| Subtotal | $0.00 |
| Subtotal | $0.00 |
When we finally managed to customize the correct HSTS header field and the results are saved, the HSTS Policy is considered to be enabled for a given host. Basically, a website performance is not affected by HSTS implementation, and a common user will not notice an obvious difference as if a particular website is using HSTS or not.
Consequently, a logical question arises whether there is a possibility to check if the HSTS Policy is indeed enabled. There are a few ways to do that: using command prompt via SSH or with the help of online checkers.
Checking HSTS status using Qualys SSL Labs
There is a plenty of online tools that allow to check server configuration in terms of security – from a basic SSL certificate installation check to a deep verification of all aspects related to secure transport implementation. One of the tools, which provide a wide set of parameters to check, is Qualys SSL Labs. Besides the overall score, which is calculated based on a variety of indexes, we need to scroll the result page, once the analysis is completed, down to Protocol Details subsection and locate Strict Transport Security (HSTS) item in front of which there would be the actual result of checking against HSTS.
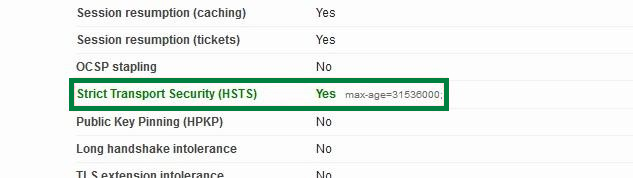
Checking HSTS header via SSH client using cURL
An SSH client (e.g. PuTTY) gives an opportunity to check any domain name by establishing whether its server returns the STS header in a response to the command, which has been designed in a practical way specifically for this purpose:
curl -s -D- https://example.com/ | grep -i Strict
The response message can be viewed on the screenshot below.
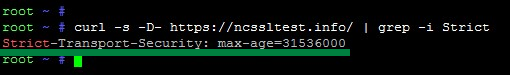
Hence, if HSTS is enabled, there will be an STS header with the “max-age” directive value. In an opposite case, there would be no message from the server, since there is nothing to send in response to the above stated command.
Need help? We're always here for you.