{"/api/v1/ncpl/simplekb/getarticle:\"{\\\"articleId\\\":10123,\\\"categoryId\\\":89}\"":{"body":{"Id":10123,"FriendlyId":"","ArticleTypeId":0,"Title":"Using CXS scan via SSH","ArticleName":"Using CXS scan via SSH","ArticleSummary":null,"PreponedSummary":false,"Approved":true,"Body":"DQoJCTxkaXY+DQoJCQkJPGI+Q29uZmlnU2VydmVyIEV4cGxvaXQgU2Nhbm5lciAoQ1hTKTwvYj4gaXMgYSBzZXJ2ZXIgYW50aXZpcnVzIHN5c3RlbSB0aGF0IGNhbiBiZSBwdXJjaGFzZWQgYW5kIGluc3RhbGxlZCBvbiBWUFMgYW5kIERlZGljYXRlZCBTZXJ2ZXJzIHRvIGRldGVjdCBhbmQgbWl0aWdhdGUgdmFyaW91cyB0eXBlcyBvZiBtYWx3YXJlLiBUaGlzIGlzIGRvbmUgYnkgY3hzd2F0Y2ggZGFlbW9uIGZvciBhbGwgZmlsZXMgdXBsb2FkZWQgdG8gdGhlIHJlc3BlY3RpdmUgc2VydmVyLCBidXQgeW91IGNhbiBhbHNvIHVzZSBpdCB0byBhY3RpdmVseSBzY2FuIGZpbGVzIGluIHJlYWwgdGltZS4gPGJyIC8+PC9kaXY+DQoJCTxkaXY+DQoJCQkJPGJyIC8+DQoJCTwvZGl2Pg0KCQk8dWw+DQoJCQkJPGxpPg0KCQkJCQkJPGEgaHJlZj0iI2ltcG9ydGFudCI+SW1wb3J0YW50IGxvY2F0aW9ucyBhbmQgY29uZmlndXJhdGlvbnM8L2E+DQoJCQkJPC9saT4NCgkJCQk8bGk+DQoJCQkJCQk8YSBocmVmPSIjc3NoX29uZV9saW5lIj5DWFMgU1NIIG9uZS1saW5lIGNvbW1hbmRzPC9hPg0KCQkJCTwvbGk+DQoJCQkJPGxpPg0KCQkJCQkJPGEgaHJlZj0iI3NjYW5uaW5nIj5TY2FubmluZyB0aGUgd2hvbGUgc2VydmVyPC9hPg0KCQkJCTwvbGk+DQoJCQkJPHVsPg0KCQkJCQkJPGxpPg0KCQkJCQkJCQk8YSBocmVmPSIjc3RvcmluZ19yZXBvcnRzIj5TdG9yaW5nIHNjYW4gcmVwb3J0cyBpbiB0aGUgZGF0YWJhc2U8L2E+DQoJCQkJCQk8L2xpPg0KCQkJCTwvdWw+DQoJCQkJPGxpPg0KCQkJCQkJPGEgaHJlZj0iI3dvcmtpbmciPldvcmtpbmcgd2l0aCBxdWFyYW50aW5lZCBmaWxlcyBhbmQgZmFsc2UtcG9zaXRpdmUgcmVzdWx0czwvYT4NCgkJCQk8L2xpPg0KCQkJCTx1bD4NCgkJCQkJCTxsaT4NCgkJCQkJCQkJPGEgaHJlZj0iI3ZpZXdpbmciPlZpZXdpbmcgcXVhcmFudGluZWQgZmlsZXM8L2E+DQoJCQkJCQk8L2xpPg0KCQkJCQkJPGxpPg0KCQkJCQkJCQk8YSBocmVmPSIjY29uc2lkZXJpbmciPkNvbnNpZGVyaW5nIHdoZXRoZXIgb3Igbm90IHRoZSBmaWxlIGlzIGRhbmdlcm91czwvYT4NCgkJCQkJCTwvbGk+DQoJCQkJCQk8bGk+DQoJCQkJCQkJCTxhIGhyZWY9IiNyZXN0b3JhdGlvbiI+RmlsZSByZXN0b3JhdGlvbiBhbmQgd2hpdGVsaXN0IG1hbmFnZW1lbnQ8L2E+DQoJCQkJCQk8L2xpPg0KCQkJCTwvdWw+DQoJCTwvdWw+DQoJCTxiciAvPg0KCQk8YnIgLz5XaGlsZSByZWFkaW5nIHRoaXMgZ3VpZGUsIHBsZWFzZSBrZWVwIGluIG1pbmQgdGhlIGZvbGxvd2luZzo8YnIgLz48YnIgLz48dWw+PGxpPkNYUyBpcyBkZXNpZ25lZCBhcyBhIGNvbW1hbmQtbGluZSB1dGlsaXR5LiBNb3N0IG9mIGl0cyBmdW5jdGlvbmFsaXR5IGlzIGF2YWlsYWJsZSB2aWEgdGhlIFdITSBwbHVnaW4sIGJ1dCB3ZSB3aWxsIGtlZXAgdGhlIGZvY3VzIG9ubHkgb24gdGhlIENvbW1hbmQgTGluZSBJbnRlcmZhY2UgKENMSSkgdXNhZ2UuIDwvbGk+PGxpPkFsbCB0ZXh0IHRoYXQgYXBwZWFycyBpbiA8Yj5ib2xkIDwvYj5zaG91bGQgYmUgcmVwbGFjZWQgd2l0aCB5b3VyIG93biBkYXRhLjwvbGk+PGxpPlRoZSBwdXJwb3NlIG9mIENYUyBpcyB0byBzdG9wIHVucHJpdmlsZWdlZCB1c2VyLWxldmVsIHRocmVhdHMgYW5kIHZpcnVzZXMuIEl0IGlzIG5vdCBhIHJvb3RraXQgc2Nhbm5lciBhbmQgaXQgd2lsbCBub3QgZGV0ZWN0IG9yIGNvbWJhdCBtYWx3YXJlIHRoYXQgd2FzIGFibGUgdG8gZ2FpbiByb290IGFjY2VzcyB0byB0aGUgc3lzdGVtLiA8L2xpPjxsaT5TY2FubmluZyBzeXN0ZW0gZm9sZGVycywgYmV5b25kIHlvdXIgaG9tZSBmb2xkZXIsIGlzIG5vdCByZWNvbW1lbmRlZCBhcyBpdCBjYW4gcmVzdWx0IGluIGZhbHNlLXBvc2l0aXZlIHJlc3VsdHMuIERvaW5nIHNvIHdpdGggb3B0aW9ucyBsaWtlIDxpPjxiPi0tcXVhcmFudGluZTwvYj48L2k+IG1heSBwdXQgdGhlIHN5c3RlbSBpbnRvIGFuIHVucmVjb3ZlcmFibGUgc3RhdGUuPC9saT48bGk+VGhlIGNvbnN0YW50bHktZXZvbHZpbmcgbmF0dXJlIG9mIG1hbHdhcmUgbWFrZXMgaXQgaW1wb3NzaWJsZSB0byBnaXZlIHNwZWNpZmljIHN0ZXBzIG9uIGhvdyB0byBldmFsdWF0ZSB3aGV0aGVyIG9yIG5vdCBhIGZpbGUgaXMgbWFsaWNpb3VzLiBCZWZvcmUgbWFraW5nIGFueSBmaW5hbCBqdWRnZW1lbnRzLCBtYWtlIHN1cmUgdG8gZG8gYWxsIHRoZSBuZWNlc3NhcnkgcmVzZWFyY2ggb24geW91ciBvd24uIDwvbGk+PC91bD48ZGl2PjxiciAvPjwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PHA+PGEgbmFtZT0iaW1wb3J0YW50Ij48Yj5JbXBvcnRhbnQgbG9jYXRpb25zIGFuZCBjb25maWd1cmF0aW9uczwvYj48L2E+PC9wPjxiciAvPjxkaXY+Q29uZmlndXJlZCBhbmQgcXVhcmFudGluZWQgZmlsZXMgYXJlIHN0b3JlZCBpbiB0aGUgc3BlY2lmaWVkIGxvY2F0aW9ucyBiZWxvdzo8L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxzdHlsZSB0eXBlPSJ0ZXh0L2NzcyI+PCFbQ0RBVEFbDQp0YWJsZSB7Ym9yZGVyOiAxcHggc29saWQgYmxhY2s7fQ0KXV0+PC9zdHlsZT48dGFibGU+PHRib2R5Pjx0cj48dGg+TG9jYXRpb248L3RoPjx0aD5FeHBsYW5hdGlvbjwvdGg+PC90cj48dHI+PHRkPjxpPi9ldGMvY3hzPC9pPjwvdGQ+PHRkPk1haW4gZGlyZWN0b3J5OyBtb3N0IGZpbGVzIHRvIHdvcmsgd2l0aCBhcmUgbG9jYXRlZCBoZXJlLg0KPC90ZD48L3RyPjx0cj48dGQ+PGk+DQovZXRjL2N4cy9jeHMuZnANCjwvaT48L3RkPjx0ZD4NCkZpbmdlcnByaW50IGRhdGFiYXNlLg0KPC90ZD48L3RyPjx0cj48dGQ+PGk+DQovZXRjL2N4cy9jeHMuZGINCjwvaT48L3RkPjx0ZD4NClJlcG9ydCBhbmQgY291bnRlciBzdG9yYWdlLg0KPC90ZD48L3RyPjx0cj48dGQ+PGk+DQovZXRjL2N4cy9kZWZhdWx0DQo8L2k+PC90ZD48dGQ+DQpFeGFtcGxlcyBvZiBjb25maWd1cmF0aW9uIGZpbGVzL2Nyb25zLg0KPC90ZD48L3RyPjx0cj48dGQ+PGk+DQovZXRjL2N4cy9jeHMuaWdub3JlKg0KPC9pPjwvdGQ+PHRkPg0KSWdub3JlIGxpc3RzIGZvciBkaWZmZXJlbnQgdHlwZXMgb2Ygc2NhbnMuDQo8L3RkPjwvdHI+PHRyPjx0ZD48aT4vZXRjL2N4cy9jeHNjZ2kuc2g8L2k+PGJyIC8+PGk+L2V0Yy9jeHMvY3hzZGFpbHkuc2g8L2k+PGJyIC8+PGk+L2V0Yy9jeHMvY3hzZnRwLnNoPC9pPjxiciAvPjwvdGQ+PHRkPlNldHMgb2Ygb3B0aW9ucyB1c2VkIGZvciBjb3JyZXNwb25kaW5nIHNjYW5zLg0KPC90ZD48L3RyPjx0cj48dGQ+PGk+DQovb3B0L2N4cy9xdWFyYW50aW5lDQo8L2k+PC90ZD48dGQ+DQpDWFMgcXVhcmFudGluZS4NCjwvdGQ+PC90cj48dHI+PHRkPjxpPg0KL3Zhci9sb2cvY3hzd2F0Y2gubG9nDQo8L2k+PC90ZD48dGQ+DQpNYWluIGxvZyBvZiB0aGUgPGk+Y3hzd2F0Y2ggPC9pPnN5c3RlbSBkYWVtb24uDQo8L3RkPjwvdHI+PHRyPjx0ZD4vZXRjL2N4cy9jeHN3YXRjaC5zaDxiciAvPjxiciAvPjwvdGQ+PHRkPkZpbGUgbGF1bmNoZWQgYnkgY3hzd2F0Y2ggZGFlbW9uLiBXaXRoIG9wdGlvbnMgcHJvdmlkZWQgaW4gaXQgQ1hTIHJ1bnMgaW4gbW9kZSB0aGF0IHNjYW5zIGZpbGVzIHVwbG9hZGVkIHRvIHRoZSBzZXJ2ZXIuPGJyIC8+SWYgeW91IHN1cHBseSAtLW1haWwgb3B0aW9uIGhlcmUsIGl0IHdpbGwgc2VuZCByZXBvcnRzIG9mIGFsbCBjeHN3YXRjaCBzY2FucyB0byB0aGF0IG1haWxib3guPGJyIC8+PGJyIC8+PC90ZD48L3RyPjwvdGJvZHk+PC90YWJsZT48ZGl2PjxiciAvPjwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PGRpdj48cD48YSBuYW1lPSJzc2hfb25lX2xpbmUiPjxiPkNYUyBTU0ggb25lLWxpbmUgY29tbWFuZHM8L2I+PC9hPjwvcD48YnIgLz5PbmUtbGluZSBjb21tYW5kcyBiZWxvdyBjYW4gYmUgdXNlZCB0byBzY2FuIHNpbmdsZSBsb2NhdGlvbnMgb3IgaG9tZSBmb2xkZXJzIG9mIGEgcGFydGljdWxhciB1c2VyLiBUbyBtYWtlIGl0IGVhc2llciBmb3IgeW91IHRvIGludGVyYWN0IHdpdGggdGhlIGNvbW1hbmRzLCBzb21lIGFkZGl0aW9uYWwgcGFyYW1ldGVycyB3ZXJlIGFkZGVkLiA8YnIgLz48L2Rpdj48ZGl2PjxiciAvPjwvZGl2Pjx0YWJsZT48dGJvZHk+PHRyPjx0aD5Db21tYW5kPC90aD48dGg+RXhwbGFuYXRpb248L3RoPjwvdHI+PHRyPjx0ZD48aT5jeHMgLS11c2VyIDxiPnVzZXI8L2I+PC9pPjxiciAvPm9yPGJyIC8+PGk+Y3hzIC88Yj5wYXRoX3RvX2ZpbGVfb3JfZm9sZGVyPC9iPjwvaT48YnIgLz48L3RkPjx0ZD5Mb2NhdGlvbiB0byBzY2FuLiBJdCBjYW4gYmUgYSB1c2VyJ3MgaG9tZSBmb2xkZXIsIGEgZmlsZSBvciBhIGZvbGRlciBhbmQgYWxsIGl0cyByZWN1cnNpdmUgY29udGVudHMuPGJyIC8+PC90ZD48L3RyPjx0cj48dGQ+PGk+Y3hzIC0tdXNlciA8Yj51c2VyIDwvYj4tLWRicmVwb3J0IC0tcmVwb3J0IC9ob21lLzxiPnVzZXI8L2I+L2N4c19zY2FuLSQoZGF0ZSArJWJfJWRfJVlfJUhoJU1tKTwvaT48YnIgLz48L3RkPjx0ZD5TY2FuIHRoZSB1c2VyJ3MgaG9tZSBmb2xkZXIgd2l0aCBwbGFpbiB0ZXh0IGFuZCBjcmVhdGUgYSBkYXRhYmFzZSByZXBvcnQuPGJyIC8+PC90ZD48L3RyPjx0cj48dGQ+PGk+Y3hzIC0tdXNlciA8Yj51c2VyIDwvYj4tLXJlcG9ydCAiL2hvbWUvPGI+dXNlcjwvYj4vcmVwb3J0LSQoZGF0ZSArJWJfJWRfJVlfJUhoJU1tKS50eHQiIC1CIC0tbWFpbCA8Yj5lbWFpbEBkb21haW4uY29tPC9iPjwvaT48YnIgLz48L3RkPjx0ZD5SdW4gYSBmdWxsIHNjYW4gb2Ygb25lIGNQYW5lbCBhY2NvdW50IGluIHRoZSBiYWNrZ3JvdW5kLCBzYXZlIHRoZSByZXBvcnQgdG8gdGhlIHVzZXLigJlzIGhvbWUgZm9sZGVyLCBhbmQgc2VuZCBlbWFpbCB0byB0aGUgc3BlY2lmaWVkIG1haWxib3guPGJyIC8+PC90ZD48L3RyPjx0cj48dGQ+PGk+Y3hzIC0tZm9yY2UgLzxiPnBhdGhfdG9fc3lzdGVtX2ZvbGRlcjwvYj48L2k+PGJyIC8+PC90ZD48dGQ+U2NhbiBmaWxlIGluIHN5c3RlbSBmb2xkZXJzICh1c2Ugd2l0aCBjYXV0aW9uKS48YnIgLz48L3RkPjwvdHI+PC90Ym9keT48L3RhYmxlPjxkaXY+PGJyIC8+PC9kaXY+PGRpdj5UaGUgZnVsbCBsaXN0IG9mIHRoZSBjb21tb24gYWRkaXRpb25hbCBDWFMgcGFyYW1ldGVycyBjYW4gYmUgZm91bmQgYmVsb3c6PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48dGFibGU+PHRib2R5Pjx0cj48dGg+Q29tbWFuZDwvdGg+PHRoPkV4cGxhbmF0aW9uPC90aD48L3RyPjx0cj48dGQ+PGk+LS1yZXBvcnQgPGI+L3BhdGhfdG9fY3hzX3JlcG9ydDwvYj48L2k+PC90ZD48dGQ+U2F2ZSBhIGRldGFpbGVkIHNjYW4gcmVwb3J0IHRvIHRoZSBwcm92aWRlZCBsb2NhdGlvbi48L3RkPjwvdHI+PHRyPjx0ZD48aT4tQiwgLS1iYWNrZ3JvdW5kDQo8L2k+PC90ZD48dGQ+TGF1bmNoIHRoZSBzY2FuIGluIHRoZSBiYWNrZ3JvdW5kLiBCZXN0IHVzZWQgdG9nZXRoZXIgd2l0aCB0aGUgPGk+PGI+LS1yZXBvcnQ8L2I+PC9pPiBvcHRpb24uPC90ZD48L3RyPjx0cj48dGQ+PGk+LS1tYWlsIDxiPmFkbWluQGV4YW1wbGUuY29tPC9iPjwvaT48L3RkPjx0ZD5TZW5kIHJlcG9ydCB0byBlbWFpbCBvbmNlIHRoZSBzY2FuIGlzIG92ZXIuPC90ZD48L3RyPjx0cj48dGQ+PGk+LVQsIC0tdGhyb3R0bGUgPGI+W251bV0gPC9iPjwvaT48L3RkPjx0ZD5QdXQgc2NhbiBpbiBzbGVlcCBtb2RlIGlmIHRoZSBzZXJ2ZXIgbG9hZCBpcyBncmVhdGVyIHRoYW4gPGk+PGI+W251bV08L2I+PC9pPi48L3RkPjwvdHI+PHRyPjx0ZD48aT4tLWZvcmNlPC9pPjwvdGQ+PHRkPlNjYW4gdGhlIGZpbGUocykgaW4gc3lzdGVtIGZvbGRlcnMgKDxpPi91c3IgL3ZhciAvYmluIC9saWIgL2xpYjY0IC9ib290IC9ldGMgL3Byb2MgL3N5cyAvb3B0PC9pPikuPC90ZD48L3RyPjx0cj48dGQ+PGk+LS1kZWVwPC9pPjwvdGQ+PHRkPkEgZGVlcCBzY2FuIHRoYXQgc2VhcmNoZXMgZm9yIGFsbCBrbm93biBleHBsb2l0cyBpbiBhbGwgc2Nhbm5lZCBmaWxlcy4gSXQgdGFrZXMgc2lnbmlmaWNhbnRseSBsb25nZXIgdGhhbiBhIG5vcm1hbCBzY2FuIGJ1dCBjYW4gYmUgaGVscGZ1bCB3aGVuIGJhc2ljIHNjYW5zIGFyZSBub3QgYWJsZSB0byBsb2NhdGUgdmlydXNlcy9wYXR0ZXJuIG1hdGNoZXMuPC90ZD48L3RyPjx0cj48dGQ+PGk+LS1xdWFyYW50aW5lIDxiPi9wYXRoX3RvX3F1YXJhbnRpbmU8L2I+PC9pPjwvdGQ+PHRkPlB1dCBhbGwgZmlsZXMgdGhhdCB0cmlnZ2VyIGFueSBtYXRjaGVzIGR1cmluZyB0aGUgc2NhbnMgdG8gcXVhcmFudGluZS4gVXNlIHdpdGggY2F1dGlvbiBhcyBpdCBtYXkgYnJlYWsgcHJvZHVjdGlvbiB3ZWJzaXRlcy48L3RkPjwvdHI+PHRyPjx0ZD48aT4tLXF2aWV3IDxiPi9wYXRoL3RvL3F1YXJhbnRpbmUvPC9iPmN4c3VzZXI8Yj4vdXNlci9maWxlPC9iPjwvaT48L3RkPjx0ZD5WaWV3IHF1YXJhbnRpbmVkIGZpbGUuPC90ZD48L3RyPjx0cj48dGQ+PGk+LS1xcmVzdG9yZSA8Yj4vcGF0aC90by9xdWFyYW50aW5lLzwvYj5jeHN1c2VyPGI+L3VzZXIvZmlsZTwvYj48L2k+PC90ZD48dGQ+UmVzdG9yZSBxdWFyYW50aW5lZCBmaWxlLjwvdGQ+PC90cj48dHI+PHRkPjxpPi0tZmlsZW1heCA8Yj5bbnVtXTwvYj48L2k+PC90ZD48dGQ+TWF4aW11bSBhbW91bnQgb2YgZmlsZXMgdG8gc2NhbiBwZXIgZGlyZWN0b3J5LiBUaGUgZGVmYXVsdCBpcyAxMCwwMDAuIFVzZWZ1bCB3aGVuIHNjYW5uaW5nIG1hc3NpdmUgbWFpbCBmb2xkZXJzLjwvdGQ+PC90cj48L3Rib2R5PjwvdGFibGU+PGRpdj48YnIgLz48L2Rpdj48ZGl2PkNYUyBzdXBwb3J0cyBtYW55IG90aGVyIHBhcmFtZXRlcnMgdGhhdCBjYW4gYmUgY2hlY2tlZCBieSBydW5uaW5nIHRoZSBmb2xsb3dpbmcgY29tbWFuZHM6PGJyIC8+PGJyIC8+PHByZSBjbGFzcz0icHJldHR5cHJpbnQiPmN4cyAtLWhlbHA8L3ByZT48YnIgLz5PciA8YnIgLz48YnIgLz48cHJlIGNsYXNzPSJwcmV0dHlwcmludCI+Y3hzIC0taGVscCB8IGxlc3MgLVI8L3ByZT48YnIgLz5UaGV5IHByb3ZpZGUgYSBmdWxsIGxpc3Qgb2YgcG9zc2libGUgb3B0aW9ucyBhcyB3ZWxsIGFzIGEgZGV0YWlsZWQgZGVzY3JpcHRpb24gb2YgZWFjaC48L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+PGJyIC8+PHA+PGEgbmFtZT0ic2Nhbm5pbmciPjxiPlNjYW5uaW5nIHRoZSB3aG9sZSBzZXJ2ZXI8L2I+PC9hPjwvcD48YnIgLz5CZWZvcmUgc3RhcnRpbmcgdGhlIHNjYW4gZm9yIHRoZSB3aG9sZSBzZXJ2ZXIsIGZpcnN0IGFkanVzdCB0aGUgQ1hTIGlnbm9yZSBsaXN0LCBzaW5jZSB0aGVyZSBhcmUgc29tZSBzdGFuZGFyZCBjUGFuZWwgZmlsZXMgbG9jYXRlZCBpbiA8aT4vaG9tZTwvaT4gZm9sZGVyIHRoYXQgd2lsbCB0cmlnZ2VyIGZhbHNlLXBvc2l0aXZlIHJlc3VsdHMuIFRvIGRvIHRoaXMsIHJ1biB0aGUgZm9sbG93aW5nIGNvbW1hbmQ6PGJyIC8+PGJyIC8+PHByZSBjbGFzcz0icHJldHR5cHJpbnQiPmNhdCAmZ3Q7IH4vaWdub3JlbGlzdCAmbHQ7Jmx0O0VPRjxiciAvPi9ob21lL3ZpcnRmczxiciAvPi9ob21lLy5jcGNwYW48YnIgLz4vaG9tZS9jUGFuZWxJbnN0YWxsPGJyIC8+L2hvbWUvLmNwYW48YnIgLz4vaG9tZS8uY3Bhbm08YnIgLz4vaG9tZS9jcGVhc3lhcGFjaGU8YnIgLz4vaG9tZS9sYXRlc3Q8YnIgLz5FT0YNCjwvcHJlPjxiciAvPk5vdyB5b3UgY2FuIHN0YXJ0IHRoZSBzY2FuLiA8YnIgLz48YnIgLz5JbiBvcmRlciB0byBydW4gaXQgaW4gdGhlIGJhY2tncm91bmQsIHNhdmUgdGhlIHJlcG9ydCB0byB0aGU8aT4gL3Jvb3QvL2Z1bGxfc2VydmVyX3NjYW48L2k+IGZpbGUgYW5kIHNlbmQgYXMgYW4gZW1haWwgdG8geW91cnNlbGYgb25jZSBpdOKAmXMgb3ZlciwgdXNlIHRoZSBmb2xsb3dpbmcgY29tbWFuZDo8YnIgLz48YnIgLz48cHJlIGNsYXNzPSJwcmV0dHlwcmludCI+Y3hzIC9ob21lIC1CIC0tcmVwb3J0IC9yb290LzxiPmZ1bGxfc2VydmVyX3NjYW48L2I+IC0taWdub3JlIH4vaWdub3JlbGlzdCAtLW1haWwgPGI+ZW1haWxAZG9tYWluLmNvbTwvYj48L3ByZT48YnIgLz48L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+PHA+PGEgbmFtZT0ic3RvcmluZ19yZXBvcnRzIj48Yj5TdG9yaW5nIHNjYW4gcmVwb3J0cyBpbiB0aGUgZGF0YWJhc2U8L2I+PC9hPjwvcD48YnIgLz5Zb3UgY2FuIHJ1biBzY2FucyB3aXRoIHRoZSA8aT4tLWRicmVwb3J0IDwvaT5vcHRpb24gdG8gc3RvcmUgdGhlIHJlc3VsdHMgaW4gdGhlIGRhdGFiYXNlIGxvY2F0ZWQgYXQgPGk+L2V0Yy9jeHMvY3hzLmRiPC9pPi4gSXQgaGFzIGl0cyBkb3duc2lkZXMsIGxpa2UgdGhlIHdheSB0aW1lc3RhbXBzIGFyZSBoYW5kbGVkIGFuZCB0aGUgbW9yZSByYXJpZmllZCBmb3JtYXQgb2YgdGhlIGRhdGFiYXNlIChTUUxpdGUpLCBidXQgaXQgc3RpbGwgbWlnaHQgY29tZSBpbiBoYW5keS4gPGJyIC8+PGJyIC8+VGhlIGRldGFpbGVkIGluc3RydWN0aW9ucyBvbiBob3cgdG8gdXNlIGl0IGNhbiBiZSBmb3VuZCBiZWxvdy48YnIgLz48YnIgLz4xLiBGaW5kIHRoZSB0aW1lc3RhbXAgKGVwb2NoIGZvcm1hdCkgb2YgdGhlIHNjYW4gc3RhcnQ6PGJyIC8+PC9kaXY+PGJyIC8+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL2N4c192aWFfc3NoXzEucG5nIiAvPjxiciAvPjxiciAvPjxwcmUgY2xhc3M9InByZXR0eXByaW50Ij5kYXRlIC1kICc8Yj55b3VyIHRpbWVzdGFtcDwvYj4nICslczwvcHJlPjxiciAvPjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9jeHNfdmlhX3NzaF8yLnBuZyIgLz48YnIgLz48YnIgLz4yLiBDaGVjayB0aGUgc2NhbiB0aW1lIGluIHRoZSBzdW1tYXJ5IGFuZCBhZGQgdG8gaXQgdG8gdGhlIHN0YXJ0IG1vbWVudDo8YnIgLz48YnIgLz48aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvY3hzX3ZpYV9zc2hfMy5wbmciIC8+PGJyIC8+PGJyIC8+PHByZSBjbGFzcz0icHJldHR5cHJpbnQiPmVjaG8gJCgoPGI+dGltZXN0YW1wIDwvYj4rIDxiPnNjYW5fdGltZTwvYj4pKTwvcHJlPjxiciAvPjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9jeHNfdmlhX3NzaF80LnBuZyIgLz48YnIgLz48YnIgLz4zLiBFbnRlciB0aGUgZGF0YWJhc2U6PGJyIC8+PGJyIC8+PHByZSBjbGFzcz0icHJldHR5cHJpbnQiPnNxbGl0ZTMgL2V0Yy9jeHMvY3hzLmRiPC9wcmU+PGJyIC8+NC4gTG9jYXRlIHRoZSByZXBvcnQ6PGJyIC8+PGJyIC8+PHByZSBjbGFzcz0icHJldHR5cHJpbnQiPlNFTEVDVCAqIEZST00gcmVwb3J0cyBXSEVSRSB0aW1lc3RhbXAgPSAnPGI+dGltZXN0YW1wPC9iPic7PC9wcmU+PGJyIC8+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL2N4c192aWFfc3NoXzUucG5nIiAvPjxiciAvPjxiciAvPlNvbWV0aW1lcywgdGhlIHRpbWVzdGFtcCBvZiB0aGUgc2NhbiBpcyBvZmYgYnkgYSBzZWNvbmQgZGVwZW5kaW5nIG9uIHRoZSBleGFjdCBzdGFydCB0aW1lIG9mIHRoZSBzY2FuLiBZb3UgY2FuIGxvY2F0ZSBpdCBieSBjaGVja2luZyB0aGUgY2xvc2VzdCB0aW1lc3RhbXAgYXZhaWxhYmxlOjxiciAvPjxiciAvPjxwcmUgY2xhc3M9InByZXR0eXByaW50Ij5TRUxFQ1QgdGltZXN0YW1wIEZST00gcmVwb3J0czs8L3ByZT48YnIgLz48ZGl2PjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9jeHNfdmlhX3NzaF82LnBuZyIgLz48L2Rpdj48YnIgLz48YnIgLz48cD48YSBuYW1lPSJ3b3JraW5nIj48Yj5Xb3JraW5nIHdpdGggcXVhcmFudGluZWQgZmlsZXMgYW5kIGZhbHNlLXBvc2l0aXZlIHJlc3VsdHM8L2I+PC9hPjwvcD48YnIgLz48ZGl2PkFmdGVyIHBlcmZvcm1pbmcgYSBzY2FuLCB5b3UgbWF5IG5vdGljZSB0aGF0IHRoZSBDWFMgcXVhcmFudGluZWQgZmlsZXMgYXJlIG5vdCBtYWxpY2lvdXMuIEluIHRoaXMgY2FzZSwgaXTigJlzIG5lY2Vzc2FyeSB0byBjbG9zZWx5IGV4YW1pbmUgdGhlIGZpbGVz4oCZIGNvbnRlbnRzIGFuZCBkZWNpZGUgd2hldGhlciBvciBub3QgeW91IHNob3VsZCBtb2RpZnksIHdoaXRlbGlzdCwgb3Iga2VlcCB0aGVtIHF1YXJhbnRpbmVkLjwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PGJyIC8+PHVsPjxsaT48YSBuYW1lPSJ2aWV3aW5nIj48Yj5WaWV3aW5nIHF1YXJhbnRpbmVkIGZpbGVzPC9iPjwvYT48L2xpPjwvdWw+PGJyIC8+U3RhbmRhcmQgdGV4dCB2aWV3aW5nL2VkaXRpbmcgdG9vbHMgKGNhdCwgbGVzcy9tb3JlLCBldGMuKSBhbGxvd3MgeW91IHRvIHZpZXcvZWRpdCBjb250ZW50cyBvZiB0aGUgZmlsZSwgYnV0IGluIG9yZGVyIHRvIHNhZmVseSB2aWV3IGEgcXVhcmFudGluZWQgZmlsZSwgd2UgcmVjb21tZW5kIHVzaW5nIHRoZSBmb2xsb3dpbmcgY29tbWFuZDo8YnIgLz48YnIgLz48cHJlIGNsYXNzPSJwcmV0dHlwcmludCI+Y3hzIC0tcXZpZXcgPGI+L3BhdGgvdG8vcXVhcmFudGluZS88L2I+Y3hzdXNlcjxiPi91c2VyL21hbGljaW91c19maWxlPC9iPjwvcHJlPjxiciAvPjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9jeHNfdmlhX3NzaF83LnBuZyIgLz48YnIgLz48YnIgLz5JZiB0aGUgZmlsZSBpcyBsb2NhdGVkIGluIGEgc3lzdGVtIGZvbGRlciAoZS5nLiw8aT4gL29wdDwvaT4sIDxpPi9ldGM8L2k+LCBldGMuKSwgeW91IHdpbGwgbmVlZCB0byB1c2UgPGI+PGk+LS1mb3JjZTwvaT48L2I+IG9wdGlvbiB0byBiZSBhYmxlIHRvIHNjYW4gaXQ6PGJyIC8+PGJyIC8+PHByZSBjbGFzcz0icHJldHR5cHJpbnQiPmN4cyAtLWZvcmNlIDxiPi9wYXRoL3RvL3F1YXJhbnRpbmUvPC9iPmN4c3VzZXI8Yj4vdXNlci9tYWxpY2lvdXNfZmlsZTwvYj48L3ByZT48YnIgLz5BcyBhIHJlc3VsdCwgeW91IHdpbGwgc2VlIHRoZSBvdXRwdXQgdGhhdCBsb29rcyBhcyBmb2xsb3dzOjxiciAvPjxiciAvPjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9jeHNfdmlhX3NzaF84LnBuZyIgLz48YnIgLz48ZGl2PjxiciAvPjwvZGl2Pjx1bD48bGk+PGEgbmFtZT0iY29uc2lkZXJpbmciPjxiPkNvbnNpZGVyaW5nIHdoZXRoZXIgb3Igbm90IHRoZSBmaWxlIGlzIGRhbmdlcm91czwvYj48L2E+PC9saT48L3VsPjxiciAvPkluIG91ciBleGFtcGxlLCBpdOKAmXMgZWFzeSB0byBkZXRlY3QgdGhlIG1hbGljaW91cyBjb2RlOyBpdCBzdG9vZCBvdXQgZnJvbSB0aGUgbm9ybWFsIFBIUCBjb2RlIGFuZCB3ZSBoYWQgYWNjZXNzIHRvIHRoZSBjbGVhbiBtYXN0ZXIgdmVyc2lvbiAoc2luY2UgdGhlIGZpbGUgaXMgYSBwYXJ0IG9mIHBvcHVsYXIgV29yZFByZXNzIHBsdWdpbikuIDxiciAvPjxiciAvPkdlbmVyYWxseS1zcGVha2luZywgaG93ZXZlciwgdGhpcyBpcyB0aGUgaGFyZGVzdCBwYXJ0IGFzIG1hbGljaW91cyBjb2RlIGlzIG9mdGVuIG9iZnVzY2F0ZWQsIGVuY29kZWQgb3Igb3RoZXJ3aXNlIG5vdCByZWFkYWJsZSBieSBodW1hbnMuIER1ZSB0byB0aGUgZGl2ZXJzZSBuYXR1cmUgb2YgdGhlc2UgZXhwbG9pdHMsIGl04oCZcyBpbXBvc3NpYmxlIHRvIGNvdmVyIGFsbC4gVGhlcmVmb3JlLCB3ZSBjYW4gb25seSBhZHZpc2UgeW91IHRvOiA8YnIgLz48YnIgLz48dWw+PGxpPk5ldmVyIHJlc3RvcmUvd2hpdGVsaXN0IGZpbGVzIGlmIHlvdSBhcmUgbm90IHN1cmUgd2hhdCBoYXJtIHRoZXkgY2FuIGRvLjwvbGk+PGxpPldoaXRlbGlzdCBvbmx5IDxhIGhyZWY9Imh0dHBzOi8vZW4ud2lraXBlZGlhLm9yZy93aWtpL01ENSIgbGlua3RleHQ9Im1kNSBjaGVja3N1bXMiIGxpbmt0eXBlPSJDdXN0b20iIHRhcmdldD0iX2JsYW5rIj5tZDUgY2hlY2tzdW1zPC9hPiwgbm90IGZpbGVzIG9yIGZvbGRlcnMuIFRoaXMgd2F5IG9ubHkgb25lIHNwZWNpZmljIHN0YXRlIG9mIHRoZSBmaWxlIHdpbGwgYmUgd2hpdGVsaXN0ZWQgYW5kIGZ1cnRoZXIgbW9kaWZpY2F0aW9ucyB3aWxsIHRyaWdnZXIgQ1hTIGNoZWNrcyBvbmUgbW9yZSB0aW1lLiBPdGhlcndpc2UsIHVzZXJzIHdpbGwgYmUgYWJsZSB0byBwdXQgc29tZXRoaW5nIHRoYXQgYWZmZWN0cyB0aGUgd2hvbGUgc2VydmVyIGluIHRoYXQgbG9jYXRpb24sIGVpdGhlciBieSBtaXN0YWtlIG9yIGludGVudGlvbmFsbHksIGFuZCBhbnRpdmlydXMgd2lsbCBpZ25vcmUgaXQgY29tcGxldGVseS48L2xpPjwvdWw+PGJyIC8+PGJyIC8+PHVsPjxsaT48YSBuYW1lPSJyZXN0b3JhdGlvbiI+PGI+RmlsZSByZXN0b3JhdGlvbiBhbmQgd2hpdGVsaXN0IG1hbmFnZW1lbnQ8L2I+PC9hPjwvbGk+PC91bD48YnIgLz5JZiB5b3UgaGF2ZSBkZXRlY3RlZCBhbmQgcmVtb3ZlZCB0aGUgbWFsd2FyZSBwYXJ0IG9mIHRoZSBmaWxlLCB5b3UgbXVzdCBwcm9jZWVkIHdpdGggdGhlIHJlcXVpcmVkIHN0ZXBzOjxiciAvPjxiciAvPjEuIFJ1biBhbiBleHRyYSBzY2FuIHRvIG1ha2Ugc3VyZSB0aGF0IGZpbGUgaXMgbm93IHNhZmU6PGJyIC8+PGJyIC8+PHByZSBjbGFzcz0icHJldHR5cHJpbnQiPmN4cyAtLWZvcmNlIDxiPi9wYXRoL3RvL3F1YXJhbnRpbmUvPC9iPmN4c3VzZXIvdXNlcjxiPi9tYWxpY2lvdXNfZmlsZTwvYj48L3ByZT48YnIgLz48aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvY3hzX3ZpYV9zc2hfOS5wbmciIC8+PGJyIC8+PGJyIC8+Mi4gUmVzdG9yZSBpdDo8YnIgLz48YnIgLz48cHJlIGNsYXNzPSJwcmV0dHlwcmludCI+Y3hzIC0tcXJlc3RvcmUgPGI+L3BhdGgvdG8vcXVhcmFudGluZS88L2I+Y3hzdXNlcjxiPi91c2VyL21hbGljaW91c19maWxlPC9iPjwvcHJlPjxiciAvPjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9jeHNfdmlhX3NzaF8xMC5wbmciIC8+PGJyIC8+PGJyIC8+SWYgaXTigJlzIG5vdCBwb3NzaWJsZSB0byBkZXRlcm1pbmUgd2h5IHRoZSBDWFMgdHJlYXRlZCB0aGUgZmlsZSBhcyBtYWxpY2lvdXMsIGJ1dCB5b3UgYXJlIHN1cmUgdGhhdCBpdCBpcyBzYWZlIHRvIHVzZSBpdCwgZm9sbG93IHRoZSBuZXh0IHN0ZXBzOjxiciAvPjxiciAvPjEuIEZpbmQgb3V0IE1ENSBzdW0gb2YgdGhlIGZpbGUuPGJyIC8+PGJyIC8+PHByZSBjbGFzcz0icHJldHR5cHJpbnQiPm1kNXN1bSA8Yj4vcGF0aC90by9xdWFyYW50aW5lLzwvYj5jeHN1c2VyPGI+L3VzZXIvbWFsaWNpb3VzX2ZpbGU8L2I+PC9wcmU+PGJyIC8+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL2N4c192aWFfc3NoXzExLnBuZyIgLz48YnIgLz48YnIgLz4yLiBBZGQgbWQ1c3VtIHRvIHdoaXRlbGlzdDo8YnIgLz48YnIgLz48cHJlIGNsYXNzPSJwcmV0dHlwcmludCI+ZWNobyDigJxtZDVzdW06PGI+bWQ1c3VtX2Zyb21fcHJldmlvdXNfY29tbWFuZDwvYj7igJ0gJmd0OyZndDsgL2V0Yy9jeHMvY3hzLmlnbm9yZS51c2VyPC9wcmU+PGJyIC8+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL2N4c192aWFfc3NoXzEyLnBuZyIgLz48YnIgLz48YnIgLz4zLiBSZXN0b3JlIHRoZSBmaWxlOjxiciAvPjxiciAvPjxwcmUgY2xhc3M9InByZXR0eXByaW50Ij5jeHMgLS1xcmVzdG9yZSA8Yj4vcGF0aC90by9xdWFyYW50aW5lLzwvYj5jeHN1c2VyPGI+L3VzZXIvbWFsaWNpb3VzX2ZpbGU8L2I+PC9wcmU+PGJyIC8+NC4gUmVzdGFydCBDWFM6PGJyIC8+PGJyIC8+PHByZSBjbGFzcz0icHJldHR5cHJpbnQiPnNlcnZpY2UgY3hzd2F0Y2ggcmVzdGFydDwvcHJlPjxiciAvPm9yIDxiciAvPjxiciAvPjxwcmUgY2xhc3M9InByZXR0eXByaW50Ij5zeXN0ZW1jdGwgcmVzdGFydCBjeHN3YXRjaC5zZXJ2aWNlPC9wcmU+PGJyIC8+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL2N4c192aWFfc3NoXzEzLnBuZyIgLz48YnIgLz48YnIgLz48YnIgLz48ZGl2PjxiciAvPjwvZGl2PjxkaXY+Q29uZ3JhdHMhIE5vdyB5b3Uga25vdyBob3cgcG93ZXJmdWwgdGhlIENvbmZpZ1NlcnZlciBFeHBsb2l0IFNjYW5uZXIgKENYUykgdG9vbCBjYW4gYmUsIGhlbHBpbmcgeW91IHRvIGVmZmVjdGl2ZWx5IHNlY3VyZSB5b3VyIHNlcnZlci4gPGJyIC8+PC9kaXY+","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"2025-08-18T07:58:53.0000000","LiveDateTime":"1754-02-02T00:00:00.0000000","CreatedDateTime":"2019-05-30T08:26:10.0000000","ApprovalDatetime":"2019-05-30T10:13:12.0000000","RequestCount":29666,"MarkedAsNew":false,"MarkedAsFeatured":false,"RatingValue":0,"CategoryPaths":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":1,"CategoryId":12,"CategoryName":"Hosting"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":2,"CategoryId":89,"CategoryName":"SSH Access"}],"AssociatedCategories":[{"CategoryId":89,"CategoryName":"SSH Access","CategoryDisplayName":"HostingSSH Access"}],"AssociatedTags":[{"TagId":18755,"Tag":" ssh"},{"TagId":27348,"Tag":"cxs"}],"RelatedArticles":[],"AssociatedMedias":[],"PreferredCategoryId":0,"RootParentCategoryName":"","RootParentCategoryId":0},"status":200,"statusText":"OK"},"/api/v1/ncpl/simplekb/getcategorybycategoryid:\"{\\\"categoryId\\\":89}\"":{"body":{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryDto","Description":"VGhlc2UgYXJ0aWNsZXMgZGVzY3JpYmUgYmFzaWMgc3RlcHMgcmVxdWlyZWQgdG8gYWNjZXNzIHlvdXIgaG9zdGluZyBhY2NvdW50IHVzaW5nIHRoZSBzZWN1cmUgU1NIIGNvbm5lY3Rpb24uIEhlcmUgeW91IGNhbiBmaW5kIHRoZSBleGFtcGxlcyBvZiB1c2luZyB0aGUgbW9zdCB3aWRlbHkgdXNlZCBsaW51eCBjb21tYW5kcy48YnIgLz4=","ParentCategoryId":12,"Parent_Category_Name":"Hosting","FriendlyId":null,"ApprovedYN":true,"TreatAsTopicYN":false,"CreatedDateTime":"11/13/2010 09:44:40","CurrentCategoryPaths":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":1,"CategoryId":12,"CategoryName":"Hosting"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":2,"CategoryId":89,"CategoryName":"SSH Access"}],"RelatedCategories":[],"AssociatedArticles":[{"ArticleId":1015,"Title":"How to find information about commands","ArticleName":"How to find information about commands","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/26/2024"},{"ArticleId":10123,"Title":"Using CXS scan via SSH","ArticleName":"Using CXS scan via SSH","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"08/18/2025"},{"ArticleId":10200,"Title":"How to secure your SSH login","ArticleName":"How to secure your SSH login","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"04/26/2024"},{"ArticleId":1007,"Title":"What is SSH?","ArticleName":"What is SSH?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":131,"Title":"Do you provide SSH? If yes, under what conditions?","ArticleName":"Do you provide SSH? If yes, under what conditions?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"07/19/2024"},{"ArticleId":1022,"Title":"How to get an SSH client","ArticleName":"How to get an SSH client","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/05/2019"},{"ArticleId":1016,"Title":"How to access a hosting account via SSH","ArticleName":"How to access a hosting account via SSH","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/25/2024"},{"ArticleId":9428,"Title":"How to connect via SSH using keys","ArticleName":"How to connect via SSH using keys","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/09/2025"},{"ArticleId":1020,"Title":"How to create a new file","ArticleName":"How to create a new file","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":1021,"Title":"How to edit a file","ArticleName":"How to edit a file","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":9571,"Title":"How to download a file via SSH","ArticleName":"How to download a file via SSH","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"12/15/2021"},{"ArticleId":1012,"Title":"How to remove a file","ArticleName":"How to remove a file","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":1019,"Title":"How to create a new directory","ArticleName":"How to create a new directory","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":1018,"Title":"How to change a working directory","ArticleName":"How to change a working directory","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":1013,"Title":"How to remove a directory","ArticleName":"How to remove a directory","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/12/2015"},{"ArticleId":1010,"Title":"How to find a current working directory","ArticleName":"How to find a current working directory","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":1017,"Title":"How to get a list of files and directories","ArticleName":"How to get a list of files and directories","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":1011,"Title":"How to change permissions for files and directories","ArticleName":"How to change permissions for files and directories","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/25/2024"},{"ArticleId":9606,"Title":"How to create a backup of your files via SSH","ArticleName":"How to create a backup of your files via SSH","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"12/21/2021"},{"ArticleId":9184,"Title":"How to import and export a database via SSH","ArticleName":"How to import and export a database via SSH","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"04/29/2025"},{"ArticleId":1249,"Title":"How to remotely connect to a MySQL database located on our shared server","ArticleName":"How to remotely connect to a MySQL database located on our shared server","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"12/02/2021"},{"ArticleId":9586,"Title":"How to deal with Git on our Shared servers","ArticleName":"How to deal with Git on our Shared servers","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/27/2019"},{"ArticleId":1008,"Title":"SCP and SFTP - Secure File Transfer Using SSH","ArticleName":"SCP and SFTP - Secure File Transfer Using SSH","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"}],"AssociatedTags":[],"CategoryId":89,"CategoryName":"SSH Access"},"status":200,"statusText":"OK"},"/api/v1/ncpl/simplekb/getcategories:\"{\\\"parentCategoryId\\\":0,\\\"getTree\\\":true}\"":{"body":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2216,"CategoryName":"Spam Protection"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2217,"CategoryName":"Renewal"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2218,"CategoryName":"cPanel SSL Plugin"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2219,"CategoryName":"PHP Configuration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2221,"CategoryName":"Multi-Domain SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2222,"CategoryName":"Cancellation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2223,"CategoryName":"Browser errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2224,"CategoryName":"Site Seal, Logo"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2225,"CategoryName":"SEO"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2226,"CategoryName":"Email Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2227,"CategoryName":"SSL Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/cloud-red.png","ShortDesc":"","CategoryId":2228,"CategoryName":"Apps","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2251,"CategoryName":"Supersonic CDN"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2298,"CategoryName":"Site Maker"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":177,"CategoryName":"Google Workspace (formerly G Suite)"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2229,"CategoryName":"Hosting Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2232,"CategoryName":"DNSSEC"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2234,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2237,"CategoryName":"Host records setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2238,"CategoryName":"SSL installation errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/easywp-red.png","ShortDesc":"","CategoryId":2239,"CategoryName":"EasyWP","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2280,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2279,"CategoryName":"General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2281,"CategoryName":"WordPress Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2282,"CategoryName":"Plugins and Themes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2284,"CategoryName":"WordPress Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2285,"CategoryName":"SFTP and Database access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2286,"CategoryName":"Domains questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2288,"CategoryName":"Billing questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2287,"CategoryName":"SSL questions"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2251,"CategoryName":"Supersonic CDN"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2252,"CategoryName":"InterWorx questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2254,"CategoryName":"Domains How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2255,"CategoryName":"Hosting How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2257,"CategoryName":"Sales & Payments How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2258,"CategoryName":"cPanel Email How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2260,"CategoryName":"Private Email Contacts and Calendars Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2262,"CategoryName":"EasyWP How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"https://download.namecheap.com/assets/img/domainvault-red@2x.png","ShortDesc":"","CategoryId":2289,"CategoryName":"Domain Vault","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2290,"CategoryName":"CSR code"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2291,"CategoryName":"Webuzo questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2292,"CategoryName":"Browser Extensions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2293,"CategoryName":"Automated SSL management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2298,"CategoryName":"Site Maker"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":27,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/support-red.png","ShortDesc":"","CategoryId":5,"CategoryName":"General & Support","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":7,"CategoryName":"Billing FAQ"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":8,"CategoryName":"Transfer Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":22,"CategoryName":"Hosting Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":38,"CategoryName":"SSL General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":45,"CategoryName":"Account Security"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":46,"CategoryName":"Domain Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":63,"CategoryName":"Namecheap API"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":177,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2179,"CategoryName":"Private Email: General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2274,"CategoryName":"General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2280,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2279,"CategoryName":"General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2215,"CategoryName":"Private Email: Mailbox Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2196,"CategoryName":"WHMCS module for SSL"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/savings-red.png","ShortDesc":"","CategoryId":2200,"CategoryName":"Checkout & Billing","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":7,"CategoryName":"Billing FAQ"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2201,"CategoryName":"Domains Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":21,"CategoryName":"Hosting Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":71,"CategoryName":"SSL Certificates Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2177,"CategoryName":"Private Email"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2201,"CategoryName":"Domains Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":67,"CategoryName":"Activation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":83,"CategoryName":"Transfer to Namecheap"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":43,"CategoryName":"Profile Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":10,"CategoryName":"DNS Questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":29,"CategoryName":"cPanel questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":21,"CategoryName":"Hosting Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":11,"CategoryName":"Dynamic DNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":44,"CategoryName":"Account Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":84,"CategoryName":"Transfer to another provider"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":68,"CategoryName":"Validation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2182,"CategoryName":"cPanel: Software Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2214,"CategoryName":"Email Forwarding"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2270,"CategoryName":"Routers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2281,"CategoryName":"WordPress Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2282,"CategoryName":"Plugins and Themes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2272,"CategoryName":"TV"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2187,"CategoryName":"cPanel: WordPress"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":219,"CategoryName":"Canceled Transfers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":71,"CategoryName":"SSL Certificates Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2176,"CategoryName":"Private Email: DNS Settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":69,"CategoryName":"Installation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/reseller-red.png","ShortDesc":"","CategoryId":34,"CategoryName":"Domains","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2232,"CategoryName":"DNSSEC"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2234,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2237,"CategoryName":"Host records setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":46,"CategoryName":"Domain Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":10,"CategoryName":"DNS Questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":11,"CategoryName":"Dynamic DNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":35,"CategoryName":"Registrations"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2207,"CategoryName":"Renewal questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":36,"CategoryName":"Domains with extended attributes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":51,"CategoryName":"FreeDNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":15,"CategoryName":"Namecheap Market"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2208,"CategoryName":"3rd Party Services Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2278,"CategoryName":"Handshake TLDs"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":35,"CategoryName":"Registrations"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":70,"CategoryName":"Reissuance"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/protection-red.png","ShortDesc":"","CategoryId":37,"CategoryName":"Domain Privacy Protection","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2177,"CategoryName":"Private Email"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2178,"CategoryName":"Private Email: Webmail Features"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2207,"CategoryName":"Renewal questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2210,"CategoryName":"cPanel Add-ons"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2273,"CategoryName":"Gaming Consoles"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2284,"CategoryName":"WordPress Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2285,"CategoryName":"SFTP and Database access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2268,"CategoryName":"macOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2175,"CategoryName":"Private Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/status-red.png","ShortDesc":"","CategoryId":2209,"CategoryName":"Domain Transfers","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":8,"CategoryName":"Transfer Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":83,"CategoryName":"Transfer to Namecheap"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":84,"CategoryName":"Transfer to another provider"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":219,"CategoryName":"Canceled Transfers"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":48,"CategoryName":"VPS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":36,"CategoryName":"Domains with extended attributes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/server-red.png","ShortDesc":"","CategoryId":12,"CategoryName":"Hosting","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2219,"CategoryName":"PHP Configuration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2225,"CategoryName":"SEO"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2252,"CategoryName":"InterWorx questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2291,"CategoryName":"Webuzo questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":27,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":22,"CategoryName":"Hosting Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":29,"CategoryName":"cPanel questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2182,"CategoryName":"cPanel: Software Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2187,"CategoryName":"cPanel: WordPress"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2210,"CategoryName":"cPanel Add-ons"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":48,"CategoryName":"VPS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2188,"CategoryName":"Dedicated Server"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":30,"CategoryName":"WHM questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":32,"CategoryName":"DNS settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":103,"CategoryName":"LVE (CloudLinux)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":89,"CategoryName":"SSH Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":205,"CategoryName":"FTP questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2180,"CategoryName":"MySQL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2199,"CategoryName":"Hosting Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2194,"CategoryName":"Tips & Tricks"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":239,"CategoryName":"WHMCS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":33,"CategoryName":"SSL Installation"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2171,"CategoryName":"Private Email: Active Sync (Exchange) Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2188,"CategoryName":"Dedicated Server"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2269,"CategoryName":"iOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2286,"CategoryName":"Domains questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2288,"CategoryName":"Billing questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2271,"CategoryName":"Linux"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":30,"CategoryName":"WHM questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":31,"CategoryName":"cPanel Email FAQs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":51,"CategoryName":"FreeDNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/email-red.png","ShortDesc":"","CategoryId":93,"CategoryName":"Email service","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2216,"CategoryName":"Spam Protection"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2226,"CategoryName":"Email Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2260,"CategoryName":"Private Email Contacts and Calendars Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2179,"CategoryName":"Private Email: General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2215,"CategoryName":"Private Email: Mailbox Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2214,"CategoryName":"Email Forwarding"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2176,"CategoryName":"Private Email: DNS Settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2178,"CategoryName":"Private Email: Webmail Features"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2175,"CategoryName":"Private Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2171,"CategoryName":"Private Email: Active Sync (Exchange) Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":31,"CategoryName":"cPanel Email FAQs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2186,"CategoryName":"cPanel Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2204,"CategoryName":"Private Email: Video Overview"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":32,"CategoryName":"DNS settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":15,"CategoryName":"Namecheap Market"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2186,"CategoryName":"cPanel Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2266,"CategoryName":"Windows"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2287,"CategoryName":"SSL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2267,"CategoryName":"Android"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2208,"CategoryName":"3rd Party Services Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2204,"CategoryName":"Private Email: Video Overview"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/security-red.png","ShortDesc":"","CategoryId":14,"CategoryName":"SSL Certificates","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2217,"CategoryName":"Renewal"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2218,"CategoryName":"cPanel SSL Plugin"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2221,"CategoryName":"Multi-Domain SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2222,"CategoryName":"Cancellation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2223,"CategoryName":"Browser errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2224,"CategoryName":"Site Seal, Logo"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2238,"CategoryName":"SSL installation errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2290,"CategoryName":"CSR code"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2293,"CategoryName":"Automated SSL management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":38,"CategoryName":"SSL General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":67,"CategoryName":"Activation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":68,"CategoryName":"Validation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":69,"CategoryName":"Installation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":70,"CategoryName":"Reissuance"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/performance-red.png","ShortDesc":"","CategoryId":9,"CategoryName":"My Account","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":45,"CategoryName":"Account Security"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":43,"CategoryName":"Profile Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":44,"CategoryName":"Account Access"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2278,"CategoryName":"Handshake TLDs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":103,"CategoryName":"LVE (CloudLinux)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/affiliates-red.png","ShortDesc":"","CategoryId":55,"CategoryName":"Affiliates","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":89,"CategoryName":"SSH Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/tools-red.png","ShortDesc":"","CategoryId":2211,"CategoryName":"API & Resellers","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2227,"CategoryName":"SSL Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2229,"CategoryName":"Hosting Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":63,"CategoryName":"Namecheap API"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2196,"CategoryName":"WHMCS module for SSL"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/timer-red.png","ShortDesc":"","CategoryId":2212,"CategoryName":"Legacy Products","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":205,"CategoryName":"FTP questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2180,"CategoryName":"MySQL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2199,"CategoryName":"Hosting Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/premiumdns-red.png","ShortDesc":"","CategoryId":2231,"CategoryName":"PremiumDNS","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2194,"CategoryName":"Tips & Tricks"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"https://static.nc-img.com/live-resource/icons/knowledgebase/fastVPN_icon-150px.png","ShortDesc":"","CategoryId":2265,"CategoryName":"FastVPN","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2292,"CategoryName":"Browser Extensions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2274,"CategoryName":"General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2270,"CategoryName":"Routers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2272,"CategoryName":"TV"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2273,"CategoryName":"Gaming Consoles"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2268,"CategoryName":"macOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2269,"CategoryName":"iOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2271,"CategoryName":"Linux"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2266,"CategoryName":"Windows"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2267,"CategoryName":"Android"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":239,"CategoryName":"WHMCS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":33,"CategoryName":"SSL Installation"}],"status":200,"statusText":"OK"}}Important locations and configurations
| Location | Explanation |
|---|---|
| /etc/cxs | Main directory; most files to work with are located here. |
| /etc/cxs/cxs.fp | Fingerprint database. |
| /etc/cxs/cxs.db | Report and counter storage. |
| /etc/cxs/default | Examples of configuration files/crons. |
| /etc/cxs/cxs.ignore* | Ignore lists for different types of scans. |
| /etc/cxs/cxscgi.sh /etc/cxs/cxsdaily.sh /etc/cxs/cxsftp.sh | Sets of options used for corresponding scans. |
| /opt/cxs/quarantine | CXS quarantine. |
| /var/log/cxswatch.log | Main log of the cxswatch system daemon. |
| /etc/cxs/cxswatch.sh | File launched by cxswatch daemon. With options provided in it CXS runs in mode that scans files uploaded to the server. If you supply --mail option here, it will send reports of all cxswatch scans to that mailbox. |
| Command | Explanation |
|---|---|
| cxs --user user or cxs /path_to_file_or_folder | Location to scan. It can be a user's home folder, a file or a folder and all its recursive contents. |
| cxs --user user --dbreport --report /home/user/cxs_scan-$(date +%b_%d_%Y_%Hh%Mm) | Scan the user's home folder with plain text and create a database report. |
| cxs --user user --report "/home/user/report-$(date +%b_%d_%Y_%Hh%Mm).txt" -B --mail email@domain.com | Run a full scan of one cPanel account in the background, save the report to the user’s home folder, and send email to the specified mailbox. |
| cxs --force /path_to_system_folder | Scan file in system folders (use with caution). |
| Command | Explanation |
|---|---|
| --report /path_to_cxs_report | Save a detailed scan report to the provided location. |
| -B, --background | Launch the scan in the background. Best used together with the --report option. |
| --mail admin@example.com | Send report to email once the scan is over. |
| -T, --throttle [num] | Put scan in sleep mode if the server load is greater than [num]. |
| --force | Scan the file(s) in system folders (/usr /var /bin /lib /lib64 /boot /etc /proc /sys /opt). |
| --deep | A deep scan that searches for all known exploits in all scanned files. It takes significantly longer than a normal scan but can be helpful when basic scans are not able to locate viruses/pattern matches. |
| --quarantine /path_to_quarantine | Put all files that trigger any matches during the scans to quarantine. Use with caution as it may break production websites. |
| --qview /path/to/quarantine/cxsuser/user/file | View quarantined file. |
| --qrestore /path/to/quarantine/cxsuser/user/file | Restore quarantined file. |
| --filemax [num] | Maximum amount of files to scan per directory. The default is 10,000. Useful when scanning massive mail folders. |
cxs --help
cxs --help | less -R
cat > ~/ignorelist <<EOF
/home/virtfs
/home/.cpcpan
/home/cPanelInstall
/home/.cpan
/home/.cpanm
/home/cpeasyapache
/home/latest
EOF
cxs /home -B --report /root/full_server_scan --ignore ~/ignorelist --mail email@domain.com
Storing scan reports in the database
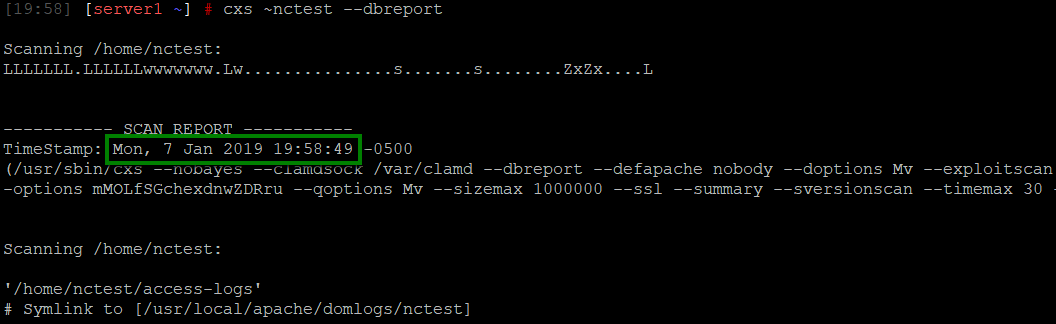
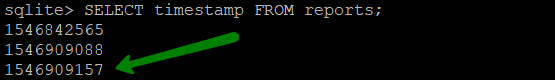
date -d 'your timestamp' +%s
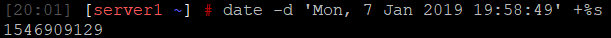
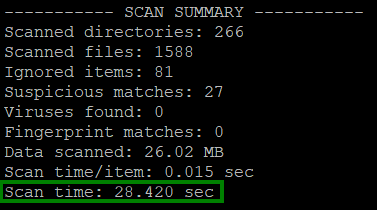
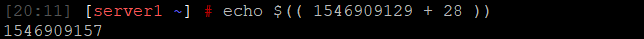
echo $((timestamp + scan_time))
sqlite3 /etc/cxs/cxs.db
SELECT * FROM reports WHERE timestamp = 'timestamp';
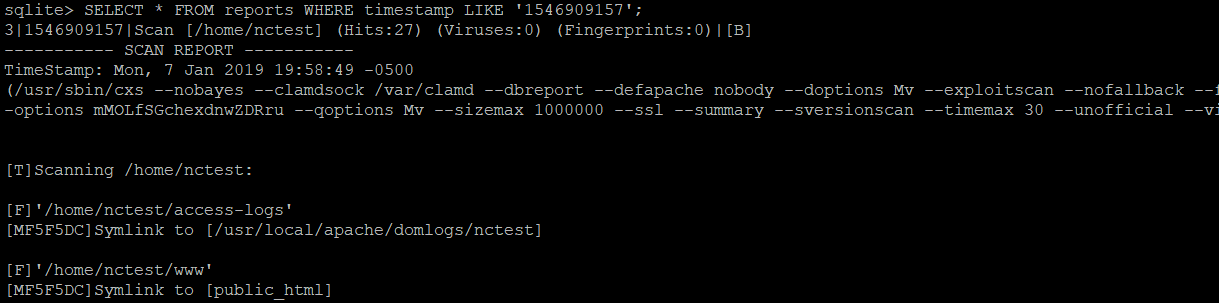
SELECT timestamp FROM reports;
Working with quarantined files and false-positive results
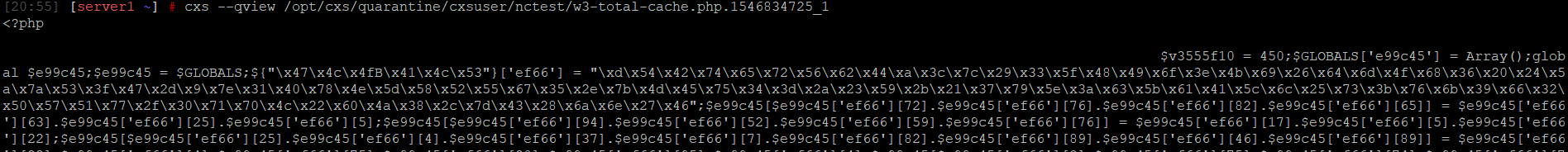
cxs --qview /path/to/quarantine/cxsuser/user/malicious_file
cxs --force /path/to/quarantine/cxsuser/user/malicious_file
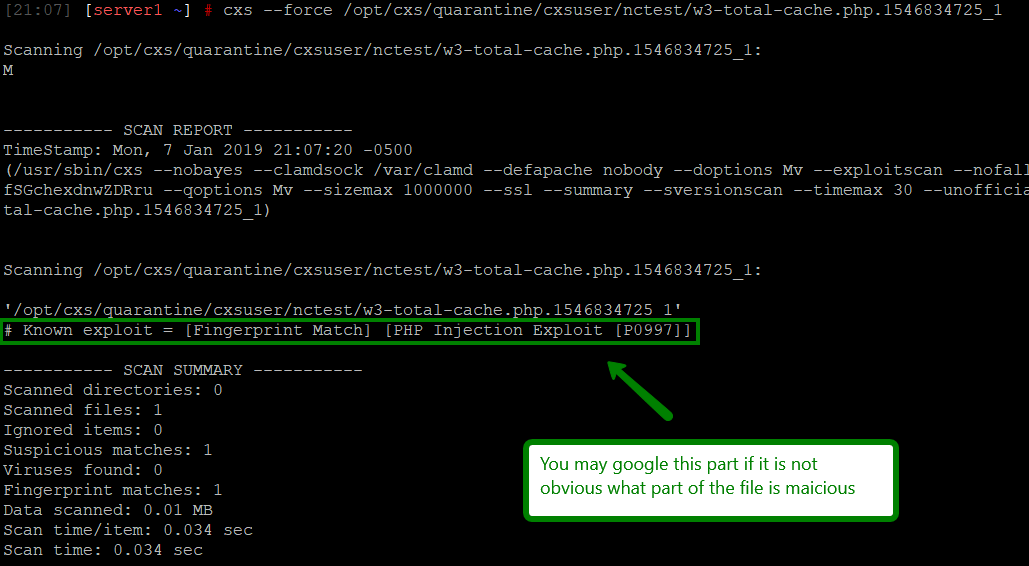
cxs --force /path/to/quarantine/cxsuser/user/malicious_file
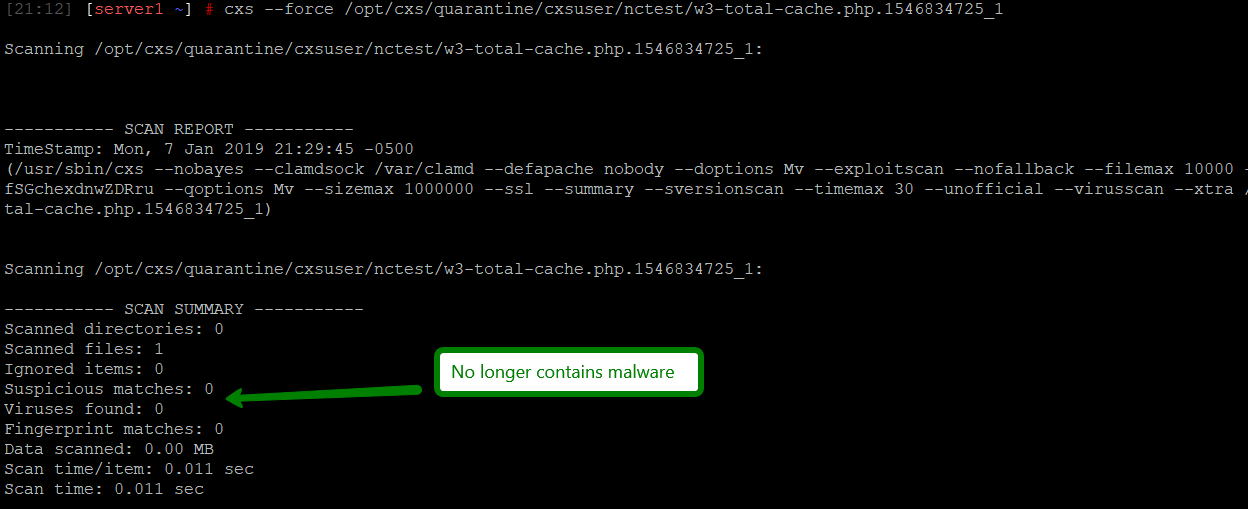
cxs --qrestore /path/to/quarantine/cxsuser/user/malicious_file
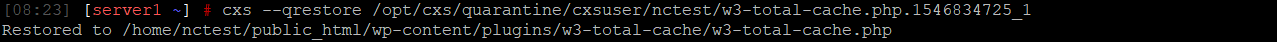
md5sum /path/to/quarantine/cxsuser/user/malicious_file
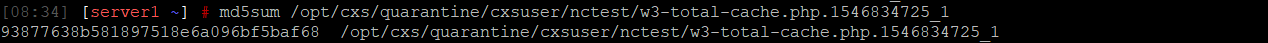
echo “md5sum:md5sum_from_previous_command” >> /etc/cxs/cxs.ignore.user
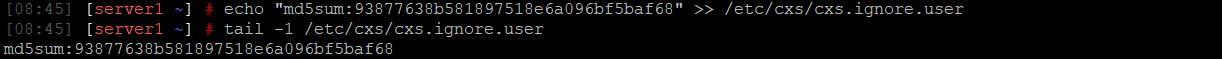
cxs --qrestore /path/to/quarantine/cxsuser/user/malicious_file
service cxswatch restart
systemctl restart cxswatch.service
Need help? We're always here for you.