],"AssociatedMedias":[],"PreferredCategoryId":0,"RootParentCategoryName":"","RootParentCategoryId":0},"status":200,"statusText":"OK"},"/api/v1/ncpl/simplekb/getcategorybycategoryid:\"{\\\"categoryId\\\":38}\"":{"body":{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryDto","Description":"QmFzaWMgaW5mb3JtYXRpb24gb24gU1NMIGNlcnRpZmljYXRlcw==","ParentCategoryId":14,"Parent_Category_Name":"SSL Certificates","FriendlyId":null,"ApprovedYN":true,"TreatAsTopicYN":false,"CreatedDateTime":"07/25/2008 16:58:37","CurrentCategoryPaths":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":1,"CategoryId":14,"CategoryName":"SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":2,"CategoryId":38,"CategoryName":"SSL General"}],"RelatedCategories":[],"AssociatedArticles":[{"ArticleId":9503,"Title":"What is an ECC (Elliptic Curve Cryptography) certificate?","ArticleName":"What is an ECC (Elliptic Curve Cryptography) certificate?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/23/2019"},{"ArticleId":9504,"Title":"How do I get an ECC certificate via Namecheap?","ArticleName":"How do I get an ECC certificate via Namecheap?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/06/2025"},{"ArticleId":9507,"Title":"Why an EV certificate is better for an ecommerce website than a Domain Validation one?","ArticleName":"Why an EV certificate is better for an ecommerce website than a Domain Validation one?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"07/24/2020"},{"ArticleId":9508,"Title":"What is the difference between very high, high, medium and low assurance certificates?","ArticleName":"What is the difference between very high, high, medium and low assurance certificates?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/15/2024"},{"ArticleId":9509,"Title":"Your site shows 256-bit encryption and my site shows 128-bit, why?","ArticleName":"Your site shows 256-bit encryption and my site shows 128-bit, why?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"08/27/2019"},{"ArticleId":9511,"Title":"How 2–5-year SSL certificates work","ArticleName":"How 2–5-year SSL certificates work","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":"03/14/2015 04:00:00","FeaturedTillDate":"03/09/2015 04:00:00","ModifiedDateTime":"04/15/2024"},{"ArticleId":9588,"Title":"What is Certificate Transparency?","ArticleName":"What is Certificate Transparency?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/06/2025"},{"ArticleId":9595,"Title":"HTTP to HTTPS redirection on IIS","ArticleName":"HTTP to HTTPS redirection on IIS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/25/2019"},{"ArticleId":9596,"Title":"HTTP Strict Transport Security (HSTS)","ArticleName":"HTTP Strict Transport Security (HSTS)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9597,"Title":"HTTP Public Key Pinning (HPKP)","ArticleName":"HTTP Public Key Pinning (HPKP)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/06/2024"},{"ArticleId":9598,"Title":"Disabling SSLv3","ArticleName":"Disabling SSLv3","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9599,"Title":"Disabling RC4","ArticleName":"Disabling RC4","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9600,"Title":"Disabling SHA-1","ArticleName":"Disabling SHA-1","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9601,"Title":"Cipher Suites Configuration and forcing Perfect Forward Secrecy on Windows","ArticleName":"Cipher Suites Configuration and forcing Perfect Forward Secrecy on Windows","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":9602,"Title":"OCSP Stapling","ArticleName":"OCSP Stapling","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9650,"Title":"I can see SHA-1 fingerprint/thumbprint on my certificate. Is my certificate actually SHA-2?","ArticleName":"I can see SHA-1 fingerprint/thumbprint on my certificate. Is my certificate actually SHA-2?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/23/2019"},{"ArticleId":9652,"Title":"Perfect Forward Secrecy. What it is?","ArticleName":"Perfect Forward Secrecy. What it is?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2022"},{"ArticleId":9653,"Title":"How to check whether the server supports Forward Secrecy","ArticleName":"How to check whether the server supports Forward Secrecy","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"06/22/2023"},{"ArticleId":9682,"Title":"How to push SSL certificates from one Namecheap account to another one","ArticleName":"How to push SSL certificates from one Namecheap account to another one","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/06/2025"},{"ArticleId":9707,"Title":"HSTS: General information","ArticleName":"HSTS: General information","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9708,"Title":"Prerequisites for Namecheap Shared hosting to enable HSTS","ArticleName":"Prerequisites for Namecheap Shared hosting to enable HSTS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9709,"Title":"How to enable HSTS on Namecheap shared hosts","ArticleName":"How to enable HSTS on Namecheap shared hosts","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/10/2023"},{"ArticleId":9710,"Title":"How to enable HSTS on third-party servers","ArticleName":"How to enable HSTS on third-party servers","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9711,"Title":"How to check if HSTS is enabled","ArticleName":"How to check if HSTS is enabled","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9727,"Title":"What is SSL certificate encryption strength?","ArticleName":"What is SSL certificate encryption strength?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9752,"Title":"How do I get A+ rating in SSLLabs?","ArticleName":"How do I get A+ rating in SSLLabs?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9770,"Title":"How to use .htaccess to redirect to https in cPanel","ArticleName":"How to use .htaccess to redirect to https in cPanel","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/10/2023"},{"ArticleId":9782,"Title":"Security tips for business","ArticleName":"Security tips for business","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/12/2021"},{"ArticleId":9783,"Title":"1024 bit certificates","ArticleName":"1024 bit certificates","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/13/2022"},{"ArticleId":9800,"Title":"Advantages of having an SSL certificate","ArticleName":"Advantages of having an SSL certificate","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2023"},{"ArticleId":9805,"Title":"Setting HTTPS redirect on a Nginx web-server","ArticleName":"Setting HTTPS redirect on a Nginx web-server","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9821,"Title":"Apache Redirect to HTTPS","ArticleName":"Apache Redirect to HTTPS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"06/19/2020"},{"ArticleId":9952,"Title":"Supported key sizes and signature algorithms in CSRs","ArticleName":"Supported key sizes and signature algorithms in CSRs","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"12/05/2017 05:00:00","ModifiedDateTime":"07/27/2023"},{"ArticleId":9953,"Title":"IIS Redirect HTTP to HTTPS","ArticleName":"IIS Redirect HTTP to HTTPS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"11/28/2017 05:00:00","ModifiedDateTime":"12/06/2022"},{"ArticleId":9968,"Title":"How to check the certificate revocation status","ArticleName":"How to check the certificate revocation status","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"01/26/2018 05:00:00","ModifiedDateTime":"09/24/2019"},{"ArticleId":9969,"Title":"HPKP pinning","ArticleName":"HPKP pinning","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/06/2024"},{"ArticleId":9991,"Title":"CAA Record and why it is needed (SSL related)","ArticleName":"CAA Record and why it is needed (SSL related)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"04/30/2018 04:00:00","ModifiedDateTime":"09/07/2022"},{"ArticleId":10081,"Title":"Comodo CA rebrands as Sectigo","ArticleName":"Comodo CA rebrands as Sectigo","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"01/25/2019"},{"ArticleId":10100,"Title":"Cipher Suites Configuration for Apache, Nginx","ArticleName":"Cipher Suites Configuration for Apache, Nginx","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2022"},{"ArticleId":10503,"Title":"How to remove an SSL from a Namecheap account","ArticleName":"How to remove an SSL from a Namecheap account","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/11/2025"},{"ArticleId":10504,"Title":"What is AutoSSL and how to use it?","ArticleName":"What is AutoSSL and how to use it?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/18/2025"},{"ArticleId":10557,"Title":"Decoder.link user guide","ArticleName":"Decoder.link user guide","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/15/2025"},{"ArticleId":10595,"Title":"Understanding How SSL Encryption Works","ArticleName":"Understanding How SSL Encryption Works","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"04/05/2023"},{"ArticleId":10597,"Title":"What is SSL and TLS","ArticleName":"What is SSL and TLS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2023"},{"ArticleId":10747,"Title":"What is MPIC (Multi-Perspective Issuance Corroboration)","ArticleName":"What is MPIC (Multi-Perspective Issuance Corroboration)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/15/2025"},{"ArticleId":9293,"Title":"I need to secure some of the subdomains of my domain name","ArticleName":"I need to secure some of the subdomains of my domain name","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9294,"Title":"I need to secure two, three or more domain names with the same certificate","ArticleName":"I need to secure two, three or more domain names with the same certificate","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":9464,"Title":"Can I download an issued certificate on your site?","ArticleName":"Can I download an issued certificate on your site?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/12/2024"},{"ArticleId":786,"Title":"What is an SSL certificate and what is it used for?","ArticleName":"What is an SSL certificate and what is it used for?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"07/24/2023"},{"ArticleId":334,"Title":"What is Certificate Authority (CA)?","ArticleName":"What is Certificate Authority (CA)?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9415,"Title":"SSL certificate migration from the SHA-1 to SHA-2 algorithm","ArticleName":"SSL certificate migration from the SHA-1 to SHA-2 algorithm","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9467,"Title":"How do I check my hashing algorithm?","ArticleName":"How do I check my hashing algorithm?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9484,"Title":"I want to test your service do you have trial certificates?","ArticleName":"I want to test your service do you have trial certificates?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"04/28/2025"},{"ArticleId":789,"Title":"Can I use a single SSL certificate for multiple subdomains?","ArticleName":"Can I use a single SSL certificate for multiple subdomains?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":787,"Title":"How to inform your clients that you use SSL","ArticleName":"How to inform your clients that you use SSL","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2023"},{"ArticleId":464,"Title":"What is a wildcard certificate?","ArticleName":"What is a wildcard certificate?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/07/2024"},{"ArticleId":790,"Title":"Types of certificates offered at Namecheap","ArticleName":"Types of certificates offered at Namecheap","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/01/2019"},{"ArticleId":9469,"Title":"Are your certificates private or shared? What is the difference?","ArticleName":"Are your certificates private or shared? What is the difference?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/26/2015"},{"ArticleId":9466,"Title":"Can I get a certificate if I use an online web-hosting (Wix, Weebly, Tumblr, etc.)?","ArticleName":"Can I get a certificate if I use an online web-hosting (Wix, Weebly, Tumblr, etc.)?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"01/20/2021"},{"ArticleId":9473,"Title":"Can I use your SSL certificates for FTP and SQL?","ArticleName":"Can I use your SSL certificates for FTP and SQL?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/22/2018"},{"ArticleId":9481,"Title":"I have a certificate at another vendor; will there be an issue, if I activate one with you for the same common name?","ArticleName":"I have a certificate at another vendor; will there be an issue, if I activate one with you for the same common name?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/26/2015"},{"ArticleId":982,"Title":"Domain Validated certificates","ArticleName":"Domain Validated certificates","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":886,"Title":"Chained and single Root certificates","ArticleName":"Chained and single Root certificates","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":885,"Title":"SSL certificate warranty","ArticleName":"SSL certificate warranty","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"}],"AssociatedTags":[],"CategoryId":38,"CategoryName":"SSL General"},"status":200,"statusText":"OK"},"/api/v1/ncpl/simplekb/getcategories:\"{\\\"parentCategoryId\\\":0,\\\"getTree\\\":true}\"":{"body":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2216,"CategoryName":"Spam Protection"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2217,"CategoryName":"Renewal"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2218,"CategoryName":"cPanel SSL Plugin"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2219,"CategoryName":"PHP Configuration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2221,"CategoryName":"Multi-Domain SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2222,"CategoryName":"Cancellation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2223,"CategoryName":"Browser errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2224,"CategoryName":"Site Seal, Logo"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2225,"CategoryName":"SEO"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2226,"CategoryName":"Email Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2227,"CategoryName":"SSL Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/cloud-red.png","ShortDesc":"","CategoryId":2228,"CategoryName":"Apps","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2251,"CategoryName":"Supersonic CDN"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2298,"CategoryName":"Site Maker"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":177,"CategoryName":"Google Workspace (formerly G Suite)"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2229,"CategoryName":"Hosting Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2232,"CategoryName":"DNSSEC"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2234,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2237,"CategoryName":"Host records setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2238,"CategoryName":"SSL installation errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/easywp-red.png","ShortDesc":"","CategoryId":2239,"CategoryName":"EasyWP","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2280,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2279,"CategoryName":"General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2281,"CategoryName":"WordPress Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2282,"CategoryName":"Plugins and Themes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2284,"CategoryName":"WordPress Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2285,"CategoryName":"SFTP and Database access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2286,"CategoryName":"Domains questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2288,"CategoryName":"Billing questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2287,"CategoryName":"SSL questions"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2251,"CategoryName":"Supersonic CDN"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2252,"CategoryName":"InterWorx questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2254,"CategoryName":"Domains How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2255,"CategoryName":"Hosting How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2257,"CategoryName":"Sales & Payments How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2258,"CategoryName":"cPanel Email How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2260,"CategoryName":"Private Email Contacts and Calendars Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2262,"CategoryName":"EasyWP How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"https://download.namecheap.com/assets/img/domainvault-red@2x.png","ShortDesc":"","CategoryId":2289,"CategoryName":"Domain Vault","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2290,"CategoryName":"CSR code"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2291,"CategoryName":"Webuzo questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2292,"CategoryName":"Browser Extensions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2293,"CategoryName":"Automated SSL management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2298,"CategoryName":"Site Maker"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":27,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/support-red.png","ShortDesc":"","CategoryId":5,"CategoryName":"General & Support","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":7,"CategoryName":"Billing FAQ"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":8,"CategoryName":"Transfer Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":22,"CategoryName":"Hosting Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":38,"CategoryName":"SSL General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":45,"CategoryName":"Account Security"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":46,"CategoryName":"Domain Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":63,"CategoryName":"Namecheap API"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":177,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2179,"CategoryName":"Private Email: General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2274,"CategoryName":"General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2280,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2279,"CategoryName":"General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2215,"CategoryName":"Private Email: Mailbox Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2196,"CategoryName":"WHMCS module for SSL"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/savings-red.png","ShortDesc":"","CategoryId":2200,"CategoryName":"Checkout & Billing","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":7,"CategoryName":"Billing FAQ"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2201,"CategoryName":"Domains Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":21,"CategoryName":"Hosting Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":71,"CategoryName":"SSL Certificates Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2177,"CategoryName":"Private Email"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2201,"CategoryName":"Domains Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":67,"CategoryName":"Activation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":83,"CategoryName":"Transfer to Namecheap"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":43,"CategoryName":"Profile Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":10,"CategoryName":"DNS Questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":29,"CategoryName":"cPanel questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":21,"CategoryName":"Hosting Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":11,"CategoryName":"Dynamic DNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":44,"CategoryName":"Account Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":84,"CategoryName":"Transfer to another provider"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":68,"CategoryName":"Validation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2182,"CategoryName":"cPanel: Software Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2214,"CategoryName":"Email Forwarding"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2270,"CategoryName":"Routers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2281,"CategoryName":"WordPress Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2282,"CategoryName":"Plugins and Themes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2272,"CategoryName":"TV"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2187,"CategoryName":"cPanel: WordPress"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":219,"CategoryName":"Canceled Transfers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":71,"CategoryName":"SSL Certificates Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2176,"CategoryName":"Private Email: DNS Settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":69,"CategoryName":"Installation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/reseller-red.png","ShortDesc":"","CategoryId":34,"CategoryName":"Domains","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2232,"CategoryName":"DNSSEC"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2234,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2237,"CategoryName":"Host records setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":46,"CategoryName":"Domain Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":10,"CategoryName":"DNS Questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":11,"CategoryName":"Dynamic DNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":35,"CategoryName":"Registrations"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2207,"CategoryName":"Renewal questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":36,"CategoryName":"Domains with extended attributes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":51,"CategoryName":"FreeDNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":15,"CategoryName":"Namecheap Market"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2208,"CategoryName":"3rd Party Services Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2278,"CategoryName":"Handshake TLDs"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":35,"CategoryName":"Registrations"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":70,"CategoryName":"Reissuance"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/protection-red.png","ShortDesc":"","CategoryId":37,"CategoryName":"Domain Privacy Protection","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2177,"CategoryName":"Private Email"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2178,"CategoryName":"Private Email: Webmail Features"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2207,"CategoryName":"Renewal questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2210,"CategoryName":"cPanel Add-ons"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2273,"CategoryName":"Gaming Consoles"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2284,"CategoryName":"WordPress Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2285,"CategoryName":"SFTP and Database access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2268,"CategoryName":"macOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2175,"CategoryName":"Private Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/status-red.png","ShortDesc":"","CategoryId":2209,"CategoryName":"Domain Transfers","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":8,"CategoryName":"Transfer Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":83,"CategoryName":"Transfer to Namecheap"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":84,"CategoryName":"Transfer to another provider"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":219,"CategoryName":"Canceled Transfers"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":48,"CategoryName":"VPS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":36,"CategoryName":"Domains with extended attributes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/server-red.png","ShortDesc":"","CategoryId":12,"CategoryName":"Hosting","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2219,"CategoryName":"PHP Configuration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2225,"CategoryName":"SEO"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2252,"CategoryName":"InterWorx questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2291,"CategoryName":"Webuzo questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":27,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":22,"CategoryName":"Hosting Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":29,"CategoryName":"cPanel questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2182,"CategoryName":"cPanel: Software Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2187,"CategoryName":"cPanel: WordPress"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2210,"CategoryName":"cPanel Add-ons"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":48,"CategoryName":"VPS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2188,"CategoryName":"Dedicated Server"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":30,"CategoryName":"WHM questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":32,"CategoryName":"DNS settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":103,"CategoryName":"LVE (CloudLinux)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":89,"CategoryName":"SSH Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":205,"CategoryName":"FTP questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2180,"CategoryName":"MySQL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2199,"CategoryName":"Hosting Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2194,"CategoryName":"Tips & Tricks"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":239,"CategoryName":"WHMCS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":33,"CategoryName":"SSL Installation"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2171,"CategoryName":"Private Email: Active Sync (Exchange) Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2188,"CategoryName":"Dedicated Server"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2269,"CategoryName":"iOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2286,"CategoryName":"Domains questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2288,"CategoryName":"Billing questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2271,"CategoryName":"Linux"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":30,"CategoryName":"WHM questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":31,"CategoryName":"cPanel Email FAQs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":51,"CategoryName":"FreeDNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/email-red.png","ShortDesc":"","CategoryId":93,"CategoryName":"Email service","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2216,"CategoryName":"Spam Protection"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2226,"CategoryName":"Email Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2260,"CategoryName":"Private Email Contacts and Calendars Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2179,"CategoryName":"Private Email: General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2215,"CategoryName":"Private Email: Mailbox Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2214,"CategoryName":"Email Forwarding"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2176,"CategoryName":"Private Email: DNS Settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2178,"CategoryName":"Private Email: Webmail Features"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2175,"CategoryName":"Private Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2171,"CategoryName":"Private Email: Active Sync (Exchange) Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":31,"CategoryName":"cPanel Email FAQs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2186,"CategoryName":"cPanel Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2204,"CategoryName":"Private Email: Video Overview"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":32,"CategoryName":"DNS settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":15,"CategoryName":"Namecheap Market"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2186,"CategoryName":"cPanel Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2266,"CategoryName":"Windows"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2287,"CategoryName":"SSL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2267,"CategoryName":"Android"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2208,"CategoryName":"3rd Party Services Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2204,"CategoryName":"Private Email: Video Overview"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/security-red.png","ShortDesc":"","CategoryId":14,"CategoryName":"SSL Certificates","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2217,"CategoryName":"Renewal"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2218,"CategoryName":"cPanel SSL Plugin"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2221,"CategoryName":"Multi-Domain SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2222,"CategoryName":"Cancellation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2223,"CategoryName":"Browser errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2224,"CategoryName":"Site Seal, Logo"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2238,"CategoryName":"SSL installation errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2290,"CategoryName":"CSR code"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2293,"CategoryName":"Automated SSL management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":38,"CategoryName":"SSL General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":67,"CategoryName":"Activation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":68,"CategoryName":"Validation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":69,"CategoryName":"Installation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":70,"CategoryName":"Reissuance"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/performance-red.png","ShortDesc":"","CategoryId":9,"CategoryName":"My Account","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":45,"CategoryName":"Account Security"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":43,"CategoryName":"Profile Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":44,"CategoryName":"Account Access"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2278,"CategoryName":"Handshake TLDs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":103,"CategoryName":"LVE (CloudLinux)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/affiliates-red.png","ShortDesc":"","CategoryId":55,"CategoryName":"Affiliates","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":89,"CategoryName":"SSH Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/tools-red.png","ShortDesc":"","CategoryId":2211,"CategoryName":"API & Resellers","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2227,"CategoryName":"SSL Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2229,"CategoryName":"Hosting Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":63,"CategoryName":"Namecheap API"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2196,"CategoryName":"WHMCS module for SSL"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/timer-red.png","ShortDesc":"","CategoryId":2212,"CategoryName":"Legacy Products","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":205,"CategoryName":"FTP questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2180,"CategoryName":"MySQL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2199,"CategoryName":"Hosting Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/premiumdns-red.png","ShortDesc":"","CategoryId":2231,"CategoryName":"PremiumDNS","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2194,"CategoryName":"Tips & Tricks"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"https://static.nc-img.com/live-resource/icons/knowledgebase/fastVPN_icon-150px.png","ShortDesc":"","CategoryId":2265,"CategoryName":"FastVPN","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2292,"CategoryName":"Browser Extensions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2274,"CategoryName":"General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2270,"CategoryName":"Routers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2272,"CategoryName":"TV"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2273,"CategoryName":"Gaming Consoles"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2268,"CategoryName":"macOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2269,"CategoryName":"iOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2271,"CategoryName":"Linux"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2266,"CategoryName":"Windows"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2267,"CategoryName":"Android"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":239,"CategoryName":"WHMCS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":33,"CategoryName":"SSL Installation"}],"status":200,"statusText":"OK"}}Some of us may have already heard the new word combination which had spread over the Internet society - Certificate Transparency. This process and, which is more important, the novelty of this concept itself have been recently announced by Google Inc. So, what certificate transparency actually is? Let us have a look.
As originally defined and planned by Netscape and others in the mid-1990s, certificate issuance process implies that a Certificate Authority (CA) should generate and present the certificate for the certificate requester (domain owner, server administrator) for review and approval, prior to the actual SSL’s issuance. Once issued, the Certificate Authority publishes the certificate in an independent repository which will prove that the requester has been aware of the certificate’s issuance. That independent repository allows public key (which is an essential part of SSL certificate) verification and validity check prior to establishing and negotiating a secure session with the server. In a way, a public key can be alternatively validated besides for getting it from the server solely during session negotiation. Certificate Transparency project brings up a new way of making certificate’s issuance process publicly available, open and, no matter how tautological it sounds, transparent.
How is the certificate transparency achieved?
Certificate transparency (further CT) is achieved by having Certificate Authorities post certificates to publicly accessible Qualified CT logs. There are four main participants in the CT:
Firstly, a Certificate Authority creates so called pre-certificate which contains main information that will be reflected in the future certificate and sends it to the trusted Log server.
In its turn, Log server accepts this information and replies with a ‘signed certificate timestamp (SCT)’ which is, by nature, a ‘promise’ to add the certificate to the log within a certain period of time. This time frame, known as Maximum Merge Delay (MMD), sets the reasonable period when the certificate is added to the Log server. One might question oneself if the MMD value can actually delay or postpone the certificate’s issuance. MMD has influence neither on SSL’s issuance nor on certificate’s usage. The largest MMD timeframe is 24 hrs, meaning that all newly issued certificates will be available in log maximum within 24 hrs once SCT is generated.
SCT goes ‘hand in hand’ with the SSL certificate throughout its life cycle, until the expiration or revocation.
SCT is accepted by the Certificate Authority and integrated either in the body of the certificate or presented by other means. SCT presence and availability in SSL Certificate itself serves as a signal that the certificate has been published for review. There are three general methods for CT to deliver SCT with the certificates: x509v3 extension (which actually requires no additional actions from server operator), TLS extension (which is to be used by site operator with type signed_certificate_timestamp for SCT delivering to the client during TLS Handshake) and OCSP Stapling.
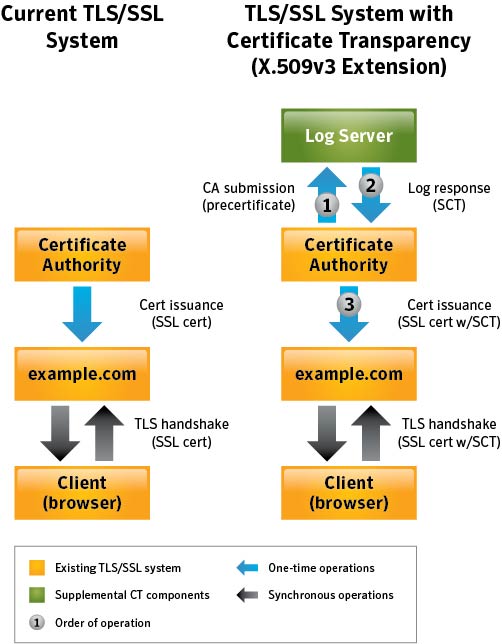
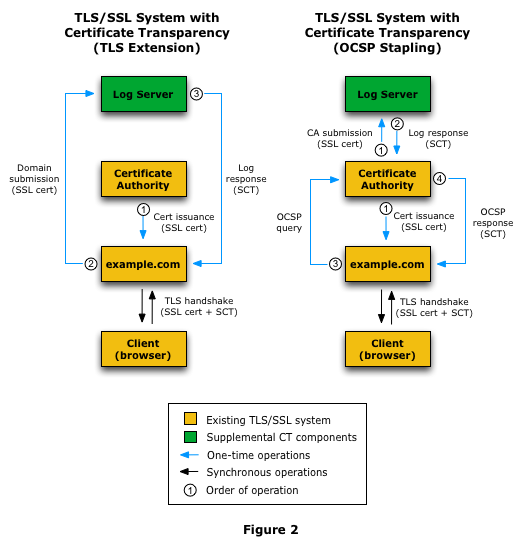
More details on these methods can be seen here, but the main idea is that Signed Certificate Timestamp is presented along with the certificate itself during session negotiation.
Pros and ….Pros!
The main and the very first advantage which comes to our mind is trust. Having company details published and open for viewing builds a way better image while doing online business. This point is beneficial not only for CAs, domain owners and server operators, but also for a great number of end users. Google is currently running a Certificate Transparency log which is filled in with the certificates retrieved from the web, and active work is performed on monitoring and auditing software which can be reviewed here. The development of a new Google Chrome version is currently going on. At some point, it will be updated to show a warning message prior to establishing a connection to a website without a verified SCT. After adoption of certificate transparency by Certificate Authorities and browsers increases, Chrome is planned to be modified again, so that no connection to a web site without a valid SCT along with the certificate is performed (but this setting can be changed by a Chrome user).
Another advantage concerns Certificate Authorities’ business model: SSL certificates are issued just the way they were, except for one extra step: first, the certificate is sent to several Log servers to receive and include a timestamp to the SSL. Domain owners or server administrators will not need to adjust to new SSL-performance procedure. TLS Handshake remains unchanged, but the domain/server owner is able to monitor the certificates and be sure that no unrequested or unapproved certificates are issued for his/her domain or server.
I am for transparency! But how does this affect my EV certificate with Namecheap Inc.?
All Extended Validation (EV) certificates with an expiration date beyond December 2015 should support certificate transparency. This concerns already issued EV certificates as well. It is planned on or after February 1st, 2015 to stop displaying the Green Bar in Google Chrome, if a valid and verified SCT is not provided along with an EV certificate during secure session negotiation. The exact time frame has not been announced so far, and it depends on Google Chrome release schedule.
Comodo (now Sectigo) Certificate Authority - our SSL vendor - supports Certificate Transparency for EV certificates starting the middle of December, 2014. All current and future EV certificates, purchased and activated via Namecheap, will support Certificate Transparency, and public logs will be whitelisted. As per recent Google announcement, all SSL certificates, DV and OV included, will be required to comply with CT starting October, 2017.
Certificate Transparency is a background modification to the way EV certificates are issued. This process has no impact on SSL ordering and activation via Namecheap interface and no actions are required from you, even if your EV certificate has been issued long before this novelty. Your EV certificates have been added to Google’s Certificate Transparency whitelist by Certificate Authorities.
Note: Since 23 March 2018, all SSL certificates issued by Comodo CA (now Sectigo CA) comply with Chromium's CT Policy. Thus, no additional actions are required from the end user of Comodo (now Sectigo) SSL certificate to include certificates issued on or after such a date in any known CT Log to be compliant with Google Chrome mandate from April 2018.
How can I check if Certificate Transparency is supported?
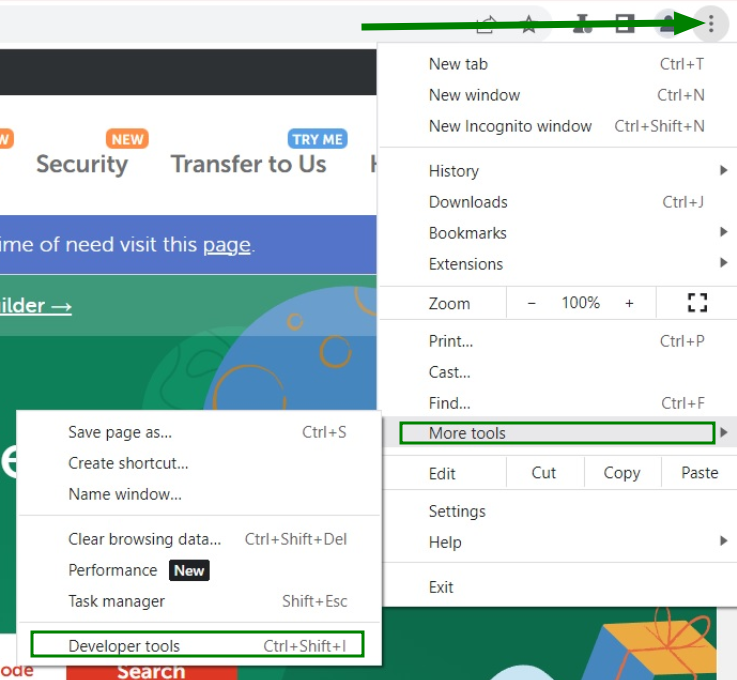
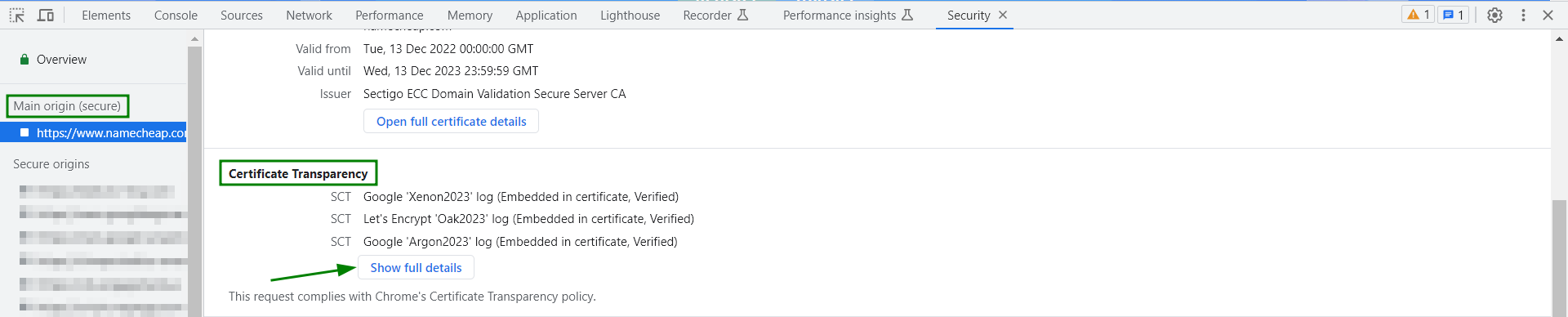
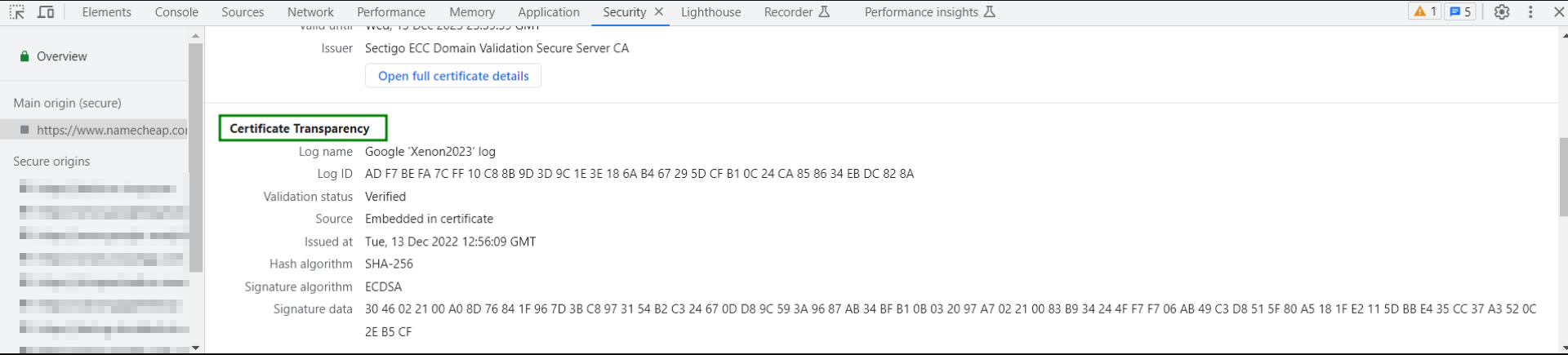
Now you will see all available SCTs logs for the opened website.
Note: The SCT list section is displayed on Windows 10 and higher. On older Operating Systems, the section is named 1.3.6.1.4.1.11129.2.4.2.
As a conclusion…
At the near future, all Certificate Authorities will need to comply with CT by automatically publishing the issued certificates. This is, in part, due to Google’s strong positioning with their Chrome browser: future versions of the Chrome browser may even show warning indicators for sites with certificates that are not present in CT Log Servers. So far, any EV certificate is checked carefully for CT presence in public CT Logs.
Of course, this article gives you a very general idea of what is going on and what Certificate Transparency is. There are much more questions to be asked, and some of them were already answered here. As usual, we are 24/7 with you via Chat and email (Product - SSL) for discussion, clarification and negotiation of what is best for you!
Need help? We're always here for you.