| Subtotal | $0.00 |
| Subtotal | $0.00 |
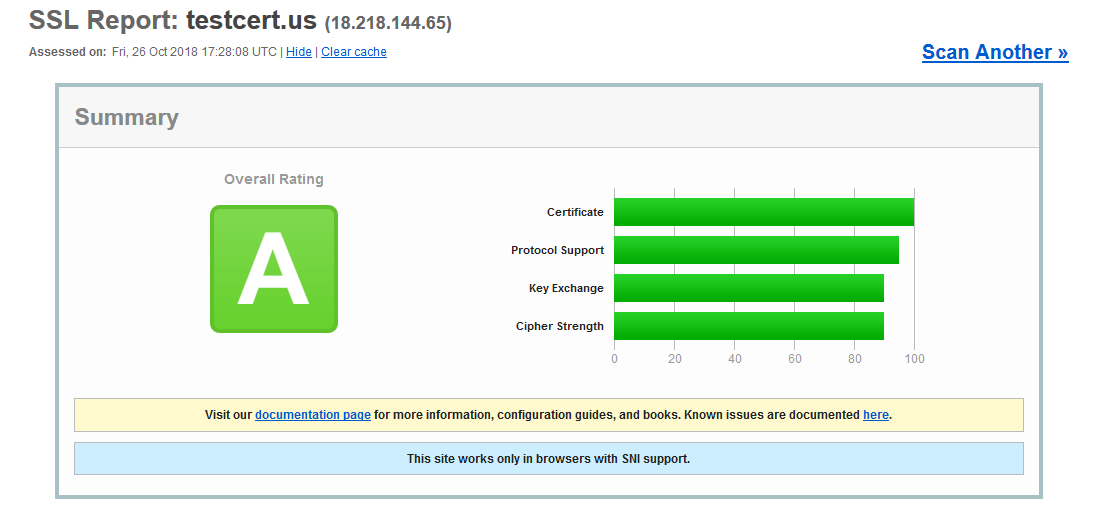
Once you install your SSL certificate on Apache, you can test its installation status by using Qualys SSL Labs and receive the A grade.
In order to avoid such vulnerabilities, you can write a specific rule in the configuration file that will only allow modern TLSv1.1+ versions to be established. These rules are called "Cipher Suites". They are needed to help secure network connections that use SSL during the handshake. To receive the A+ grade on SSL Labs, there are a few necessary Cipher Suites to add to the configuration file. More details regarding Cipher Suites are provided in this article.
Please note: Some older browsers that don’t support the latest TLS versions cannot access websites with up-to-date protocols enabled.
Apache
Keep in mind that the configuration file for your website are:
For Debian and Ubuntu Operating Systems, the file can be found in:
/etc/apache2/sites-available/
For CentOS, Fedora, and Red Hat Enterprise Linux (RHEL), the configuration file can be found running the following command:
httpd -S"
Now, open the configuration file with the text editor of your choice.
Here is the link where you can receive the necessary configuration file for your system. Now you will need to choose your web server type, its version, and the OpenSSL certificate version.
If you are unsure which version you have, you can run the following command to locate the web server version: httpd -v
To check the OpenSSL version, use this command: openssl version
You will then see the example of the configuration file for the chosen version that includes the virtual host for 443 port with the HSTS header in it. The tool gives the OCSP values as well.
Please make sure to only copy the necessary values to your configuration file and keep in mind the Cipher Suite location.
The HSTS header needs to be placed inside the Virtual Host for 443 port.
However, the Cipher Suites and OCSP responder need to be located outside the Virtual Host. See below:
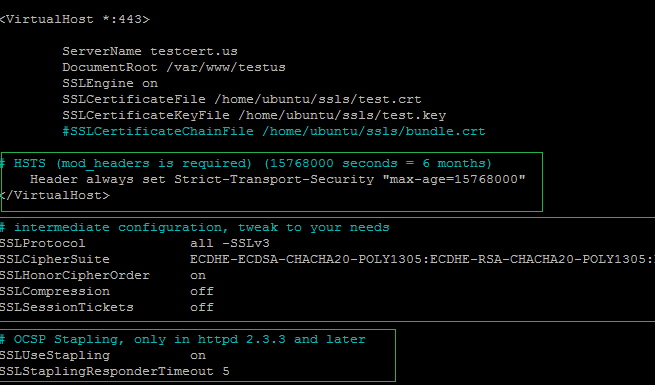
When the VirtualHost is modified, save the file, and run the syntax check: apachectl -t
If the system shows "Syntax OK", reload the Apache for the changes to take effect with the following command: sudo service apache2 reload
You can check the applied configuration file using this online analyzer.
Nginx
In order to add the Cipher Suites to the configuration file, you first need to locate it. The configuration file is named nginx.conf and is placed in the directory /usr/local/nginx/conf, /etc/nginx, or /usr/local/etc/nginx by default.
Here is the link where you can receive the needed configuration file for your system.
You will need to choose your web server type, its version, and the version of the OpenSSL certificate.
If you are unsure which version you have, you can run the following command to locate the installed version of NGINX: nginx -v
To check the OpenSSL certificate version, use this command: openssl version
You will see the example of the configuration file for the chosen version that includes the virtual host for 443 port with the HSTS header in it. The tool also lists the OCSP values.
Please make sure to only copy the necessary values to your configuration file and keep in mind the Cipher Suite location.
All the provided values need to be copied to the server block for the secure 443 port.
Open the file in the text editor of your choice and copy the needed configuration file on Cipher Suites using this tool.
The copied code needs to be pasted right after the path to the Private key. Here is an example:
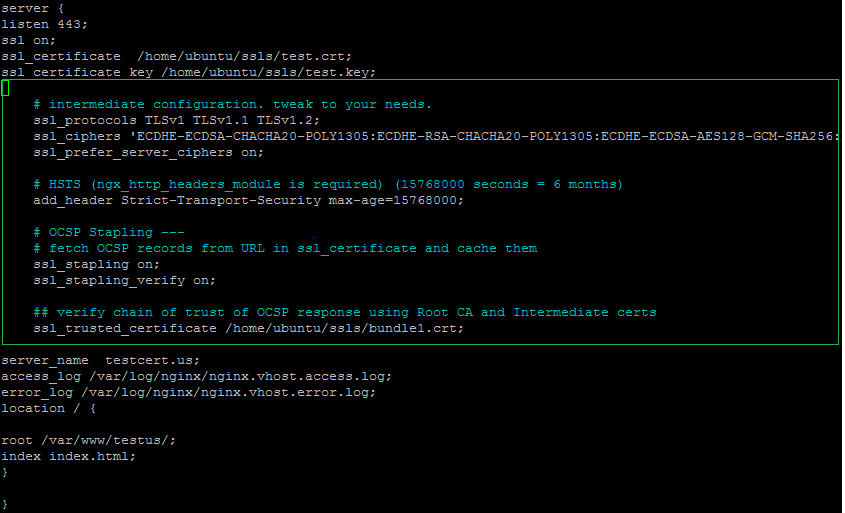
Once the configuration file is edited, you will need to restart your web server and save the changes.
You may use the following command: nginx -s reload
You can check the applied configuration file here.
If you encounter any difficulties with this process, please reach out to our 24/7 Customer Support Team!
Need help? We're always here for you.