{"/api/v1/ncpl/simplekb/getarticle:\"{\\\"articleId\\\":9782,\\\"categoryId\\\":38}\"":{"body":{"Id":9782,"FriendlyId":"","ArticleTypeId":0,"Title":"Security tips for business","ArticleName":"Security tips for business","ArticleSummary":null,"PreponedSummary":false,"Approved":true,"Body":"DQoJCTxwPklmIHlvdSBoYXZlIGp1c3Qgc3RhcnRlZCBhIGJ1c2luZXNzLCB5b3XigJlyZSBwcm9iYWJseSBhbHJlYWR5IGF3YXJlIG9mIHRoZSBpbXBhY3QgdGhlIEludGVybmV0IGhhcyBoYWQgb24gYWxsIGZhY2V0cyBvZiBvdXIgZWNvbm9teSBhbmQgY3VsdHVyZSB0b2RheS4gWW91IGFsc28ga25vdyBob3cgZXNzZW50aWFsIGl0IGlzIGZvciBhIG5ldyBjb21wYW55IHRvIGhhdmUgYSBzdHJvbmcgd2ViIHByZXNlbmNlLiA8L3A+DQoJCTxiciAvPllvdXIgd2Vic2l0ZSBpcyB0aGUgbWFpbiBjaGFubmVsIHlvdSB1c2UgdG8gY29tbXVuaWNhdGUgd2l0aCB5b3VyIGN1c3RvbWVycyBvbmxpbmUsIHNvIGl0IHNob3VsZCBiZSBhcyBzZWN1cmUgYXMgcG9zc2libGUgdG8gcHJvdGVjdCB5b3VyIGRhdGEgYW5kIGJ1aWxkIGN1c3RvbWVyIGNvbmZpZGVuY2UuIEluIHRoaXMgYXJ0aWNsZSwgd2Ugd2lsbCBkaWcgYSBiaXQgZGVlcGVyIGludG8gdGhlIGJhc2ljIHNlY3VyaXR5IG1lYXN1cmVzIHRoYXQgc2hvdWxkIGJlIHRha2VuIHRvIHByb3RlY3QgeW91ciBvbmxpbmUgYnVzaW5lc3MuPGJyIC8+T25lIG9mIHRoZSBwcmltYXJ5IGVsZW1lbnRzIG9mIG9ubGluZSBzZWN1cml0eSBpcyB0aGUgdXNlciBwYXNzd29yZC4gQWxsIGFjY291bnRzIHVzZWQgYnkgZW1wbG95ZWVzIGFuZCB1c2VycyBzaG91bGQgYmUgcHJvdGVjdGVkIHdpdGggYSBzdHJvbmcgcGFzc3dvcmQgdGhhdDo8YnIgLz4tIERvZXMgbm90IGNvbnRhaW4gc2ltcGxlIHNlcXVlbmNlcyBvciBjb21iaW5hdGlvbnMgc3VjaCBhcyAxMjM0NSBvciAwMDAwMC4gTmV2ZXIgdXNlIOKAnHBhc3N3b3Jk4oCdIGFzIHlvdXIgcGFzc3dvcmQuPGJyIC8+LSBEb2VzIG5vdCBjb250YWluIHlvdXIgbmFtZSwgdGhlIGNvbXBhbnkgbmFtZSwgb3IgYSBzaW1wbGUgd29yZCBvciBhIHdvcmQgY29tYmluYXRpb24gdGhhdCBjYW4gYmUgZWFzaWx5IGRlY3J5cHRlZCBieSBhIGRpY3Rpb25hcnkgcHJvZ3JhbS48YnIgLz4tIENvbnRhaW5zIGxvd2VyIGFuZCB1cHBlciBjYXNlIGxldHRlcnMsIG51bWJlcnMgYW5kIHNwZWNpYWwgY2hhcmFjdGVycyBzdWNoIGFzICQsICMsICouPGJyIC8+LSBJcyBhdCBsZWFzdCA4IGNoYXJhY3RlcnMgbG9uZy48YnIgLz5UaGVzZSBzYW1lIGd1aWRlbGluZXMgYXBwbHkgdG8geW91ciBOYW1lY2hlYXAgYWNjb3VudCBwYXNzd29yZC4gVGhvdWdoIGl04oCZcyBub3QgcmVxdWlyZWQsICB3ZSBzdHJvbmdseSBhZHZpc2UgdGhhdCB5b3UgY2hvb3NlIGEgcGFzc3dvcmQgdXNpbmcgdGhlIHBvaW50cyB3ZSBoYXZlIGNvdmVyZWQgYWJvdmUuPHA+PC9wPjxwPkFub3RoZXIgc2VjdXJpdHkgbWVhc3VyZSBpcyBUd28gRmFjdG9yIEF1dGhlbnRpY2F0aW9uIG9yIDJGQS4gVGhpcyBzdGVwIGhlbHBzIGtlZXAgeW91ciBhY2NvdW50cyB3aXRoIGRpZmZlcmVudCBzZXJ2aWNlcyBzYWZlIGZyb20gdHJlc3Bhc3NlcnMgd2hvIG1pZ2h0IHRyeSB1c2luZyB5b3VyIGNyZWRlbnRpYWxzIG9uIG11bHRpcGxlIHNpdGVzLiAyRkEgIGFkZHMgYW4gYWRkaXRpb25hbCBsYXllciBvZiBzZWN1cml0eSBieSByZXF1aXJpbmcgYWNjZXNzIHRvIHRoZSBwaG9uZSBudW1iZXIgYXNzb2NpYXRlZCB3aXRoIHRoZSBhY2NvdW50LiAgWW91IGNhbiBlbmFibGUgMkZBIGluIHlvdXIgTmFtZWNoZWFwIGFjY291bnQgYnkgZm9sbG93aW5nIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC85MjUzLzQ1L2hvdy10by10d28tZmFjdG9yLWF1dGhlbnRpY2F0aW9uLyIgdGFyZ2V0PSJfYmxhbmsiPnRoaXMgZ3VpZGU8L2E+LjwvcD48cD5JdOKAmXMgYSBnb29kIGlkZWEgIHRvIHVzZSBwYXNzd29yZCBtYW5hZ2VycyBzdWNoIGFzIDxhIGhyZWY9Imh0dHBzOi8vbGFzdHBhc3MuY29tLyIgdGFyZ2V0PSJfYmxhbmsiPkxhc3RQYXNzPC9hPiwgPGEgaHJlZj0iaHR0cHM6Ly93d3cuZGFzaGxhbmUuY29tLyIgdGFyZ2V0PSJfYmxhbmsiPkRhc2hsYW5lPC9hPiwgPGEgaHJlZj0iaHR0cDovL3d3dy5yb2JvZm9ybS5jb20vIiB0YXJnZXQ9Il9ibGFuayI+Um9ib2Zvcm08L2E+IGFuZCA8YSBocmVmPSJodHRwOi8va2VlcGFzcy5pbmZvLyIgdGFyZ2V0PSJfYmxhbmsiPktlZVBhc3M8L2E+IHRvIHNlY3VyZWx5IHN0b3JlIGFuZCBtYW5hZ2UgeW91ciBwYXNzd29yZHMuICBUaGVzZSBwcm9ncmFtcyBjYW4gYWxzbyBhdXRvLWdlbmVyYXRlIHN0cm9uZyBwYXNzd29yZHMgdGhhdCBtZWV0IHRoZSBhYm92ZS1tZW50aW9uZWQgcmVxdWlyZW1lbnRzLiA8L3A+PGJyIC8+VG8gbWFpbnRhaW4gYSBmdWxseSBzZWN1cmUgd29yayBlbnZpcm9ubWVudCwgd2UgcmVjb21tZW5kIHlvdSBzdHJvbmdseSBlbmNvdXJhZ2UgeW91ciBlbXBsb3llZXMgdG8gdXNlIHRoZXNlIHBhc3N3b3JkIG1hbmFnZXJzIGZvciBhbGwgd29yay1yZWxhdGVkIHNlcnZpY2VzIGFuZCB0byBuZXZlciBkaXNjbG9zZSB0aGUgcGFzc3dvcmRzIGZvciB0aGVpciB3b3JrIGFjY291bnRzLjxwPlNpbmNlIHlvdXIgd2Vic2l0ZSB1c2VzIHZhcmlvdXMgc29mdHdhcmUgZm9yIGhvc3RpbmcgYW5kIG1hbmFnZW1lbnQsIGJlIHN1cmUgdG8ga2VlcCBpdCB1cGRhdGVkIHdpdGggdGhlIGxhdGVzdCBzb2Z0d2FyZSB1cGRhdGVzLCBzaW5jZSwgd2l0aCBlYWNoIHVwZGF0ZSwgdGhlIGNvbXBhbnkgZml4ZXMgcmVwb3J0ZWQgZXJyb3JzIGFuZCBidWdzLCBhbmQgbWluaW1pemVzIHZ1bG5lcmFiaWxpdGllcy4gPC9wPjxiciAvPllvdXIgd2ViIGhvc3RpbmcgY29tcGFueSBzaG91bGQgYWxzbyBkbyByZWd1bGFyIHVwZGF0ZXMgb2YgdGhlaXIgc29mdHdhcmUgdG8gcmVkdWNlIHZ1bG5lcmFiaWxpdGllcywgdGhvdWdoIGl0IGlzIHJlY29tbWVuZGVkIHRoYXQgeW91IG1hbnVhbGx5IHVwZGF0ZSB5b3VyIGhvc3Rpbmcgc29mdHdhcmUgYXMgb2Z0ZW4gYXMgcG9zc2libGUuICA8YnIgLz5JZiB5b3UgZGVjaWRlIHRvIGhvc3QgeW91ciBzaXRlIHdpdGggTmFtZWNoZWFwLCB5b3XigJlsbCBhbHdheXMgYmUgb24gdGhlIHNhZmUgc2lkZS4gV2UgdGFrZSBzZWN1cml0eSBzZXJpb3VzbHksIHVzaW5nIG9ubHkgdGhlIGxhdGVzdCBoYXJkd2FyZSBhbmQgc29mdHdhcmUgZmlyZXdhbGxzLiBXZSBjb25zdGFudGx5IHRlc3QgYW5kIHNjYW4gdGhlIGRlZmVuc2Ugc3lzdGVtcyBvdXIgc2VydmVycyBhcmUgc2VjdXJlZCB3aXRoIGFzIHdlbGwuIEFsc28sIHdlIHVwZGF0ZSB0aGUgc29mdHdhcmUgdGhhdCBpcyB1c2VkIG9uIG91ciBzZXJ2ZXJzIGFuZCBub3RpZnkgb3VyIGN1c3RvbWVycyBhYm91dCByZWNvbW1lbmRlZCB1cGRhdGVzIG9mIHRoZSBzZXJ2aWNlcyB3ZSBwcm92aWRlLiBZb3UgY2FuIGNoZWNrIGFsbCB0aGUgaG9zdGluZyBwYWNrYWdlcyB3ZSBwcm92aWRlIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vaG9zdGluZy8iIHRhcmdldD0iX2JsYW5rIj5oZXJlPC9hPi48YnIgLz5PdXIgc3Ryb25nIHN0YW5jZSB0b3dhcmRzIHNlY3VyaXR5IGFwcGxpZXMgdG8gYWxsIHRoZSBzZXJ2aWNlcyB3ZSBwcm92aWRlIGluY2x1ZGluZyBlbWFpbCBob3N0aW5nLCBTU0wgY2VydGlmaWNhdGVzIGFuZCBkb21haW5zLiBXZSBoYXZlIHdvcmxkLWNsYXNzIGFudGktc3BhbSBhbmQgYW50aS12aXJ1cyBwcm90ZWN0aW9uIHVzaW5nIFNwYW1FeHBlcnRzIHRlY2hub2xvZ3kgdGhhdCBjb21lcyB3aXRoIG91ciA8YSBocmVmPSJodHRwczovL3d3dy5uYW1lY2hlYXAuY29tL2hvc3RpbmcvZW1haWwvIiB0YXJnZXQ9Il9ibGFuayI+ZW1haWwgaG9zdGluZyBzZXJ2aWNlczwvYT4uIFlvdSBjYW4gYWxzbyBrZWVwIHlvdXIgZG9tYWluIGNvbnRhY3QgaW5mb3JtYXRpb24gcHJpdmF0ZSB3aXRoIHRoZSBoZWxwIG9mIG91ciBXaG9pcyBQcml2YWN5IFByb3RlY3Rpb24gc2VydmljZSB3aGljaCBwcmV2ZW50cyBpdCBmcm9tIGJlaW5nIGxpc3RlZCBpbiB0aGUgcHVibGljIFdob2lzIGRhdGFiYXNlLiBPdXIgPGEgaHJlZj0iaHR0cHM6Ly93d3cubmFtZWNoZWFwLmNvbS9zdXBwb3J0L2tub3dsZWRnZWJhc2UvY2F0ZWdvcnkuYXNweC8yMjMxL3ByZW1pdW1kbnMvIiB0YXJnZXQ9Il9ibGFuayI+UHJlbWl1bUROUyBzZXJ2aWNlPC9hPiBwcm92aWRlcyB5b3VyIGRvbWFpbiBuYW1lc2VydmVycyB3aXRoIGFkdmFuY2VkIEREb1MgcHJvdGVjdGlvbi48cD5EZXNwaXRlIGhhdmluZyB1cGRhdGVkIHNvZnR3YXJlLCBob3dldmVyLCB0aGVyZeKAmXMgc3RpbGwgcGxlbnR5IG9mIG1hbHdhcmUgdGhhdCBjYW4gaW5mZWN0IHlvdXIgd2Vic2l0ZSB3aXRob3V0IHlvdSBiZWluZyBhd2FyZS4gRm9yIGV4YW1wbGUsIHNpdGVzIHRoYXQgc3ByZWFkIG1hbHdhcmUgY2FuIGltcGxlbWVudCBtYWxpY2lvdXMgY29kZSBvbiB5b3VyIHdlYnNpdGUgdG8gcmVkaXJlY3QgdmlzaXRvcnMgc29tZXdoZXJlIGVsc2UuIEFsd2F5cyBzY2hlZHVsZSByZWd1bGFyIG1vbnRobHkgb3Igd2Vla2x5IHNlY3VyaXR5IGNoZWNrcyB0byBiZSBvbiB0aGUgc2FmZSBzaWRlLjwvcD48YnIgLz5Nb3N0IGhvc3RpbmcgcHJvdmlkZXJzIG9mZmVyIHdheXMgdG8gc2VjdXJlbHkgYWNjZXNzIGFuZCBjaGVjayB0aGUgc2VydmVyIHRoYXQgaG9zdHMgeW91ciBzaXRlLjxiciAvPk9uZSBvZiB0aGUgbW9zdCBjb21tb24gbWV0aG9kcyB1c2VkIHRvIHNlY3VyZWx5IGFjY2VzcyBhIHJlbW90ZSBzZXJ2ZXIgaXMgU1NIICBvciBTZWN1cmUgU2hlbGwuIFRoaXMgaXMgYSBwcm90b2NvbCB0aGF0IGFsbG93cyB5b3UgdG8gZXhlY3V0ZSBjb21tYW5kcyBvbiBhIHNlcnZlciByZW1vdGVseSBvciB0cmFuc2ZlciBmaWxlcyBmcm9tIG9uZSBtYWNoaW5lIHRvIGFub3RoZXIgdXRpbGl6aW5nIGEgc2VjdXJlIGNoYW5uZWwuIFNpbXBsZSBzb2Z0d2FyZSBwcm9ncmFtcyB3aXRoIGVhc3kgaW50ZXJmYWNlcyBoYXZlIGJlZW4gZGVzaWduZWQgZm9yIFNTSCBhY2Nlc3MsIHdlIGhhdmUgYSBsaXN0IG9mIHRob3NlIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC8xMDIyLzg5L2hvdy10by1nZXQtYW4tc3NoLWNsaWVudC8iIHRhcmdldD0iX2JsYW5rIj5oZXJlPC9hPi4gSWYgeW91IHdpc2ggdG8gZ2FpbiBTU0ggYWNjZXNzIHRvIHlvdXIgZXhpc3RpbmcgaG9zdGluZyBwYWNrYWdlIHRocm91Z2ggeW91ciBob3N0aW5nIHByb3ZpZGVyLCB3ZSByZWNvbW1lbmQgY29udGFjdGluZyB0aGVtIGZvciB0aGUgYWNjZXNzIGRldGFpbHMuIEFsbCA8YSBocmVmPSJodHRwczovL3d3dy5uYW1lY2hlYXAuY29tL2hvc3RpbmcvIiB0YXJnZXQ9Il9ibGFuayI+TmFtZWNoZWFwIGhvc3Rpbmc8L2E+IHNlcnZlcnMgY2FuIGJlIGFjY2Vzc2VkIG92ZXIgU1NILCBhbmQgd2UgaGF2ZSBhIGRldGFpbGVkIGd1aWRlIG9uIHRoYXQgPGEgaHJlZj0iaHR0cHM6Ly93d3cubmFtZWNoZWFwLmNvbS9zdXBwb3J0L2tub3dsZWRnZWJhc2UvYXJ0aWNsZS5hc3B4LzEwMTYvODkvaG93LXRvLWFjY2Vzcy1ob3N0aW5nLWFjY291bnQtdmlhLXNzaC8iIHRhcmdldD0iX2JsYW5rIj5oZXJlPC9hPi48YnIgLz5GaWxlIHRyYW5zZmVyIGlzIGFub3RoZXIgc2V0dGluZyB0aGF0IGNhbiBiZSBhcnJhbmdlZCB1c2luZyBjZXJ0YWluIHNlY3VyaXR5IHByb3RvY29scywgc3BlY2lmaWNhbGx5LCBzZWN1cmUgRlRQIChTRlRQKS4gVXN1YWxseSwgdW5lbmNyeXB0ZWQgd2Vic2l0ZSBkYXRhIGlzIHVwbG9hZGVkIHRvIHRoZSBzZXJ2ZXIgdXNpbmcgRlRQIChmaWxlIHRyYW5zZmVyIHByb3RvY29sKS4gU0ZUUCBlbmNyeXB0cyB0aGUgdHJhbnNtaXR0ZWQgZGF0YSBzbyB0aGF0IG9ubHkgdGhlIFNGVFAgY2xpZW50IGFuZCBTRlRQIHNlcnZlciBvZiB0aGUgY3VycmVudCBzZXNzaW9uIGNhbiBkZWNyeXB0IGl0LiBUaGUgU0ZUUCBwb3J0IG1vc3Qgb2Z0ZW4gdXNlZCBpcyAyMiwgd2hpY2ggaXMgY29uZmlndXJlZCBpbiB0aGUgRlRQIGNsaWVudC4gWW91IGNhbiB1c2UgU0ZUUCB3aXRoIE5hbWVjaGVhcCBob3N0aW5nIHZpYSB0aGUgMjEwOTggcG9ydC4gTW9yZSBkZXRhaWxzIGFib3V0IHRoaXMgYXJlIGF2YWlsYWJsZSBpbiA8YSBocmVmPSJodHRwczovL3d3dy5uYW1lY2hlYXAuY29tL3N1cHBvcnQva25vd2xlZGdlYmFzZS9hcnRpY2xlLmFzcHgvMTg4LzIwNS9ob3ctdG8tYWNjZXNzLWFjY291bnQtdmlhLWZ0cC8iIHRhcmdldD0iX2JsYW5rIj50aGlzIGFydGljbGU8L2E+LjxiciAvPklmIHlvdSBtYW5hZ2UgeW91ciBob3N0aW5nIHVzaW5nIGEgY29udHJvbCBwYW5lbCwgaXQgaXMgbW9zdCBsaWtlbHkgYWNjZXNzaWJsZSB2aWEgYSBub24tc3RhbmRhcmQgcG9ydC4gRm9yIGNQYW5lbCwgdGhpcyBwb3J0IGlzIDIwODMgYW5kIGZvciBQbGVzaywgaXQgaXMgODQ0MywgdGhlIGdlbmVyYWwgaWRlYSBiZWluZyB0byBoYXZlIHRoZSBjb250cm9sIHBhbmVsIGFjY2Vzc2libGUgaW4gYSB3YXkgb3RoZXIgdGhhbiB0aGUgdXN1YWwgcG9ydCA4MCBIVFRQIGNvbm5lY3Rpb24sKCBzb21ldGhpbmcgd2UgYWxzbyBlbmNvdXJhZ2UgeW91IHRvIGRvIGlmIHlvdSB3YW50IHRvIGNvbW11bmljYXRlIHdpdGggdGhlIGhvc3Rpbmcgc2VydmVyIHNlY3VyZWx5KS4gV2l0aCBOYW1lY2hlYXAgaG9zdGluZyBzZXJ2ZXJzIHRoYXQgdXNlIGNQYW5lbCwgeW91IGNhbiBhbHdheXMgcmVhY2ggdGhlIGhvc3RpbmcgbWFuYWdlbWVudCBhcmVhIHNlY3VyZWx5IHRocm91Z2ggdGhlIDIwODMgcG9ydC48cD48L3A+PHA+RW1haWwgaXMgYW4gZXNzZW50aWFsIHBhcnQgb2YgZXZlcnkgYnVzaW5lc3MgdGhhdCBvdWdodCB0byBiZSBwcm90ZWN0ZWQgYXMgd2VsbC4gSXQgaXMgcG9zc2libGUgdG8gbm90IG9ubHkgc2VjdXJlIHRoZSBjb25uZWN0aW9uIHRvIHlvdXIgbWFpbCBzZXJ2ZXIsIGJ1dCBhbHNvIHRvIHNpZ24geW91ciBlbWFpbHMgd2l0aCBzZWN1cml0eSBjZXJ0aWZpY2F0ZXMsIGtub3duIGFzIFMvTUlNRSBjZXJ0aWZpY2F0ZXMuPGJyIC8+R2VuZXJhbGx5LCBzZWN1cmUgbWFpbCBwb3J0cyBhcmUgdXNlZCB0byBjb25uZWN0IHRvIHRoZSBtYWlsIHNlcnZlciwgc3VjaCBhcyA5OTUgKGluc3RlYWQgb2Ygc3RhbmRhcmQgMTAwIGZvciBQT1AzKSwgOTkzIChpbnN0ZWFkIG9mIDE0MyBmb3IgSU1BUCksIGFuZCA0NjUgKGluc3RlYWQgb2YgMjUgZm9yIFNNVFApLiBZb3UgbWF5IHNldCBhIHNlY3VyZSBjb25uZWN0aW9uIHRvIGEgPGEgaHJlZj0iaHR0cHM6Ly93d3cubmFtZWNoZWFwLmNvbS9ob3N0aW5nL2VtYWlsLyIgdGFyZ2V0PSJfYmxhbmsiPk5hbWVjaGVhcCBQcml2YXRlIGVtYWlsPC9hPiBzZXJ2aWNlIHVzaW5nIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC8xMTc5LzIxNzUvZ2VuZXJhbC1jb25maWd1cmF0aW9uLWZvci1tYWlsLWNsaWVudHMtYW5kLW1vYmlsZS1kZXZpY2VzLyIgdGFyZ2V0PSJfYmxhbmsiPnRoaXMgZ3VpZGU8L2E+LjwvcD48cD5XZeKAmWQgYWxzbyBsaWtlIHRvIHRha2UgYSBtb21lbnQgdG8gZGVzY3JpYmUgaG93IHBoaXNoaW5nIGF0dGFja3Mgd29yaywgc28gdGhhdCB5b3UgY2FuIHNlY3VyZSB5b3Vyc2VsZiBmcm9tIHRoZW0gYXMgd2VsbC4gTGV04oCZcyBzYXksIGZvciBleGFtcGxlLCB5b3UgcmVjZWl2ZSBhbiBlbWFpbCB0aGF0IGNsYWltcyB0byBiZSBmcm9tIOKAnFlvdXIgdHJ1c3RlZCBiYW5r4oCdLCBhbmQgaW5kZWVkLCBhcHBlYXJzIHRvIGJlIGZyb20gdGhlIGFjdHVhbCBiYW5rIHdoZXJlIHlvdSBrZWVwIHlvdXIgbW9uZXkuIFRoZSBlbWFpbCBtYXkgYXNrIHlvdSwgZm9yIGV4YW1wbGUsIHRvIHZpc2l0IGEgbGluayBhbmQgcHJvdmlkZSBjZXJ0YWluIGNyaXRpY2FsIGFjY291bnQgaW5mb3JtYXRpb24uIFRoZSBlbWFpbCBtYXkgYWxzbyBjbGFpbSB0aGF0IHRoZXkgc2ltcGx5IG5lZWQgdG8g4oCcY29uZmlybeKAnSB0aGlzIGRhdGEsIG9yIHRoZXkgbWF5IHdhcm4gdGhhdCB5b3VyIGFjY291bnQgbWF5IGJlIGNsb3NlZCBvciB0aGF0IHlvdSBtYXkgaW5jdXIgZmVlcyBpZiB5b3UgZG8gbm90IHRha2UgaW1tZWRpYXRlIGFjdGlvbi4gLiBSZWdhcmRsZXNzIG9mIHRoZSByZXF1ZXN0LCBpdCBpcyBpbXBvcnRhbnQgdG8gcmVtZW1iZXIgdGhhdCBiYW5rcyBhbmQgb3RoZXIgY3JlZGlibGUgZmluYW5jaWFsIG9yZ2FuaXphdGlvbnMgd2lsbCBuZXZlciBhc2sgZm9yIHBlcnNvbmFsIGluZm9ybWF0aW9uIHZpYSBlbWFpbC4gWW91IHNob3VsZCBuZXZlciBzaGFyZSBhbnkgcGVyc29uYWwgaW5mb3JtYXRpb24gdmlhIGxpbmtzIHByb3ZpZGVkIGluIHRoZXNlIHR5cGVzIG9mIGVtYWlscy4uLiBJZiB5b3UgY2xpY2sgdGhlIGxpbmssIG1ha2Ugc3VyZSBpdCBicmluZ3MgeW91IHRvIHRoZSBzYW1lIGxvY2F0aW9uIGl0IGNsYWltcyB0byBwb2ludCB0by4gQXMgYW4gZXhhbXBsZSBvZiB0aGlzLCAgbG9vayBhdCB0aGUgdHdvIGxpbmtzIGJlbG93OiA8YSBocmVmPSJodHRwczovL3d3dy5uYW1lY2hlYXAuY29tLyIgdGFyZ2V0PSJfYmxhbmsiPmh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb208L2E+IGFuZCA8YSBocmVmPSJodHRwczovL3d3dy5nb29nbGUuY29tLyIgdGFyZ2V0PSJfYmxhbmsiPmh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb208L2E+LjwvcD48YnIgLz5Zb3XigJlsbCBmaW5kIGJ5IGNsaWNraW5nIG9uIHRoZW0gKGRvbuKAmXQgd29ycnksIHRoZXnigJlyZSBib3RoIHNhZmUpIHRoYXQsIHdoaWxlIHRoZXkgbG9vayBpZGVudGljYWwsIHRoZSBmaXJzdCBvbmUgdGFrZXMgeW91IHRvIG91ciBtYWluIHBhZ2UsIHdoaWxlIHRoZSBzZWNvbmQgb25lIGFjdHVhbGx5IGRpcmVjdHMgeW91IHRvIHRoZSBHb29nbGUgaG9tZXBhZ2UuPGJyIC8+PGRpdj5TbyBob3cgY2FuIHlvdSB0ZWxsIHRoZSBhY3R1YWwgbGluayBmcm9tIGEgaGlkZGVuIHJlZGlyZWN0PyBJbiBtb3N0IGNhc2VzLCB5b3UgY2FuIGp1c3QgaG92ZXIgdGhlIG1vdXNlIG92ZXIgdGhlIGxpbmssIHRoaXMgd2lsbCBicmluZyB1cCB0aGUgbWV0YWRhdGEgdGhhdCBzaG93cyB0aGUgYWN0dWFsIHdlYnNpdGUgYWRkcmVzcy4gT2Z0ZW4gdGhpcyBtZXRhZGF0YSBpcyBkaXNwbGF5ZWQgaW4gdGhlIHN0YXR1cyBtZXNzYWdlIG9mIHlvdXIgYnJvd3NlciBpbiB0aGUgYm90dG9tIG9mIHRoZSBicm93c2VyIHdpbmRvdywgdGhvdWdoIGl0IG1heSBhbHNvIGFwcGVhciBuZXh0IHRvIHlvdXIgY3Vyc29yIG9yLCBpbiBzb21lIGNhc2VzLCBieSByaWdodC1jbGlja2luZyBvbiB0aGUgbGluayBpdHNlbGYgKHRoaXMgYWN0aW9uIHdpbGwgbm90IG9wZW4gdGhlIGxpbmspLiBZb3UgY2FuIGZpbmQgdGhlIHNjcmVlbnNob3Qgb2YgdGhlIOKAnGdvb2TigJ0gYW5kIOKAnGJhZOKAnSBsaW5rc+KAmSBtZXRhZGF0YSBiZWxvdzo8L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+PGk+R29vZCBsaW5rPGJyIC8+PGJyIC8+PC9pPjwvZGl2PjxwPjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9zY3QxLnBuZyIgYWx0PSJzY3QxIiB3aWR0aD0iNDU0IiBoZWlnaHQ9Ijc0IiBib3JkZXI9IjAiIC8+PC9wPjxwPjxiciAvPjwvcD48cD48aT5CYWQgbGluazwvaT48L3A+PHA+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL3NjdDIucG5nIiBhbHQ9InNjdDEiIHdpZHRoPSI0NTciIGhlaWdodD0iNzQiIGJvcmRlcj0iMCIgLz48L3A+PHA+PC9wPjxwPkluIG9yZGVyIHRvIGVuY3J5cHQgYW5kIHNlY3VyZSB0aGUgdHJhZmZpYyBiZXR3ZWVuIHlvdXIgd2Vic2l0ZSBhbmQgdmlzaXRvcnMgYmUgLCB3ZSByZWNvbW1lbmQgaW1wbGVtZW50aW5nIGFuIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc2VjdXJpdHkvc3NsLWNlcnRpZmljYXRlcy8iPlNTTCBjZXJ0aWZpY2F0ZTwvYT4gb24geW91ciBzaXRlLjxiciAvPlNTTCAod2hpY2ggc3RhbmRzIGZvciBTZWN1cmUgU29ja2V0cyBMYXllcikgY2VydGlmaWNhdGVzIGNvbWUgaW4gdmFyaW91cyBsZXZlbHMgb2Ygc2VjdXJpdHkgdG8gZml0IHRoZSBzcGVjaWZpYyBuZWVkcyBvZiB5b3VyIHNpdGUuIC4gV2Ugd2lsbCBicmllZmx5IHRha2UgYSBsb29rIGF0IGVhY2ggb2YgdGhlc2UgY2VydGlmaWNhdGVzIGFuZCB3aWxsIGRlc2NyaWJlIHRoZW0gaW4gdGVybXMgb2YgaG93IHRoZSB2YWxpZGF0aW9uIG9mIHRoZSBkb21haW4gbmFtZSBpcyBhcnJhbmdlZC48YnIgLz5UaGUgbW9zdCBiYXNpYyB0eXBlIG9mIGNlcnRpZmljYXRlIGlzIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc2VjdXJpdHkvc3NsLWNlcnRpZmljYXRlcy9kb21haW4tdmFsaWRhdGlvbi8iIHRhcmdldD0iX2JsYW5rIj5kb21haW4gdmFsaWRhdGlvbjwvYT4gKERWLiBBIERWIGNlcnRpZmljYXRlIHdpbGwgc2hvdyB3aG8gb3ducyB0aGUgZG9tYWluIG5hbWUgYW5kIHdpbGwgcHJvdmlkZSBlbmNyeXB0aW9uIG9mIHNpdGUgdHJhZmZpYy4gPGJyIC8+VG8gc2hvdyB5b3VyIGN1c3RvbWVycyB5b3VyIGRvbWFpbiBvd25lcnNoaXAgaW5mb3JtYXRpb24gYXMgd2VsbCBhcyB2YWxpZGF0aW9uIHRoYXQgIHlvdXIgY29tcGFueSBpcyBvZmZpY2lhbGx5IG93bmVkIGFuZCByZWdpc3RlcmVkIGJ5IHlvdSwgd2UgcmVjb21tZW5kIGFuIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc2VjdXJpdHkvc3NsLWNlcnRpZmljYXRlcy9vcmdhbml6YXRpb24tdmFsaWRhdGlvbi8iIHRhcmdldD0iX2JsYW5rIj5vcmdhbml6YXRpb24gdmFsaWRhdGlvbjwvYT4gKE9WKWNlcnRpZmljYXRlLiBPViBjZXJ0cyBkaXNwbGF5IHlvdXIgY29tcGFueSBuYW1lIGFuZCBhZGRyZXNzIGluIHRoZSBjZXJ0aWZpY2F0ZSBkZXRhaWxzLiBBZGRpdGlvbmFsbHksIHRoZXkgcmVxdWlyZSB5b3UgdG8gcGFzcyBhIGNvbXBhbnkgdmVyaWZpY2F0aW9uIHByb2Nlc3Mgd2l0aCB0aGUgQ2VydGlmaWNhdGUgQXV0aG9yaXR5IChDQSkgdGhhdCBpc3N1ZXMgdGhlIGNlcnRpZmljYXRlLiBUaGlzIG1heSBpbmNsdWRlIHJlcXVpcmVtZW50cyBzdWNoIGFzIGhhdmluZyB5b3VyIG9yZ2FuaXphdGlvbiBsaXN0ZWQgaW4gYSBidXNpbmVzcyBjcmVkaXQgbGlzdGluZyBsaWtlIER1biAmYW1wOyBCcmFkc3RyZWV0LCBvciBhIHB1YmxpYyBkYXRhYmFzZSBsaWtlIFllbGxvd1BhZ2VzLmNvbS4gQmUgc3VyZSB5b3VyIGJ1c2luZXNzIGNhbiBiZSB2YWxpZGF0ZWQgdGhyb3VnaCBjaGFubmVscyBzdWNoIGFzIHRoZXNlIGJlZm9yZSBjaG9vc2luZyBhbiBPViBjZXJ0aWZpY2F0ZS48YnIgLz48YSBocmVmPSJodHRwczovL3d3dy5uYW1lY2hlYXAuY29tL3NlY3VyaXR5L3NzbC1jZXJ0aWZpY2F0ZXMvZXh0ZW5kZWQtdmFsaWRhdGlvbi8iIHRhcmdldD0iX2JsYW5rIj5FeHRlbmRlZCB2YWxpZGF0aW9uPC9hPiAoRVYpIGNlcnRpZmljYXRlcyBhcmUgYSBncmVhdCBvcHRpb24gZm9yIHRvcC10aWVyIHNlY3VyaXR5LiBMaWtlIE9WIGNlcnRpZmljYXRlcywgRVYgY2VydHMgcmVxdWlyZSB5b3VyIGNvbXBhbnkgdG8gYmUgaW5jb3Jwb3JhdGVkLCB2ZXJpZmllZCB3aXRoIHRoZSBpc3N1aW5nIENBLCBtYWludGFpbiBhIGNvcnBvcmF0ZSBwaG9uZSBudW1iZXIgbGlzdGVkIGluIGEgZGlyZWN0b3J5IG9mIHlvdXIgY291bnRyeSwgYW5kIGJlIHJlZ2lzdGVyZWQgaW4gYSBidXNpbmVzcyBjcmVkaXQgbGlzdGluZyBzdWNoIGFzIER1biAmYW1wOyBCcmFkc3RyZWV0LiBUaGUgdmVyaWZpY2F0aW9uIGlzIG1vcmUgdGhvcm91Z2gsIGFuZCB0aGUgZXhwbGljaXQgY29tcGFueSBkZXRhaWxzIHdpbGwgYmUgcmVmbGVjdGVkIG9uIHRoZSBjZXJ0aWZpY2F0ZSBkZXRhaWxzIHBhbmVsIGluIHRoZSBicm93c2VyIGFuZCBvbiB0aGUgc2l0ZSBzZWFsLiBXZSByZWNvbW1lbmQgY2hvb3NpbmcgYW4gRVYgY2VydCBvbmx5IGlmIHlvdXIgYnVzaW5lc3MgaXMgYWJsZSB0byBhY2NvbW1vZGF0ZSB0aGlzIHJpZ29yb3VzIHZhbGlkYXRpb24gcHJvY2VzcyBhbmQgeW91IHJlcXVpcmUgdGhlIGhpZ2hlc3QgY2VydGlmaWNhdGUgYXNzdXJhbmNlIGxldmVsLjwvcD48cD5Eb21haW5zLCBob3N0aW5nIHNlcnZpY2VzLCBTU0wgY2VydGlmaWNhdGVzLCBzb2Z0d2FyZSwgYW5kIG90aGVyIHNlcnZpY2VzIHJlcXVpcmUgaGF2aW5nIGEgbWFuYWdlZCBhY2NvdW50IHdpdGggb25lIG9yIG1vcmUgcHJvdmlkZXJzLiBJZiB5b3VyIGJ1c2luZXNzIGhhcyBvbmx5IG9uZSBwZXJzb24gbWFuYWdpbmcgeW91ciBhY2NvdW50KHMpLCBpdOKAmXMgYWR2aXNhYmxlIHRvIGhhdmUgYSBwbGFuIGZvciB3aGVuIGFuZCBpZiB0aGF0IHBlcnNvbiBpcyBzdWRkZW5seSB1bmF2YWlsYWJsZS48L3A+PGJyIC8+V2UgcmVjb21tZW5kIHRoYXQgeW91IGhhdmUgYXQgbGVhc3Qgb25lIGFkZGl0aW9uYWwgcGVyc29uIGluIHlvdXIgY29tcGFueSB0aGF0IGlzIGFibGUgdG8gc2VhbWxlc3NseSBtYW5hZ2UgeW91ciB3ZWIgc2VydmljZXMgc2hvdWxkIHRoZSBuZWVkIGFyaXNlLiBUaGlzIHdheSwgaWYgdGhlIGVtcGxveWVlIGxlYXZlcywgeW91IHdpbGwgYWxyZWFkeSBoYXZlIHRoZSByZXNvdXJjZXMgaW4gcGxhY2UgdG8gcmV0YWluIGNvbnRyb2wgb2YgeW91ciB2aXRhbCBhY2NvdW50cy48YnIgLz5BIHZlcnkgaW1wb3J0YW50IHBhcnQgb2Ygb3ZlcmFsbCBzZWN1cml0eSBpcyBjb250cm9sbGluZyB0aGUgb25saW5lIGFjdGl2aXR5IG9mIHlvdXIgZW1wbG95ZWVzLCBpbmNsdWRpbmcgZG93bmxvYWRzIHRoZSB3ZWJzaXRlcyB0aGV5IHZpc2l0LiBIYXZpbmcgYSBzdHJpY3QgY29tcGFueSBwb2xpY3kgb24gd2hhdCBmaWxlIGZvcm1hdHMgYXJlIGFsbG93ZWQgYW5kIGZyb20gd2hpY2ggc291cmNlcyBjYW4gaGVscCBrZWVwIHlvdXIgYnVzaW5lc3MgbmV0d29yayBzYWZlIGZyb20gd29ybXMgYW5kIG1hbHdhcmUuIEZpbGUgZm9ybWF0cyB0aGF0IGFyZSBtb3N0IGxpa2VseSB0byBiZSBpbmZlY3RlZCBieSB2aXJ1c2VzIGFyZTogLmV4ZSwgLmpzLCAuamFyLCBvciAuanNlLiBUbyBkZW1vbnN0cmF0ZSBob3cgZGFuZ2Vyb3VzIHN1Y2ggdmlydXNlcyBjYW4gYmUsIHdl4oCZbGwgc2hvdyB5b3UgYW4gZXhhbXBsZS48cD5MZXTigJlzIGFzc3VtZSB5b3VyIGNvbXBhbnkgaGFzIDMwIGVtcGxveWVlcywgYWxsIG9mIHdoaWNoIGFyZSBwcmV0dHkgZmFtaWxpYXIgd2l0aCB0aGUgY29tcGFueeKAmXMgcG9saWN5IHJlZ2FyZGluZyBkb3dubG9hZHMgZnJvbSB0aGUgaW50ZXJuZXQuIFlvdXIgY29tcGFueSBtYW5hZ2VzIDEwMDAgcGF5bWVudCB0cmFuc2FjdGlvbnMgZXZlcnkgZGF5LCBtZWFuaW5nIHlvdeKAmXJlIHN0b3JpbmcgdG9ucyBvZiBjcmVkaXQgY2FyZCBhbmQgb3RoZXIgcGVyc29uYWwgY3VzdG9tZXIgaW5mb3JtYXRpb24gaW4geW91ciBpbnRlcm5hbCBkYXRhYmFzZS4gTGV04oCZcyBhbHNvIGFzc3VtZSB5b3XigJl2ZSBpbXBsZW1lbnRlZCBhbGwgdGhlIHNlY3VyaXR5IG1lYXN1cmVzIHJlY29tbWVuZGVkIGluIHRoaXMgYXJ0aWNsZSB1cCB0byB0aGlzIHBvaW50LiBTbywgdGhlIGRheSBjb21lcyB3aGVuIG9uZSBvZiB5b3VyIGVtcGxveWVlcyBhY2NpZGVudGFsbHkgZG93bmxvYWRzIGFuIGF0dGFjaG1lbnQgaW4gb25lIG9mIHRob3NlIOKAnFlvdSBoYXZlIHdvbiBhICQxMC4wMDAgbG90dGVyeSHigJ0gZW1haWxzLiBUaGUgZW1haWwgY29udGFpbnMgYSB3b3JtIHRoYXQgaW1tZWRpYXRlbHkgcnVucyBhbmQgY2xvbmVzIGl0c2VsZiBhbGwgb3ZlciB5b3VyIGVudGlyZSBjb21wYW55IG5ldHdvcmssIHN0ZWFsaW5nIHlvdXIgY3VzdG9tZXJz4oCZIHBlcnNvbmFsIGRhdGEgYW5kIHNlbmRpbmcgaXQgdG8gdGhlIHdvcm0gY3JlYXRvci4gQXQgdGhpcyBwb2ludCwgYWxsIHlvdSBjYW4gZG8gaXMgc3dpdGNoIG9mZiB5b3VyIG9mZmljZSBpbnRlcm5ldCB0byBlbnN1cmUgdGhlIGluZm9ybWF0aW9uIGRvZXMgbm90IGdvIGZ1cnRoZXIgdGhhbiB5b3VyIGludGVybmFsIG5ldHdvcmssIGFuZCB0aGlzIGlzIGFzc3VtaW5nIHlvdSBzb21laG93IGZpbmQgb3V0IGhvdyB0aGUgdmlydXMgYWN0dWFsbHkgd29ya3MuIFN1Y2ggYSB3b3JtIGNhbiBhbHNvIHNpbXBseSBkZWxldGUgYWxsIHRoZSBpbmZvcm1hdGlvbiBvbiBhbGwgeW91ciBjb21wdXRlcnMsIHRha2luZyB5b3UgYmFjayB0byBzcXVhcmUgb25lLiBBcyB5b3UgY2FuIHByb2JhYmx5IHRlbGwgYXQgdGhpcyBwb2ludCBpbiBvdXIgZXhhbXBsZSwgdGhpcyBpcyBub3QgZXZlbiB0aGUgd29yc3QtY2FzZSBzY2VuYXJpby48L3A+PGJyIC8+QWxsIG9mIHRoaXMgYmVpbmcgc2FpZCwgd2UgcmVjb21tZW5kIG1vdmluZyB5b3VyIGNvbXBhbnkgZGF0YSAob3IgYXQgbGVhc3QgdGhlIG1vc3QgaW1wb3J0YW50IHBhcnQgb2YgaXQpIHRvIHRoZSBjbG91ZC4gTm93YWRheXMsIGNsb3VkIHNlcnZpY2VzIGFyZSBjb25zaWRlcmFibHkgbW9yZSBzZWN1cmUgYW5kIHRydXN0d29ydGh5IHRoYW4gdGhleSB3ZXJlIGV2ZW4gMiB0byAzIHllYXJzIGFnby4gU3VjaCBzZXJ2aWNlcyBsaWtlIERyb3Bib3ggZm9yIEJ1c2luZXNzIG9mZmVyIGVudGVycHJpc2UtbGV2ZWwgY2xvdWQgc3RvcmFnZSAoZm9yIGEgZmVlKSB3aGljaCBhcmUgYnVpbHQgdG8gYWNjb21tb2RhdGUgYnVzaW5lc3NlcyB3aXRoIGEgc2lnbmlmaWNhbnQgYW1vdW50IG9mIGludGVybmFsIGRhdGEuICBIYXZpbmcgeW91ciBvd24gY2xvdWQgaW4gYSBkaWZmZXJlbnQgcGh5c2ljYWwgbG9jYXRpb24gaXMgYWxzbyBhbiBvcHRpb24uIEJ5IGhhdmluZyBhbiBpbnRlcm5hbGx5LWJhc2VkIGNsb3VkLCB5b3UgY2FuIG5vdCBvbmx5IHN0b3JlIHlvdXIgaW5mb3JtYXRpb24gc2VjdXJlbHksIGJ1dCB5b3UgYWxzbyBhdm9pZCBoYXZpbmcgdG8gZGVhbCB3aXRoIGEgM3JkLXBhcnR5IGNsb3VkIHN0b3JhZ2UgcHJvdmlkZXIuDQo8cD5MYXN0IGJ1dCBub3QgbGVhc3QgaXMgdGhlIG1vc3Qgb2J2aW91cyBzZWN1cml0eSBtZWFzdXJlOiB0aGUgdHJhZGl0aW9uYWwgYW50aXZpcnVzIHNvZnR3YXJlLiBNYW55IGNvbXBhbmllcyBwcm92aWRlIHRoaXMgdHlwZSBvZiAgc29mdHdhcmUsIDxhIGhyZWY9Imh0dHBzOi8vYW50aXZpcnVzLmNvbW9kby5jb20vIiB0YXJnZXQ9Il9ibGFuayI+Q29tb2RvPC9hPiwgPGEgaHJlZj0iaHR0cDovL3d3dy5lc2V0LmNvbS8iIHRhcmdldD0iX2JsYW5rIj5FU0VUPC9hPiwgPGEgaHJlZj0iaHR0cHM6Ly93d3cuYXZhc3QuY29tLyIgdGFyZ2V0PSJfYmxhbmsiPkFWQVNUPC9hPiwgPGEgaHJlZj0iaHR0cDovL3d3dy5tY2FmZWUuY29tLyIgdGFyZ2V0PSJfYmxhbmsiPk1jQWZlZTwvYT4sIGFuZCA8YSBocmVmPSJodHRwOi8vd3d3Lmthc3BlcnNreS5jb20vIiB0YXJnZXQ9Il9ibGFuayI+S2FzcGVyc2t5IExhYjwvYT4sIHRvIG5hbWUganVzdCBhIGZldy4gVGhlc2UgY29tcGFuaWVzIHByb3ZpZGUgdmFyaW91cyBzZWN1cml0eSBmZWF0dXJlcyB0byBrZWVwIHlvdSBvbiB0aGUgc2FmZSBzaWRlIGFuZCBoZWxwIGF2b2lkIGNyaXRpY2FsIHNpdHVhdGlvbnMgbGlrZSB0aGUgb25lIHdlIGhhdmUgZGVzY3JpYmVkIGFib3ZlLiBXZSByZWNvbW1lbmQgdmlzaXRpbmcgdGhlc2Ugc2l0ZXMgdG8gZGV0ZXJtaW5lIHdoaWNoIGNvbXBhbnnigJlzIHNvZnR3YXJlIGJlc3QgZml0cyB5b3VyIHNlY3VyaXR5IHJlcXVpcmVtZW50cy48L3A+PHA+VG8gY29uY2x1ZGUsIHRoZSBiZXN0IGFkdmljZSB3ZSBjYW4gb2ZmZXIgdG8ga2VlcCBhbGwgb2YgeW91ciBzaXRlIHNlY3VyaXR5IHJlc291cmNlcyBvcHRpbWl6ZWQgaXMgdG8gY29uc3VsdCB3aXRoIGEgcHJvZmVzc2lvbmFsIHdlYi1zZWN1cml0eSBzcGVjaWFsaXN0IG9uIGhvdyBiZXN0IHRvIHNlY3VyZSB5b3VyIHNpdGUgYW5kIGRhdGEuIFdoaWxlIHRoaXMgbWF5IHByZXNlbnQgc3Vic3RhbnRpYWwgdXAtZnJvbnQgY29zdHMsIGl0IHdpbGwgc2F2ZSB5b3UgdGltZSBhbmQgbW9uZXkgaW4gdGhlIGxvbmcgcnVuLCBwcm92aWRlIHlvdSB3aXRoIHBlYWNlLW9mLW1pbmQsIGFuZCBhbGxvdyB5b3UgdG8gZm9jdXMgb24gdGhlIHVuaXF1ZSBhc3BlY3RzIG9mIHJ1bm5pbmcgYSBzdWNjZXNzZnVsIGJ1c2luZXNzLiA8L3A+","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"2021-05-12T15:08:44.0000000","LiveDateTime":"1754-02-02T00:00:00.0000000","CreatedDateTime":"2016-07-07T09:01:36.0000000","ApprovalDatetime":"2016-07-07T09:19:42.0000000","RequestCount":32261,"MarkedAsNew":false,"MarkedAsFeatured":false,"RatingValue":3,"CategoryPaths":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":1,"CategoryId":14,"CategoryName":"SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":2,"CategoryId":38,"CategoryName":"SSL General"}],"AssociatedCategories":[{"CategoryId":38,"CategoryName":"SSL General","CategoryDisplayName":"SSL CertificatesSSL General"}],"AssociatedTags":[],"RelatedArticles":[],"AssociatedMedias":[],"PreferredCategoryId":0,"RootParentCategoryName":"","RootParentCategoryId":0},"status":200,"statusText":"OK"},"/api/v1/ncpl/simplekb/getcategorybycategoryid:\"{\\\"categoryId\\\":38}\"":{"body":{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryDto","Description":"QmFzaWMgaW5mb3JtYXRpb24gb24gU1NMIGNlcnRpZmljYXRlcw==","ParentCategoryId":14,"Parent_Category_Name":"SSL Certificates","FriendlyId":null,"ApprovedYN":true,"TreatAsTopicYN":false,"CreatedDateTime":"07/25/2008 16:58:37","CurrentCategoryPaths":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":1,"CategoryId":14,"CategoryName":"SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":2,"CategoryId":38,"CategoryName":"SSL General"}],"RelatedCategories":[],"AssociatedArticles":[{"ArticleId":9503,"Title":"What is an ECC (Elliptic Curve Cryptography) certificate?","ArticleName":"What is an ECC (Elliptic Curve Cryptography) certificate?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/23/2019"},{"ArticleId":9504,"Title":"How do I get an ECC certificate via Namecheap?","ArticleName":"How do I get an ECC certificate via Namecheap?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/06/2025"},{"ArticleId":9507,"Title":"Why an EV certificate is better for an ecommerce website than a Domain Validation one?","ArticleName":"Why an EV certificate is better for an ecommerce website than a Domain Validation one?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"07/24/2020"},{"ArticleId":9508,"Title":"What is the difference between very high, high, medium and low assurance certificates?","ArticleName":"What is the difference between very high, high, medium and low assurance certificates?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/15/2024"},{"ArticleId":9509,"Title":"Your site shows 256-bit encryption and my site shows 128-bit, why?","ArticleName":"Your site shows 256-bit encryption and my site shows 128-bit, why?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"08/27/2019"},{"ArticleId":9511,"Title":"How 2–5-year SSL certificates work","ArticleName":"How 2–5-year SSL certificates work","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":"03/14/2015 04:00:00","FeaturedTillDate":"03/09/2015 04:00:00","ModifiedDateTime":"04/15/2024"},{"ArticleId":9588,"Title":"What is Certificate Transparency?","ArticleName":"What is Certificate Transparency?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/06/2025"},{"ArticleId":9595,"Title":"HTTP to HTTPS redirection on IIS","ArticleName":"HTTP to HTTPS redirection on IIS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/25/2019"},{"ArticleId":9596,"Title":"HTTP Strict Transport Security (HSTS)","ArticleName":"HTTP Strict Transport Security (HSTS)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9597,"Title":"HTTP Public Key Pinning (HPKP)","ArticleName":"HTTP Public Key Pinning (HPKP)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/06/2024"},{"ArticleId":9598,"Title":"Disabling SSLv3","ArticleName":"Disabling SSLv3","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9599,"Title":"Disabling RC4","ArticleName":"Disabling RC4","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9600,"Title":"Disabling SHA-1","ArticleName":"Disabling SHA-1","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9601,"Title":"Cipher Suites Configuration and forcing Perfect Forward Secrecy on Windows","ArticleName":"Cipher Suites Configuration and forcing Perfect Forward Secrecy on Windows","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":9602,"Title":"OCSP Stapling","ArticleName":"OCSP Stapling","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9650,"Title":"I can see SHA-1 fingerprint/thumbprint on my certificate. Is my certificate actually SHA-2?","ArticleName":"I can see SHA-1 fingerprint/thumbprint on my certificate. Is my certificate actually SHA-2?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/23/2019"},{"ArticleId":9652,"Title":"Perfect Forward Secrecy. What it is?","ArticleName":"Perfect Forward Secrecy. What it is?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2022"},{"ArticleId":9653,"Title":"How to check whether the server supports Forward Secrecy","ArticleName":"How to check whether the server supports Forward Secrecy","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"06/22/2023"},{"ArticleId":9682,"Title":"How to push SSL certificates from one Namecheap account to another one","ArticleName":"How to push SSL certificates from one Namecheap account to another one","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/06/2025"},{"ArticleId":9707,"Title":"HSTS: General information","ArticleName":"HSTS: General information","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9708,"Title":"Prerequisites for Namecheap Shared hosting to enable HSTS","ArticleName":"Prerequisites for Namecheap Shared hosting to enable HSTS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9709,"Title":"How to enable HSTS on Namecheap shared hosts","ArticleName":"How to enable HSTS on Namecheap shared hosts","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/10/2023"},{"ArticleId":9710,"Title":"How to enable HSTS on third-party servers","ArticleName":"How to enable HSTS on third-party servers","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9711,"Title":"How to check if HSTS is enabled","ArticleName":"How to check if HSTS is enabled","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9727,"Title":"What is SSL certificate encryption strength?","ArticleName":"What is SSL certificate encryption strength?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9752,"Title":"How do I get A+ rating in SSLLabs?","ArticleName":"How do I get A+ rating in SSLLabs?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9770,"Title":"How to use .htaccess to redirect to https in cPanel","ArticleName":"How to use .htaccess to redirect to https in cPanel","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/10/2023"},{"ArticleId":9782,"Title":"Security tips for business","ArticleName":"Security tips for business","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/12/2021"},{"ArticleId":9783,"Title":"1024 bit certificates","ArticleName":"1024 bit certificates","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/13/2022"},{"ArticleId":9800,"Title":"Advantages of having an SSL certificate","ArticleName":"Advantages of having an SSL certificate","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2023"},{"ArticleId":9805,"Title":"Setting HTTPS redirect on a Nginx web-server","ArticleName":"Setting HTTPS redirect on a Nginx web-server","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9821,"Title":"Apache Redirect to HTTPS","ArticleName":"Apache Redirect to HTTPS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"06/19/2020"},{"ArticleId":9952,"Title":"Supported key sizes and signature algorithms in CSRs","ArticleName":"Supported key sizes and signature algorithms in CSRs","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"12/05/2017 05:00:00","ModifiedDateTime":"07/27/2023"},{"ArticleId":9953,"Title":"IIS Redirect HTTP to HTTPS","ArticleName":"IIS Redirect HTTP to HTTPS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"11/28/2017 05:00:00","ModifiedDateTime":"12/06/2022"},{"ArticleId":9968,"Title":"How to check the certificate revocation status","ArticleName":"How to check the certificate revocation status","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"01/26/2018 05:00:00","ModifiedDateTime":"09/24/2019"},{"ArticleId":9969,"Title":"HPKP pinning","ArticleName":"HPKP pinning","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/06/2024"},{"ArticleId":9991,"Title":"CAA Record and why it is needed (SSL related)","ArticleName":"CAA Record and why it is needed (SSL related)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"04/30/2018 04:00:00","ModifiedDateTime":"09/07/2022"},{"ArticleId":10081,"Title":"Comodo CA rebrands as Sectigo","ArticleName":"Comodo CA rebrands as Sectigo","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"01/25/2019"},{"ArticleId":10100,"Title":"Cipher Suites Configuration for Apache, Nginx","ArticleName":"Cipher Suites Configuration for Apache, Nginx","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2022"},{"ArticleId":10503,"Title":"How to remove an SSL from a Namecheap account","ArticleName":"How to remove an SSL from a Namecheap account","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/11/2025"},{"ArticleId":10504,"Title":"What is AutoSSL and how to use it?","ArticleName":"What is AutoSSL and how to use it?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/18/2025"},{"ArticleId":10557,"Title":"Decoder.link user guide","ArticleName":"Decoder.link user guide","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/15/2025"},{"ArticleId":10595,"Title":"Understanding How SSL Encryption Works","ArticleName":"Understanding How SSL Encryption Works","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"04/05/2023"},{"ArticleId":10597,"Title":"What is SSL and TLS","ArticleName":"What is SSL and TLS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2023"},{"ArticleId":10747,"Title":"What is MPIC (Multi-Perspective Issuance Corroboration)","ArticleName":"What is MPIC (Multi-Perspective Issuance Corroboration)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/15/2025"},{"ArticleId":9293,"Title":"I need to secure some of the subdomains of my domain name","ArticleName":"I need to secure some of the subdomains of my domain name","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9294,"Title":"I need to secure two, three or more domain names with the same certificate","ArticleName":"I need to secure two, three or more domain names with the same certificate","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":9464,"Title":"Can I download an issued certificate on your site?","ArticleName":"Can I download an issued certificate on your site?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/12/2024"},{"ArticleId":786,"Title":"What is an SSL certificate and what is it used for?","ArticleName":"What is an SSL certificate and what is it used for?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"07/24/2023"},{"ArticleId":334,"Title":"What is Certificate Authority (CA)?","ArticleName":"What is Certificate Authority (CA)?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9415,"Title":"SSL certificate migration from the SHA-1 to SHA-2 algorithm","ArticleName":"SSL certificate migration from the SHA-1 to SHA-2 algorithm","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9467,"Title":"How do I check my hashing algorithm?","ArticleName":"How do I check my hashing algorithm?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9484,"Title":"I want to test your service do you have trial certificates?","ArticleName":"I want to test your service do you have trial certificates?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"04/28/2025"},{"ArticleId":789,"Title":"Can I use a single SSL certificate for multiple subdomains?","ArticleName":"Can I use a single SSL certificate for multiple subdomains?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":787,"Title":"How to inform your clients that you use SSL","ArticleName":"How to inform your clients that you use SSL","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2023"},{"ArticleId":464,"Title":"What is a wildcard certificate?","ArticleName":"What is a wildcard certificate?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/07/2024"},{"ArticleId":790,"Title":"Types of certificates offered at Namecheap","ArticleName":"Types of certificates offered at Namecheap","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/01/2019"},{"ArticleId":9469,"Title":"Are your certificates private or shared? What is the difference?","ArticleName":"Are your certificates private or shared? What is the difference?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/26/2015"},{"ArticleId":9466,"Title":"Can I get a certificate if I use an online web-hosting (Wix, Weebly, Tumblr, etc.)?","ArticleName":"Can I get a certificate if I use an online web-hosting (Wix, Weebly, Tumblr, etc.)?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"01/20/2021"},{"ArticleId":9473,"Title":"Can I use your SSL certificates for FTP and SQL?","ArticleName":"Can I use your SSL certificates for FTP and SQL?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/22/2018"},{"ArticleId":9481,"Title":"I have a certificate at another vendor; will there be an issue, if I activate one with you for the same common name?","ArticleName":"I have a certificate at another vendor; will there be an issue, if I activate one with you for the same common name?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/26/2015"},{"ArticleId":982,"Title":"Domain Validated certificates","ArticleName":"Domain Validated certificates","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":886,"Title":"Chained and single Root certificates","ArticleName":"Chained and single Root certificates","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":885,"Title":"SSL certificate warranty","ArticleName":"SSL certificate warranty","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"}],"AssociatedTags":[],"CategoryId":38,"CategoryName":"SSL General"},"status":200,"statusText":"OK"},"/api/v1/ncpl/simplekb/getcategories:\"{\\\"parentCategoryId\\\":0,\\\"getTree\\\":true}\"":{"body":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2216,"CategoryName":"Spam Protection"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2217,"CategoryName":"Renewal"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2218,"CategoryName":"cPanel SSL Plugin"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2219,"CategoryName":"PHP Configuration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2221,"CategoryName":"Multi-Domain SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2222,"CategoryName":"Cancellation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2223,"CategoryName":"Browser errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2224,"CategoryName":"Site Seal, Logo"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2225,"CategoryName":"SEO"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2226,"CategoryName":"Email Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2227,"CategoryName":"SSL Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/cloud-red.png","ShortDesc":"","CategoryId":2228,"CategoryName":"Apps","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2251,"CategoryName":"Supersonic CDN"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2298,"CategoryName":"Site Maker"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":177,"CategoryName":"Google Workspace (formerly G Suite)"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2229,"CategoryName":"Hosting Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2232,"CategoryName":"DNSSEC"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2234,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2237,"CategoryName":"Host records setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2238,"CategoryName":"SSL installation errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/easywp-red.png","ShortDesc":"","CategoryId":2239,"CategoryName":"EasyWP","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2280,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2279,"CategoryName":"General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2281,"CategoryName":"WordPress Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2282,"CategoryName":"Plugins and Themes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2284,"CategoryName":"WordPress Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2285,"CategoryName":"SFTP and Database access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2286,"CategoryName":"Domains questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2288,"CategoryName":"Billing questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2287,"CategoryName":"SSL questions"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2251,"CategoryName":"Supersonic CDN"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2252,"CategoryName":"InterWorx questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2254,"CategoryName":"Domains How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2255,"CategoryName":"Hosting How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2257,"CategoryName":"Sales & Payments How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2258,"CategoryName":"cPanel Email How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2260,"CategoryName":"Private Email Contacts and Calendars Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2262,"CategoryName":"EasyWP How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"https://download.namecheap.com/assets/img/domainvault-red@2x.png","ShortDesc":"","CategoryId":2289,"CategoryName":"Domain Vault","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2290,"CategoryName":"CSR code"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2291,"CategoryName":"Webuzo questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2292,"CategoryName":"Browser Extensions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2293,"CategoryName":"Automated SSL management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2298,"CategoryName":"Site Maker"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":27,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/support-red.png","ShortDesc":"","CategoryId":5,"CategoryName":"General & Support","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":7,"CategoryName":"Billing FAQ"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":8,"CategoryName":"Transfer Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":22,"CategoryName":"Hosting Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":38,"CategoryName":"SSL General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":45,"CategoryName":"Account Security"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":46,"CategoryName":"Domain Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":63,"CategoryName":"Namecheap API"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":177,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2179,"CategoryName":"Private Email: General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2274,"CategoryName":"General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2280,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2279,"CategoryName":"General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2215,"CategoryName":"Private Email: Mailbox Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2196,"CategoryName":"WHMCS module for SSL"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/savings-red.png","ShortDesc":"","CategoryId":2200,"CategoryName":"Checkout & Billing","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":7,"CategoryName":"Billing FAQ"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2201,"CategoryName":"Domains Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":21,"CategoryName":"Hosting Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":71,"CategoryName":"SSL Certificates Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2177,"CategoryName":"Private Email"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2201,"CategoryName":"Domains Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":67,"CategoryName":"Activation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":83,"CategoryName":"Transfer to Namecheap"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":43,"CategoryName":"Profile Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":10,"CategoryName":"DNS Questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":29,"CategoryName":"cPanel questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":21,"CategoryName":"Hosting Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":11,"CategoryName":"Dynamic DNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":44,"CategoryName":"Account Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":84,"CategoryName":"Transfer to another provider"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":68,"CategoryName":"Validation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2182,"CategoryName":"cPanel: Software Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2214,"CategoryName":"Email Forwarding"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2270,"CategoryName":"Routers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2281,"CategoryName":"WordPress Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2282,"CategoryName":"Plugins and Themes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2272,"CategoryName":"TV"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2187,"CategoryName":"cPanel: WordPress"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":219,"CategoryName":"Canceled Transfers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":71,"CategoryName":"SSL Certificates Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2176,"CategoryName":"Private Email: DNS Settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":69,"CategoryName":"Installation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/reseller-red.png","ShortDesc":"","CategoryId":34,"CategoryName":"Domains","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2232,"CategoryName":"DNSSEC"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2234,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2237,"CategoryName":"Host records setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":46,"CategoryName":"Domain Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":10,"CategoryName":"DNS Questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":11,"CategoryName":"Dynamic DNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":35,"CategoryName":"Registrations"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2207,"CategoryName":"Renewal questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":36,"CategoryName":"Domains with extended attributes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":51,"CategoryName":"FreeDNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":15,"CategoryName":"Namecheap Market"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2208,"CategoryName":"3rd Party Services Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2278,"CategoryName":"Handshake TLDs"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":35,"CategoryName":"Registrations"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":70,"CategoryName":"Reissuance"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/protection-red.png","ShortDesc":"","CategoryId":37,"CategoryName":"Domain Privacy Protection","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2177,"CategoryName":"Private Email"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2178,"CategoryName":"Private Email: Webmail Features"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2207,"CategoryName":"Renewal questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2210,"CategoryName":"cPanel Add-ons"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2273,"CategoryName":"Gaming Consoles"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2284,"CategoryName":"WordPress Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2285,"CategoryName":"SFTP and Database access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2268,"CategoryName":"macOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2175,"CategoryName":"Private Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/status-red.png","ShortDesc":"","CategoryId":2209,"CategoryName":"Domain Transfers","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":8,"CategoryName":"Transfer Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":83,"CategoryName":"Transfer to Namecheap"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":84,"CategoryName":"Transfer to another provider"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":219,"CategoryName":"Canceled Transfers"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":48,"CategoryName":"VPS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":36,"CategoryName":"Domains with extended attributes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/server-red.png","ShortDesc":"","CategoryId":12,"CategoryName":"Hosting","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2219,"CategoryName":"PHP Configuration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2225,"CategoryName":"SEO"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2252,"CategoryName":"InterWorx questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2291,"CategoryName":"Webuzo questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":27,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":22,"CategoryName":"Hosting Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":29,"CategoryName":"cPanel questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2182,"CategoryName":"cPanel: Software Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2187,"CategoryName":"cPanel: WordPress"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2210,"CategoryName":"cPanel Add-ons"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":48,"CategoryName":"VPS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2188,"CategoryName":"Dedicated Server"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":30,"CategoryName":"WHM questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":32,"CategoryName":"DNS settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":103,"CategoryName":"LVE (CloudLinux)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":89,"CategoryName":"SSH Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":205,"CategoryName":"FTP questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2180,"CategoryName":"MySQL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2199,"CategoryName":"Hosting Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2194,"CategoryName":"Tips & Tricks"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":239,"CategoryName":"WHMCS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":33,"CategoryName":"SSL Installation"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2171,"CategoryName":"Private Email: Active Sync (Exchange) Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2188,"CategoryName":"Dedicated Server"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2269,"CategoryName":"iOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2286,"CategoryName":"Domains questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2288,"CategoryName":"Billing questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2271,"CategoryName":"Linux"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":30,"CategoryName":"WHM questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":31,"CategoryName":"cPanel Email FAQs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":51,"CategoryName":"FreeDNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/email-red.png","ShortDesc":"","CategoryId":93,"CategoryName":"Email service","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2216,"CategoryName":"Spam Protection"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2226,"CategoryName":"Email Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2260,"CategoryName":"Private Email Contacts and Calendars Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2179,"CategoryName":"Private Email: General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2215,"CategoryName":"Private Email: Mailbox Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2214,"CategoryName":"Email Forwarding"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2176,"CategoryName":"Private Email: DNS Settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2178,"CategoryName":"Private Email: Webmail Features"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2175,"CategoryName":"Private Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2171,"CategoryName":"Private Email: Active Sync (Exchange) Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":31,"CategoryName":"cPanel Email FAQs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2186,"CategoryName":"cPanel Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2204,"CategoryName":"Private Email: Video Overview"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":32,"CategoryName":"DNS settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":15,"CategoryName":"Namecheap Market"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2186,"CategoryName":"cPanel Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2266,"CategoryName":"Windows"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2287,"CategoryName":"SSL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2267,"CategoryName":"Android"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2208,"CategoryName":"3rd Party Services Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2204,"CategoryName":"Private Email: Video Overview"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/security-red.png","ShortDesc":"","CategoryId":14,"CategoryName":"SSL Certificates","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2217,"CategoryName":"Renewal"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2218,"CategoryName":"cPanel SSL Plugin"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2221,"CategoryName":"Multi-Domain SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2222,"CategoryName":"Cancellation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2223,"CategoryName":"Browser errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2224,"CategoryName":"Site Seal, Logo"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2238,"CategoryName":"SSL installation errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2290,"CategoryName":"CSR code"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2293,"CategoryName":"Automated SSL management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":38,"CategoryName":"SSL General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":67,"CategoryName":"Activation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":68,"CategoryName":"Validation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":69,"CategoryName":"Installation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":70,"CategoryName":"Reissuance"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/performance-red.png","ShortDesc":"","CategoryId":9,"CategoryName":"My Account","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":45,"CategoryName":"Account Security"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":43,"CategoryName":"Profile Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":44,"CategoryName":"Account Access"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2278,"CategoryName":"Handshake TLDs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":103,"CategoryName":"LVE (CloudLinux)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/affiliates-red.png","ShortDesc":"","CategoryId":55,"CategoryName":"Affiliates","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":89,"CategoryName":"SSH Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/tools-red.png","ShortDesc":"","CategoryId":2211,"CategoryName":"API & Resellers","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2227,"CategoryName":"SSL Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2229,"CategoryName":"Hosting Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":63,"CategoryName":"Namecheap API"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2196,"CategoryName":"WHMCS module for SSL"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/timer-red.png","ShortDesc":"","CategoryId":2212,"CategoryName":"Legacy Products","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":205,"CategoryName":"FTP questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2180,"CategoryName":"MySQL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2199,"CategoryName":"Hosting Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/premiumdns-red.png","ShortDesc":"","CategoryId":2231,"CategoryName":"PremiumDNS","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2194,"CategoryName":"Tips & Tricks"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"https://static.nc-img.com/live-resource/icons/knowledgebase/fastVPN_icon-150px.png","ShortDesc":"","CategoryId":2265,"CategoryName":"FastVPN","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2292,"CategoryName":"Browser Extensions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2274,"CategoryName":"General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2270,"CategoryName":"Routers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2272,"CategoryName":"TV"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2273,"CategoryName":"Gaming Consoles"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2268,"CategoryName":"macOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2269,"CategoryName":"iOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2271,"CategoryName":"Linux"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2266,"CategoryName":"Windows"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2267,"CategoryName":"Android"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":239,"CategoryName":"WHMCS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":33,"CategoryName":"SSL Installation"}],"status":200,"statusText":"OK"}}If you have just started a business, you’re probably already aware of the impact the Internet has had on all facets of our economy and culture today. You also know how essential it is for a new company to have a strong web presence.
Another security measure is Two Factor Authentication or 2FA. This step helps keep your accounts with different services safe from trespassers who might try using your credentials on multiple sites. 2FA adds an additional layer of security by requiring access to the phone number associated with the account. You can enable 2FA in your Namecheap account by following this guide.
It’s a good idea to use password managers such as LastPass, Dashlane, Roboform and KeePass to securely store and manage your passwords. These programs can also auto-generate strong passwords that meet the above-mentioned requirements.
Since your website uses various software for hosting and management, be sure to keep it updated with the latest software updates, since, with each update, the company fixes reported errors and bugs, and minimizes vulnerabilities.
Despite having updated software, however, there’s still plenty of malware that can infect your website without you being aware. For example, sites that spread malware can implement malicious code on your website to redirect visitors somewhere else. Always schedule regular monthly or weekly security checks to be on the safe side.
Email is an essential part of every business that ought to be protected as well. It is possible to not only secure the connection to your mail server, but also to sign your emails with security certificates, known as S/MIME certificates.
Generally, secure mail ports are used to connect to the mail server, such as 995 (instead of standard 100 for POP3), 993 (instead of 143 for IMAP), and 465 (instead of 25 for SMTP). You may set a secure connection to a Namecheap Private email service using this guide.
We’d also like to take a moment to describe how phishing attacks work, so that you can secure yourself from them as well. Let’s say, for example, you receive an email that claims to be from “Your trusted bank”, and indeed, appears to be from the actual bank where you keep your money. The email may ask you, for example, to visit a link and provide certain critical account information. The email may also claim that they simply need to “confirm” this data, or they may warn that your account may be closed or that you may incur fees if you do not take immediate action. . Regardless of the request, it is important to remember that banks and other credible financial organizations will never ask for personal information via email. You should never share any personal information via links provided in these types of emails... If you click the link, make sure it brings you to the same location it claims to point to. As an example of this, look at the two links below: https://www.namecheap.com and https://www.namecheap.com.
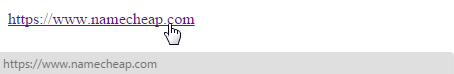
Bad link

In order to encrypt and secure the traffic between your website and visitors be , we recommend implementing an SSL certificate on your site.
SSL (which stands for Secure Sockets Layer) certificates come in various levels of security to fit the specific needs of your site. . We will briefly take a look at each of these certificates and will describe them in terms of how the validation of the domain name is arranged.
The most basic type of certificate is domain validation (DV. A DV certificate will show who owns the domain name and will provide encryption of site traffic.
To show your customers your domain ownership information as well as validation that your company is officially owned and registered by you, we recommend an organization validation (OV)certificate. OV certs display your company name and address in the certificate details. Additionally, they require you to pass a company verification process with the Certificate Authority (CA) that issues the certificate. This may include requirements such as having your organization listed in a business credit listing like Dun & Bradstreet, or a public database like YellowPages.com. Be sure your business can be validated through channels such as these before choosing an OV certificate.
Extended validation (EV) certificates are a great option for top-tier security. Like OV certificates, EV certs require your company to be incorporated, verified with the issuing CA, maintain a corporate phone number listed in a directory of your country, and be registered in a business credit listing such as Dun & Bradstreet. The verification is more thorough, and the explicit company details will be reflected on the certificate details panel in the browser and on the site seal. We recommend choosing an EV cert only if your business is able to accommodate this rigorous validation process and you require the highest certificate assurance level.
Domains, hosting services, SSL certificates, software, and other services require having a managed account with one or more providers. If your business has only one person managing your account(s), it’s advisable to have a plan for when and if that person is suddenly unavailable.
Let’s assume your company has 30 employees, all of which are pretty familiar with the company’s policy regarding downloads from the internet. Your company manages 1000 payment transactions every day, meaning you’re storing tons of credit card and other personal customer information in your internal database. Let’s also assume you’ve implemented all the security measures recommended in this article up to this point. So, the day comes when one of your employees accidentally downloads an attachment in one of those “You have won a $10.000 lottery!” emails. The email contains a worm that immediately runs and clones itself all over your entire company network, stealing your customers’ personal data and sending it to the worm creator. At this point, all you can do is switch off your office internet to ensure the information does not go further than your internal network, and this is assuming you somehow find out how the virus actually works. Such a worm can also simply delete all the information on all your computers, taking you back to square one. As you can probably tell at this point in our example, this is not even the worst-case scenario.
Last but not least is the most obvious security measure: the traditional antivirus software. Many companies provide this type of software, Comodo, ESET, AVAST, McAfee, and Kaspersky Lab, to name just a few. These companies provide various security features to keep you on the safe side and help avoid critical situations like the one we have described above. We recommend visiting these sites to determine which company’s software best fits your security requirements.
To conclude, the best advice we can offer to keep all of your site security resources optimized is to consult with a professional web-security specialist on how best to secure your site and data. While this may present substantial up-front costs, it will save you time and money in the long run, provide you with peace-of-mind, and allow you to focus on the unique aspects of running a successful business.
Need help? We're always here for you.